To strike fear into the heart of a security or risk manager, just utter one word: Ransomware.
After countless headlines and costs of over 11.5 billion dollars in 2019 alone, organizations around the world are understandably terrified of being hit by a ransomware attack.
But here’s the thing. For a well-prepared organization, ransomware poses a very manageable risk.
In this article, we’ll explain what ransomware is, look at a high-profile example, and cover the most important steps you can take to protect your organization.
What is Ransomware?
Very simply, ransomware is a type of malicious software that restricts access to digital assets and demands a ransom in exchange for their safe return. Ransoms are usually requested in Bitcoin and range from a few hundred dollars to hundreds of thousands of dollars.
There are three types of ransomware:
-
Locking ransomware restricts access to an entire device (usually a smartphone or tablet).
-
Crypto ransomware uses encryption to restrict access to files and folders.
-
Wiper ransomware often poses as crypto ransomware, but is really used to ‘wipe’ the hard drives of infected systems. Although a ransom is often demanded, there is no way to recover encrypted files.
While locking ransomware can be disruptive, crypto and wiper ransomware are far greater threats to organizations because they are harder to recover from. This article will focus mainly on crypto ransomware as it is most prevalent in the wild today.
Crypto ransomware uses cryptovirology techniques to encrypt files in a way that is functionally impossible for anybody but the attacker to decrypt. The technical details of this process are beyond the scope of this article, but you can find a brief overview and some examples here.
The headline is simply this: If your organization is hit by ransomware and you don’t have a recovery plan in place, the damage can be catastrophic.
Ransomware in the Real World
To understand how damaging a ransomware attack can be, it’s worth looking at a real-world example. And what better case than the globally-renowned (and reviled) WannaCry, which infected more than 250 thousand devices across 150 countries… all within a matter of days.
This extreme replication rate made WannaCry — an otherwise unremarkable ransomware variant — a global phenomenon, causing an estimated $4 billion in damages. Previous ransomware variants had spread mainly through social engineering tactics like phishing, vishing, and malvertising. By contrast, WannaCry was able to spread itself in a way similar to ‘computer worms’ like Conficker and Nimda.
Once a device was infected with WannaCry, all of the usual things happened: the virus set about encrypting every file it could find, and ultimately displayed a ransom message.
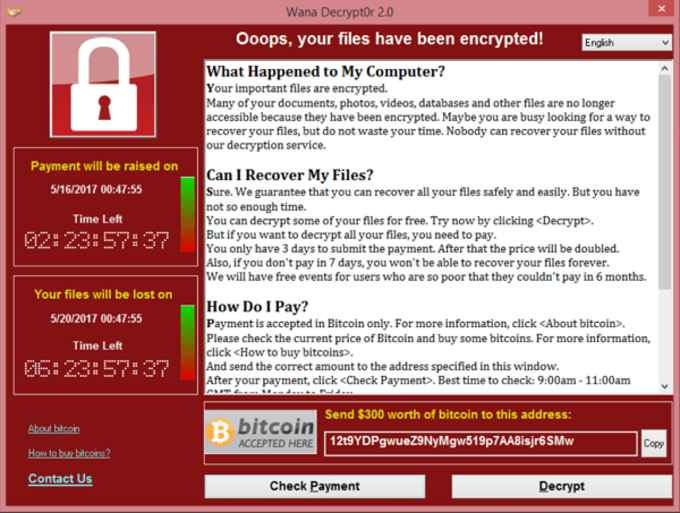
The ransoms demanded by WannaCry were quite low, typically falling in the $300 — $600 range. Despite this (and the huge number of devices infected), the threat actors responsible made only around $140,000 — much less than other prominent ransomware families.
Why? Because for many organizations, the sheer number of devices infected made paying the ransom cost-prohibitive.
Instead, they had two options:
-
Restore their encrypted files from backups
-
Try to move forward without the lost files
Let’s be honest, no organization wants to find itself in this position.
Now for an important piece of context about the WannaCry case. One of the factors that made WannaCry possible was MS17–010, a vulnerability in Microsoft’s Server Message Block (SMB) protocol. But MS17–010 wasn’t an unknown vulnerability at the time WannaCry was released. In fact, Microsoft had issued a patch and a critical alert for all supported Windows operating systems more than two months earlier.
There are two things to note here:
First, only organizations running the long out-of-support OS Windows XP were in the position of not having an available patch that would have prevented their systems from being infected by WannaCry. Sadly, a large number of organizations were still running Windows XP on at least some devices at the time, making them highly vulnerable.
Second, a huge number of devices affected by WannaCry weren’t running Windows XP. They simply hadn’t been patched. Despite Microsoft issuing a patch (and a critical alert) two months earlier, many organizations had not yet patched MS17–010.
