State of Pentesting Report 2025
Learn what 10 years of pentesting data and a survey of 450 security leaders tells us about the AI security gap, why pentesting is more essential than ever, and much more.






Start testing in as little as 24 hours, streamline workflows, and collaborate directly with security experts. Proactively plan your annual penetration test. Uncover insights with simple reporting – all within one easy-to-use location on the Cobalt Platform.
.png)
Integrate testing capabilities and expert services in one solution for comprehensive coverage. Tap into multiple services from a single provider for comprehensive coverage, streamline your processes, reduce overhead, and significantly improve efficiencies in security testing.

Whether you’re a startup or have a large security team, our platform can adapt. We tailor our flexible offerings to meet your specific needs, so you have the right protection without overextending your resources.
Work directly with testers to understand findings and impact, implement the most effective remediation strategies, and accelerate fixes.
View all of your security testing efforts in a single place to visualize risk. The Cobalt Offensive Security Platform provides the high-level perspective you need.
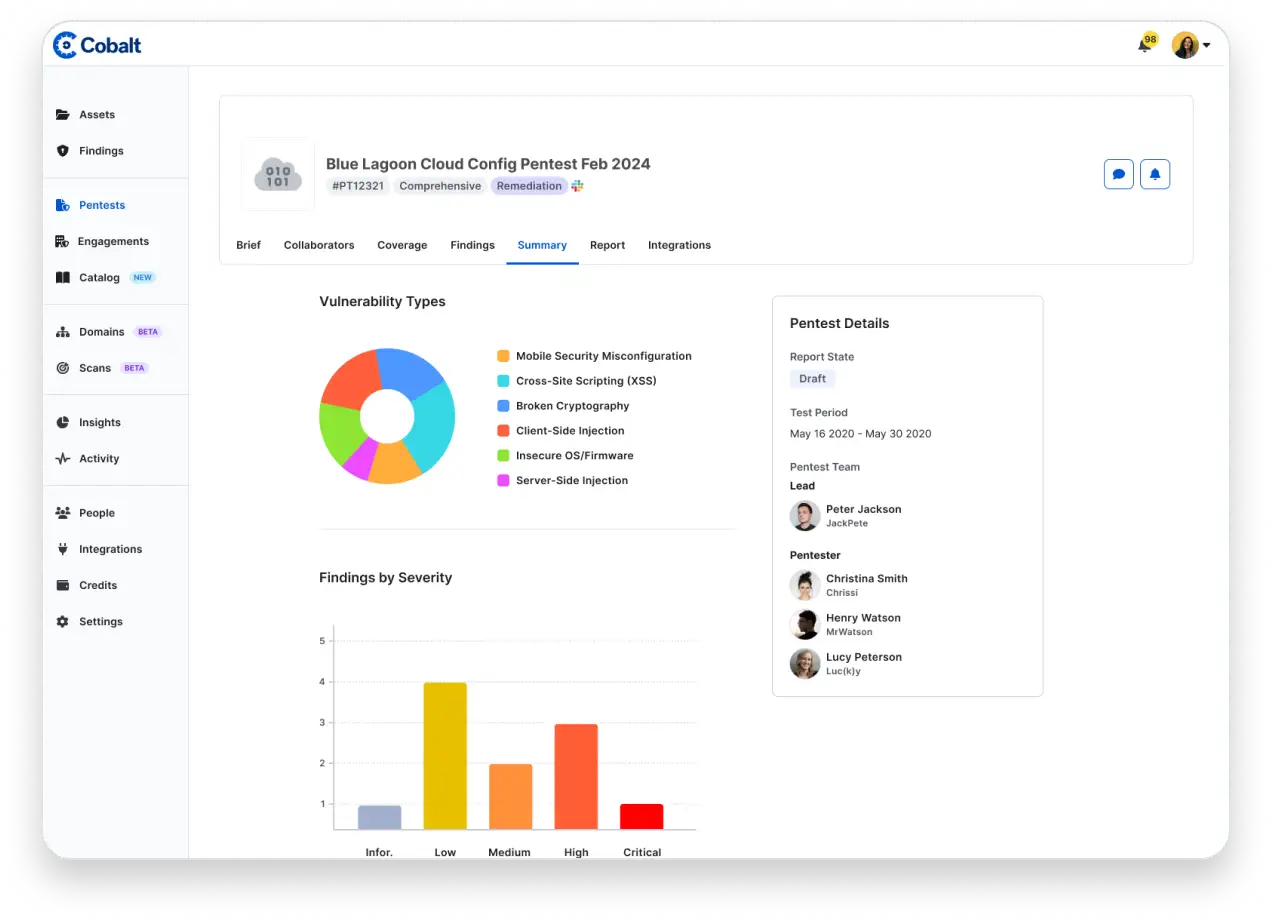
Better manage your security testing program with a single dashboard for all of your assets, pentests, and findings.
