Welcome to the first part of the Active Directory Pentesting series. In this blog, we will cover the fundamentals of Active Directory to create a foundation for learning more profound AD concepts in future blogs.
What is Active Directory?
Microsoft develops Active Directory (AD) as a directory service for Windows domain networks. In a nutshell, a directory is a hierarchical structure that stores information about objects in the network. A directory service provides methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as names, passwords, phone numbers, etc., and enables other authorized users in the same network to access this information. Hence, its primary functions include providing authentication and authorization to help manage access to network resources.
Active Directory acts as a centralized repository and stores all the data related to objects like AD users, computers, servers, and other resources within an organization. Previously, when directory services were unavailable, a person had to know the file's name, the server's name, and its folder path to retrieve a file. This works fine on a small network, but as the network grows, it becomes problematic. For example, when a user signs into a computer on the Domain, the services check the username and password to verify the account. The user is authenticated and logged into the computer if it is a valid username and password.
Without a centralized authentication system, there would be a lack of security as it was difficult to enforce strong password policies and track user activity across different resources. This made it easier for attackers to exploit weak passwords or gain unauthorized access to sensitive information. Additionally, because other resources had their authentication systems, ensuring users had the appropriate permissions to access the resources they needed wasn't easy. This often led to inconsistencies and confusion in access control. Implementing new security policies or integrating new resources into the existing infrastructure took a lot of work. This limited the organization's ability to adapt to changing business requirements.
Authentication of Active Directory
AD authentication is a Windows-oriented mechanism that verifies and permits access to Active Directory for users, endpoints, and services. By employing AD authentication, IT teams can simplify user and rights administration while obtaining centralized device and user configuration control via the Active Directory Group Policy functionality.
Additionally, it facilitates single sign-on (SSO) capability, enabling users to authenticate once and effortlessly access any corporate resource in the Domain.
There are two types of authentications used by Active Directory:
Kerberos
Kerberos is a network authentication protocol that identifies each user who provides a secret password. Kerberos is used in Active Directory to provide information about the privileges of each user. It does not perform authorization. Each service's responsibility is to determine if the user has access to its resources, and Kerberos does not validate which resource or service a user can access.
With Kerberos-based AD authentication, users need only log in once to access enterprise resources. Unlike the LM and NTLM protocols, which transmit login credentials over the network, Kerberos generates a session key for the user, eliminating this security risk. This session key is valid for a specified time period, affording users greater flexibility in the authentication process.
LDAP
Active Directory supports the Lightweight Directory Access Protocol for directory lookups and with Kerberos. The lightweight Directory Access Protocol allows systems and applications to talk to directory services such as Active Directory. Non-Windows devices, such as Linux machines or firewalls, authenticate to Active Directory via RADIUS or LDAP.
Components of AD
There are two primary components of Active Directory: physical components and logical components.
Physical AD Components
Domain Controller
A domain controller is a server that manages network and identity security. Domain Controller is an important server and primary target for attackers because it holds the key to the Active Directory environment. In this environment, all user requests go to the domain controller for authentication and authorization. The domain controller then authenticates the user identity by validating a username and password and then authorizes access requests accordingly.
Working of Domain Controller
Enterprises usually have several Domain Controllers, each with a copy of the Active Directory (AD).
All the user login credentials from the network are consolidated in Active Directory Domain Controller service. Hence, the Domain C uses the Active Directory to house the user database and login information.
So, when users log in to their Domain, the Domain Controller checks and validates their credentials, like usernames and passwords, and accordingly either permits or denies access for that user. Thus, a remote Domain Controller helps manage and maintain network security and user identity security enforcing security policies across Active Directory domains.
Global Catalog Server
The Global Catalog (GC) is a feature within AD that allows a domain controller to provide information on any object in the forest. When installing the first domain controller, it will become the GC server, and other domain controllers can be promoted as GC servers according to the business requirements. The GC server holds the full writable copy of objects in its host domain and the partial copy of the objects in other domains in the same forest. Applications and users in one Domain can query for the objects in another domain via this server. To speed up the queries for the objects in other domains of the forest, a GC server has a replica of its Domain and read-only partitions with objects of other domains.
Read Only Domain Controller
There are three types of domain controllers:
• Primary Domain Controller (PDC)
• Read-only domain controller(s) (RODC)
• Backup Domain Controller
Read-Only Domain Controllers (RODC) do not allow any changes to the database. In the case of a Read-only domain controller, changes must be made on a writable domain controller and then copied to the Read-only domain controller in a particular domain.
The primary purpose of a Read-only Domain Controller is to facilitate authentication from remote office branches and allow users to access domain resources and are suitable to address issues in branch offices in remote locations that might not have a domain controller or with poor physical security, poor network bandwidth, or no local expertise to support it.
