GigaOm Radar Report for PTaaS 2024
For the third consecutive year, Cobalt is honored to be recognized as an Outperformer in the GigaOm Radar Report for Penetration Testing as a Service.






Identify network vulnerabilities and comply with regulatory requirements more easily with the speed and flexibility that set Cobalt apart.

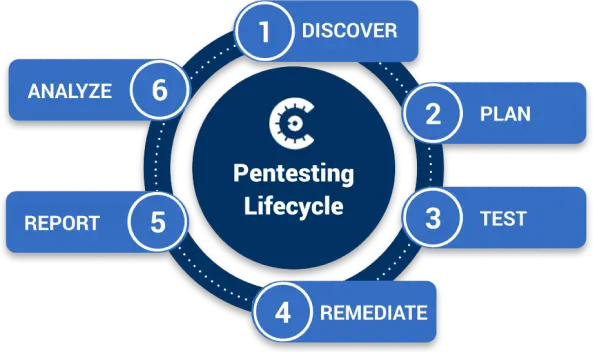
Find and proactively address issues in network infrastructure, applications, and systems before malicious actors do. A comprehensive approach to testing mitigates risk so your cybersecurity defenses are at peak performance.
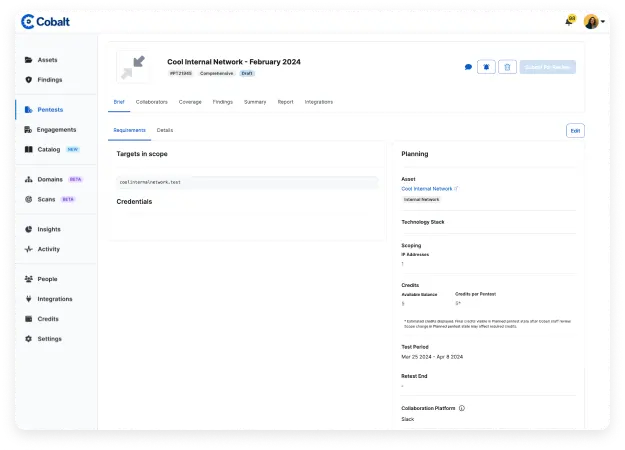
Identify weaknesses across network devices, firewalls, web servers, and other externally facing assets. Optimize security controls on the perimeter to strengthen your security posture organization-wide.
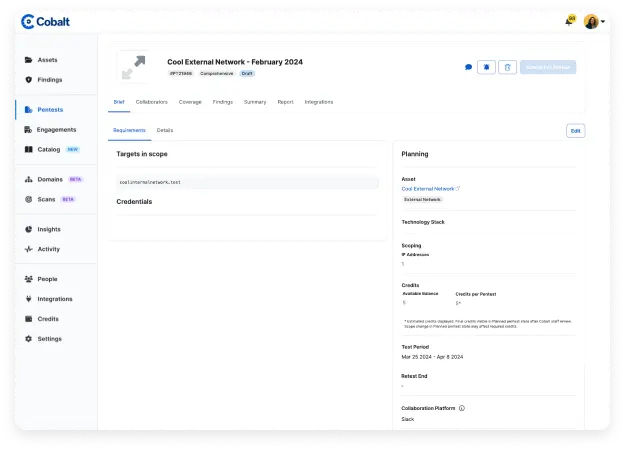
Our experienced pentesters simulate attacks to identify potential vulnerabilities in your networks using industry standard methodologies.
Protect your company against dangerous vulnerabilities and security gaps like SQL injection (SQLi) and Cross-Site-Scripting (XSS) with Cobalt Fast Start.
With Cobalt Fast Start limited-scoped pentest, our pentesters identify vulnerabilities quickly using the same techniques hackers use. Fast Start focuses on specific vulnerabilities like SQLi or can be applied to a portion of an app or website. This targeted assessment protects you from the most impactful security issues that have led to breaches year after year - all without overwhelming your team with noise.
Get ahead of hackers with Cobalt Fast Start.
Limited time offer, terms apply.



For the third consecutive year, Cobalt is honored to be recognized as an Outperformer in the GigaOm Radar Report for Penetration Testing as a Service.
Empower your security and development teams with Cobalt’s unique combination of a modern SaaS platform and our community of vetted security experts. Trust the pioneers of PtaaS as your offensive security testing partner across your entire attack surface.