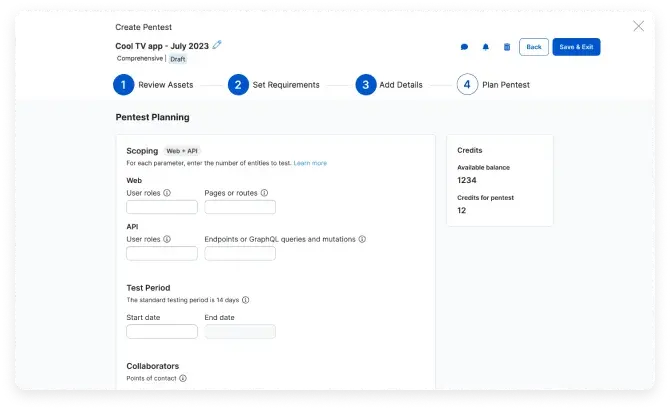
Launch tests quickly by defining the scope in four simple steps to fast-track your testing.
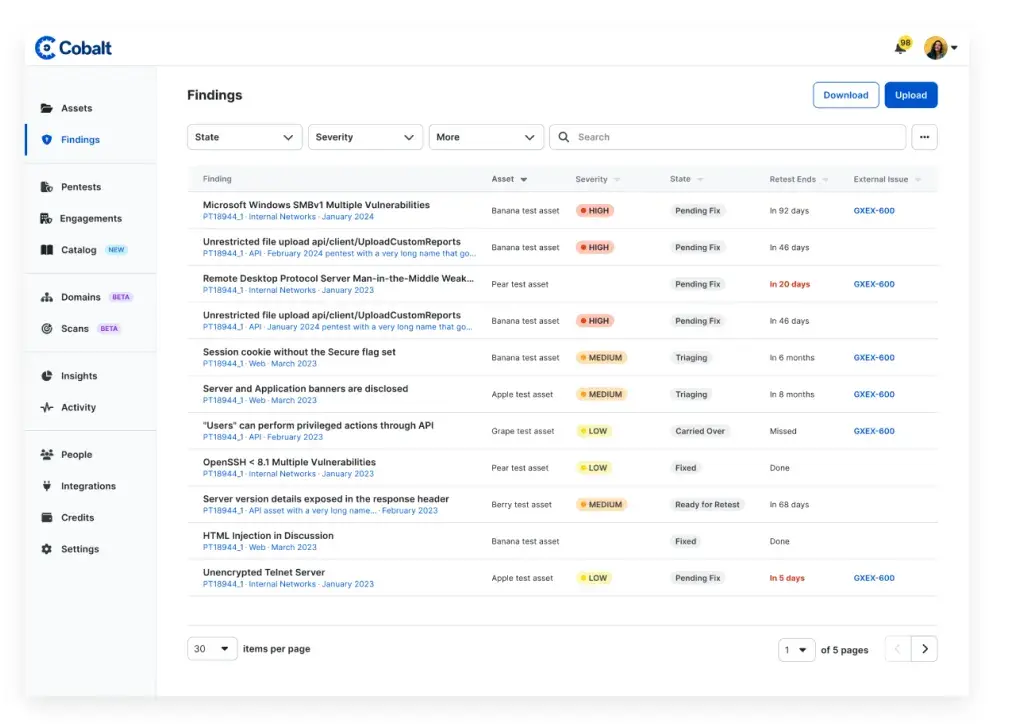
The Cobalt platform offers a single repository for all of your testing results. Evaluate individual test results and overall program performance in one place.