Logical components
Objects
Objects in Active Directory are entities that represent resources that are present in the AD network. A set of information characterizes them. Each piece of information is called an Active Directory object attribute. These objects are assigned a unique security identifier (SID) to grant or deny the object access to resources in the Domain. There are different types of objects in the Active Directory including:
- Users: User accounts are primarily assigned to users to gain access to domain resources. You can also use them to run programs or system services.
- Computer: This is a computer that is joined to the Domain.
- Groups: There are two types of objects: Security and Distribution groups. A security group groups user accounts that can provide access to resources. Distribution groups are for email distribution lists.
- Contacts: A contact is for email purposes. You cannot log on to the Domain as a contact, and it cannot be to secure permissions.
- Organizational Unit (OU): An organizational unit is a container object capable of housing users, computers, groups, or shared folders. OUs serve organizational purposes by facilitating resource management and enabling control delegation among objects within the OU.
- Printer: A printer object represents a printer resource in an AD network
- Shared Folder: Creating an object occurs when you publish a shared folder in Active Directory. Publishing shared folders in AD simplifies the process of locating shared files and folders within the Domain for users.
Active Directory Schema
Active Directory (AD) schema is a blueprint that states the rules about the type of objects that live in the AD and their related attributes. The schema defines the content, structure of object classes, and the object attributes required for object creation. During the creation of a new object, AD references the schema's classes and utilizes the retrieved information to construct the object.
Each object in Active Directory is an instance of a class in the schema. A user object, for example, exists as an instance of the user class. Attributes define the pieces of information that a class, and thus an instance of that class, can hold. Syntaxes define the type of data that can be in an attribute. For example, if you define an attribute with a syntax of Boolean, it can store its value as True or False, or it can be null. A null value has an implementation-specific meaning; it could mean True or False depending on the application using the value.
The fundamental objective of the AD schema is to establish the objects that can be stored in AD. The schema consists of a compilation of definitions that govern the AD database's permissible objects and the information types associated with those objects. The schema is also managed as an object to be administered and manipulated.
The schema is defined by two types of objects: classes and attributes. These classes and attributes are stored separately within the schema. When referring to these objects collectively, we refer to them as schema objects or metadata.
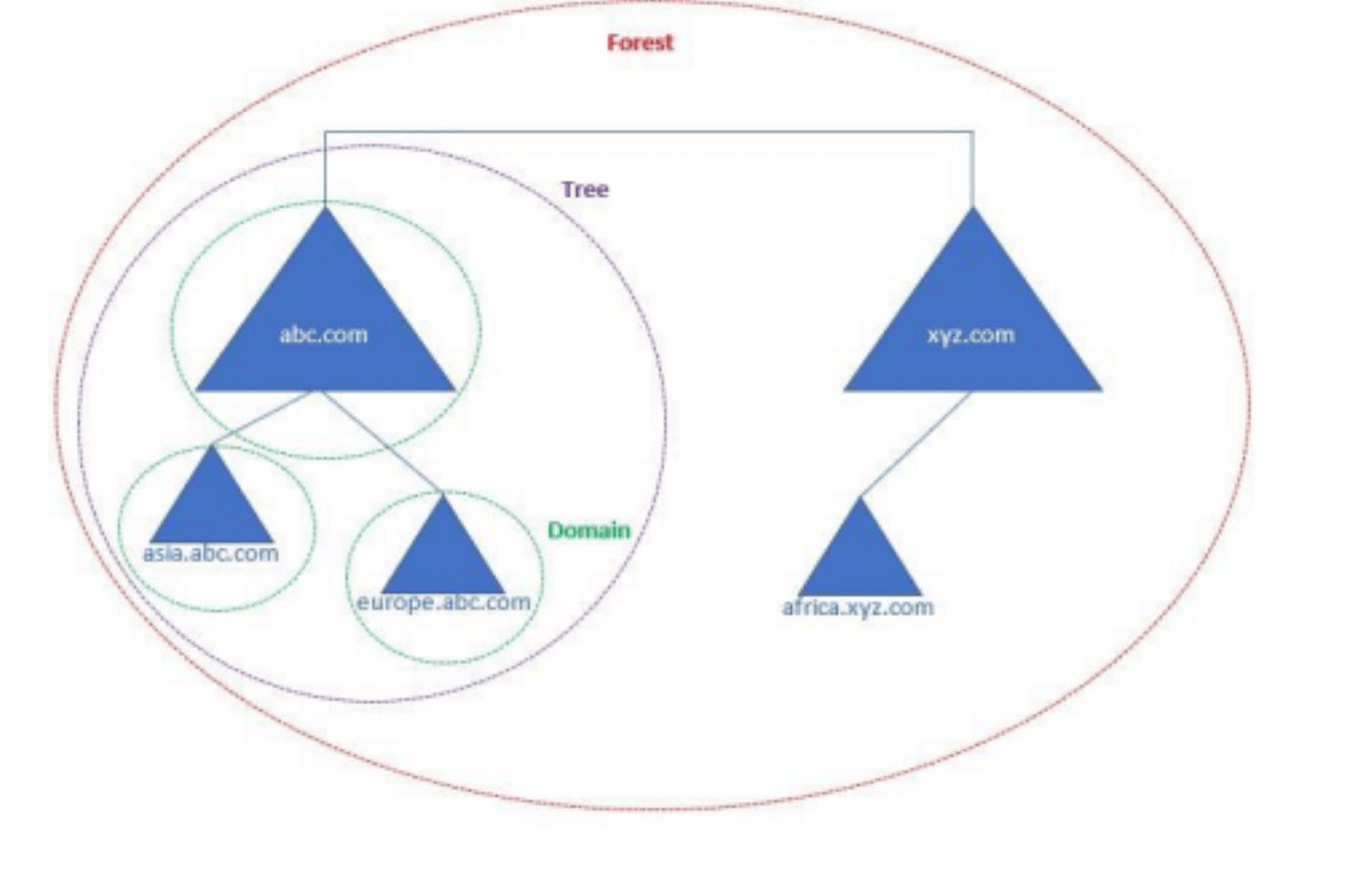
Domain
A logical group of objects within the Active Directory is called Domain—a hierarchical structure for users, groups, computers, and other objects. A DNS name identifies the Domain. When you log into a computer part of a domain, you log into the DNS domain name.
Domain Tree
Trees organize Domains. A domain tree comprises several domains with a common schema and configuration, forming a continuous namespace. You create a domain tree when you add a child domain to a parent domain. A domain tree is just a series of domains connected hierarchically using the same DNS namespace. Trees can divide in two ways. One view is the trust relationships between domains. The other view is the namespace of the domain tree.