4 Steps to Prevent Ransomware
Benjamin Franklin famously warned: “An ounce of prevention is worth a pound of cure.”
He was talking about fire safety, but the quote applies equally to ransomware. Having a plan to recover from ransomware is important, but preventing it altogether is the best option. Thankfully, it’s not as hard as you might think.
Ransomware prevention can be boiled down to four steps:
Step 1: Understand Your Environment
Business networks can be horrifyingly complex, with thousands of unique devices, applications, and services running at any time. Since any weakness is a potential entry point for an attacker, the first step in preventing ransomware is knowing exactly what’s going on in your environment.
Service enumeration is critical here. Generally, this involves using an automated scanner to identify everything connected to a network, along with any known vulnerabilities or weaknesses associated with those assets.
Step 2: Patching and General Security Hygiene
The world of cybersecurity is awash with exciting new products and cutting-edge technology. But if your ‘house’ isn’t in order, none of that will help.
Unpatched or out-of-date assets provide the easiest entry points for threat actors. So now that you have a deep understanding of your environment, the next step is to ensure all of the mundane, business-as-usual security processes are in place.
#1 on that list is patching.
Are all of your applications and services up-to-date? Is everything properly configured? Have all known vulnerabilities been patched? If the answer to any of these questions is no, fixing that should be your starting point. Naturally, this is an ongoing process, since new vulnerabilities are continually identified and new patches developed.
Once you’re happy that a strong patching process is in place, the next stage is regular penetration testing. Penetration tests will uncover any additional vulnerabilities, misconfigurations, or security holes in your network that could be exploited by a threat actor.
Once you have a process in place to find and resolve these weaknesses, you’re ready for step three.
Step 3: Backups
There is only one guaranteed way to recover from ransomware: Restore encrypted files and folders from a recent backup.
“What about paying the ransom,” you ask?
In many cases, the encryption keys provided by threat actors simply don’t work. In some cases, crypto ransomware variants have been specifically designed to make decrypting files impossible, even for the attacker.
Backups, then, are the only way. And they have one huge advantage: If you can recover internally using your own backups, there’s no external cost to the recovery effort. There are, however, some things to keep in mind:
-
Backups must be taken regularly, so minimal data is lost in the event of a ransomware attack.
-
Live/continuous backups are not a good idea, because if backup media is connected to live systems it could be infected by ransomware. Similarly, unencrypted files could be overwritten by encrypted files during the backup process.
-
Ideally, backups should be stored securely on a separate physical site, and never connected directly to the Internet.
-
Test backups regularly and have a plan for how you’ll recover in the event of a ransomware attack. You wouldn’t believe how many organizations have tried to restore from a backup, only to discover it was corrupted or incomplete.
Keep in mind that the ‘perfect’ backup process is often unfeasible for logistical reasons. When designing or evaluating your backup process, keep the above points in mind and try to adhere to the principles: regular backups that are separate from your primary network and tested regularly.
Step 4: Endpoint Detection and Response (EDR)
EDR solutions continually monitor network endpoints like PCs, laptops, and servers to identify and block malicious processes. In the case of a ransomware attack, an EDR solution would do one of two things:
-
Identify a known malicious application and prevent it from executing.
-
Identify malicious activity (bulk encryption) and shut down the application.
As with any higher-end security technology, EDR solutions aren’t appropriate for every organization. However, for organizations that have the resources, they are an excellent defense against many cyber threats.
The Ransomware Trade-Off
Whenever a well-known organization is hit by ransomware (or any other cyberattack) the same question is asked: Why didn’t they have security controls in place?
The answer is always the same: security controls cost money.
Ultimately, protecting against ransomware boils down to a simple cost/benefit analysis. So simple that it can be summarized by answering three questions:
-
What is the cost of penetration testing, basic anti-ransomware protocols like patching, and backups?
-
How much would it cost (including reputation damage) to recover from a ransomware attack?
-
And finally, how likely is your organization to be targeted with ransomware?
In the current climate, the answer to that last question is almost always ‘very likely’. As a consequence, for nearly every organization, the results of this cost/benefit analysis are simply this:
Basic security controls are affordable. Recovering from a ransomware attack may not be.
And that’s why the simple anti-ransomware protocols described in this article are so important. Because just like Benjamin Franklin said: “An ounce of prevention is worth a pound of cure.”
A version of this article originally appeared on Security Magazine on April 27, 2020.
To find out more about how penetration testing can help protect your organization from ransomware (and other cyber threats) arrange a demo of our Pentest as a Service Platform today.