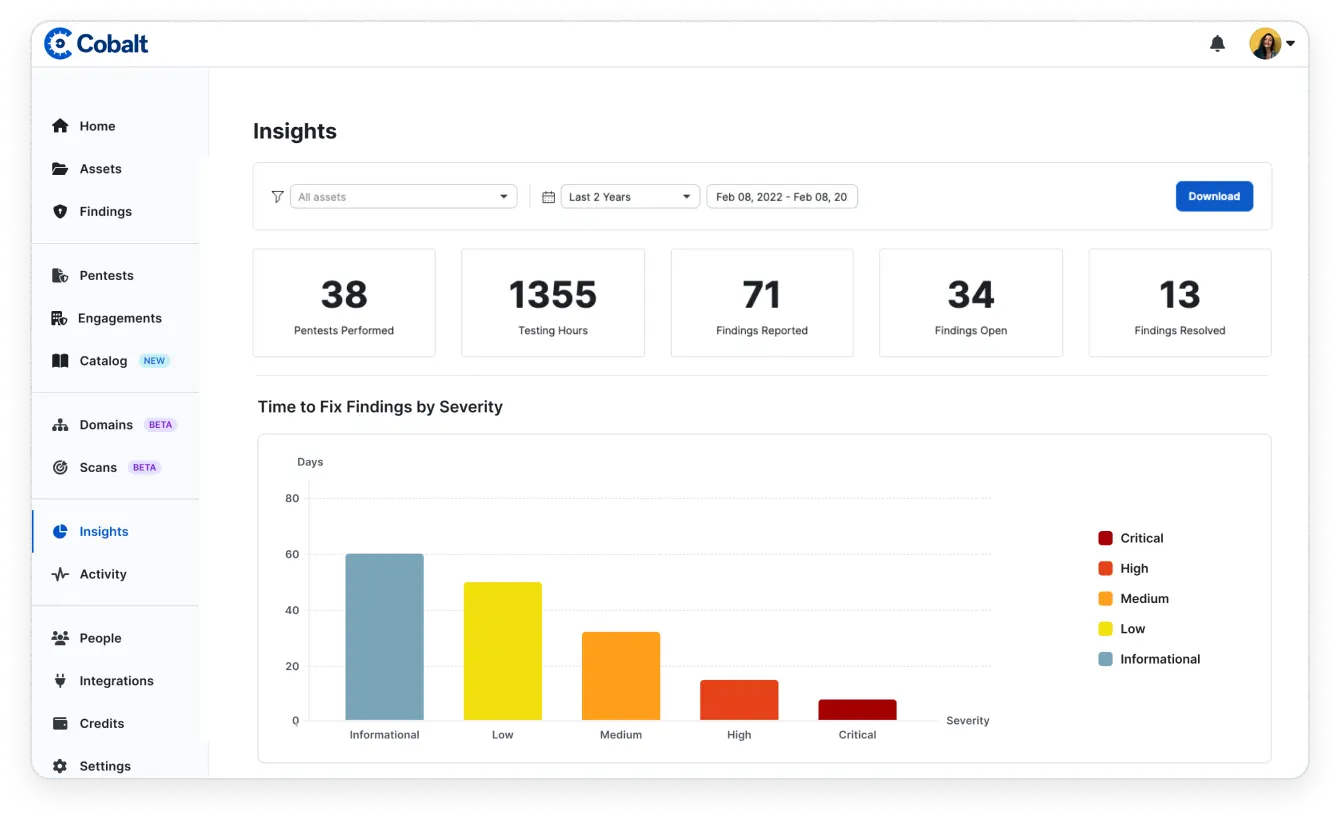
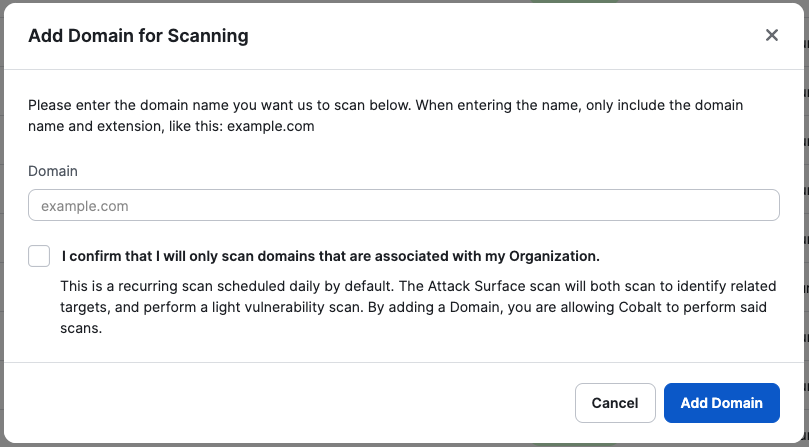
Run daily scans to see how your attack surface is changing, including new hosts, port, and IP changes – as well as basic vulnerability scanning to identify missing security headers, deprecated TLS, and weak ciphers. Discover externally reachable assets in your environment, even if they’re unknown to your team. Identify new assets that need to be tested, and quickly shift from discovery to testing within the same platform.
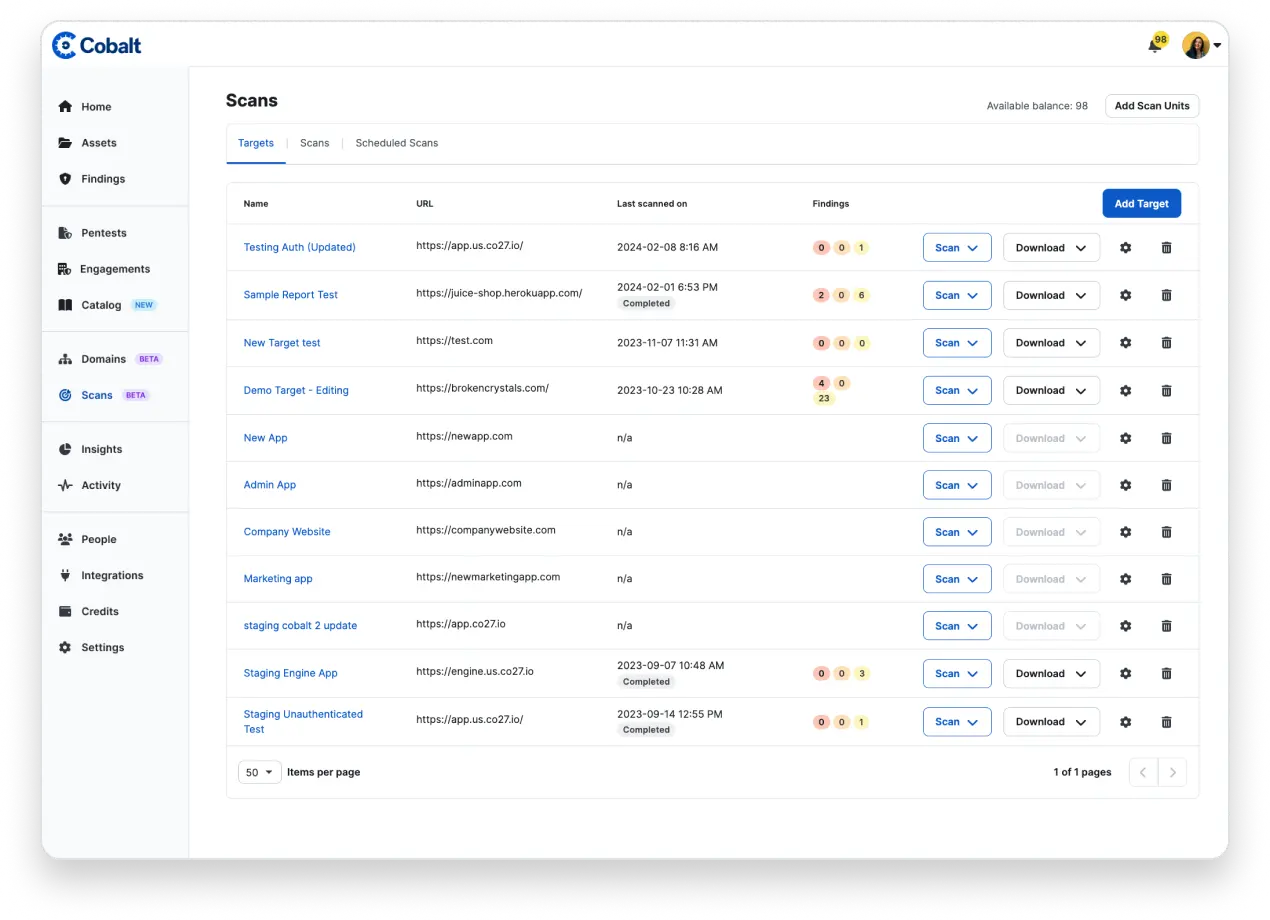
Cobalt Dynamic Application Security Testing (DAST) delivers comprehensive scanning of web assets and APIs to uncover vulnerabilities and provide a clear understanding of your risk posture. Cobalt DAST detects over 30,000 potential vulnerabilities, delivering detailed reports with precise remediation steps. Enhance your security strategy with Cobalt’s automated DAST solution as a great addition to your pentest program. Centralize scanning and testing for a unified view of asset risk.
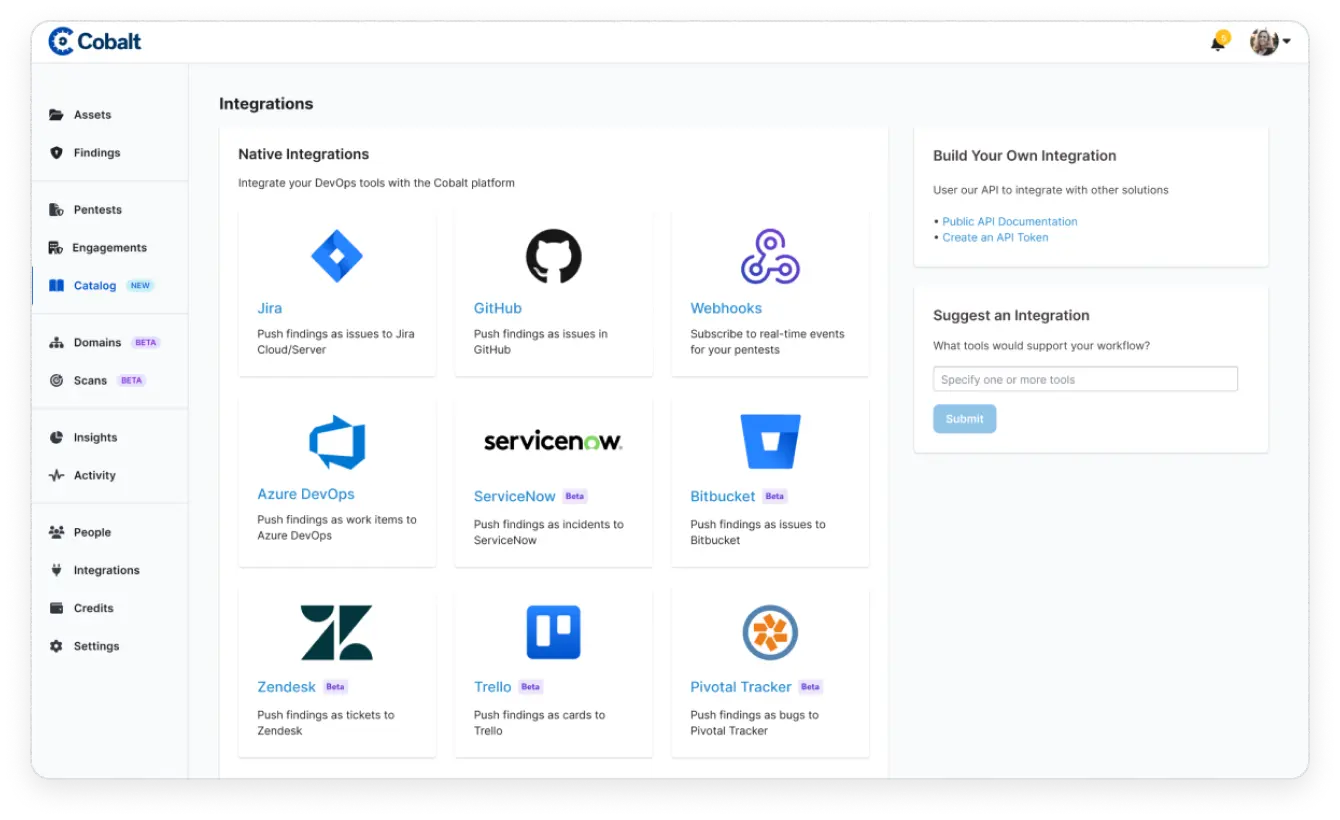
The Cobalt platform offers a wide range of integrations to easily bring testing data into your broader remediation workflows. Our native integrations with ITSM, DevOps, and collaboration tools can help you accelerate remediation and create more secure applications. Bring testing and validation findings directly into your governance, risk, and compliance systems.


"Being able to interact with findings in the platform and discuss them through Slack makes for a much more efficient process. We’ve been able to get into it and engage with the findings there, which is a big improvement on the old process."

"It's honestly been amazing working with Cobalt so far, as the platform really proved itself, and the testing quality is high. These tests allow us to bolster our application security and be true to our customers when it comes to protecting their sensitive data."
Learn what 10 years of pentesting data and a survey of 450 security leaders tells us about the AI security gap, why pentesting is more essential than ever, and much more.
Download the report to see how organizations are shifting and bringing both defense and offense to the cybersecurity battle.
Learn how speed, AI, and quality are driving change in modern security testing
Empower your security and development teams with Cobalt’s unique combination of a modern SaaS platform and our seasoned community of vetted security experts. Trust the pioneers of PTaaS to safeguard all your assets and attack surfaces with proven, practical solutions.