• Viewing Trust Relationships
• Viewing the Namespace
Forest
A forest comprises one or more domain trees that share a unified logical structure, directory schema (class and attribute definitions), directory configuration, and global catalog. Each Domain in the forest can have one or more Domain controllers that can interact with other domains and access the resources from other domains.
Domains in the same forest link with two-way, transitive trust relationships. Objects in separate forests can only interact if the administrators of each forest create trust between them.
The most cost-effective option is a single forest because it requires the least administrative overhead. It also enables maximum collaboration among users since all objects in the forest are in a single global catalog. Multiple forests can be required or even necessary, depending on the data isolation and data autonomy requirements for the groups in the organization.
Forest Design models
▪Resource forest model
▪Organizational forest model
▪Restricted access forest model
Resource Forest model
As the name suggests, this model is only for resources. In the resource forest model, a separate forest manages resources. Resource forests only house essential user accounts, necessary for service administration and alternate access provision to resources in the event of unavailability of user accounts in the organizational forest.
Organizational Forest Model
Every Active Directory design includes at least one organizational forest. The user accounts and resources are contained in this structure and are independent. This forest provides service or data isolation or service autonomy in case it is configured to be inaccessible by users outside the forest.
Restricted Forest Model
A separate forest is where data and user accounts are supposed to be kept independent of other organizations in the restricted access forest structure. Restricted access forests isolate data where the consequences of compromising project data are quite high/ severe.
Organizational Unit
An active directory organizational unit is a container within Microsoft Active Directory. It is the smallest unit to which the administrator can assign Group Policy settings and permissions. An OU is a subdivision within Active Directory to place users, groups, computers, and other organizational units. One can create organizational units to mirror their functional or business structure. Each Domain can implement its organizational unit hierarchy. If the organization contains several domains, one can create organizational unit structures in each Domain that are independent of the structures in the other domains. Control is determined by the access control lists (ACLs) on the OU and the objects in the OU. To facilitate the management of large numbers of objects, AD DS supports the concept of delegation of authority (DoA). Using delegation, owners can transfer full/ limited administrative control over objects to other users or groups.
Trusts
Active Directory Domain Services (AD DS) ensure security across multiple domains or forests using Domain and forest trust relationships.Before authentication can occur across trusts, Windows verifies whether the requested Domain by a user, computer, or service has a trust relationship with the requesting account's Domain.
In a forest, domains connect by connections called trusts. This is the reason why users from a domain can access resources of other domains. In an AD environment, once trust establishes between two domains, it grants access to resources to the users, groups, and computers across entities. This is done by linking the authentication systems between the domains and allowing authentication traffic to flow between them.
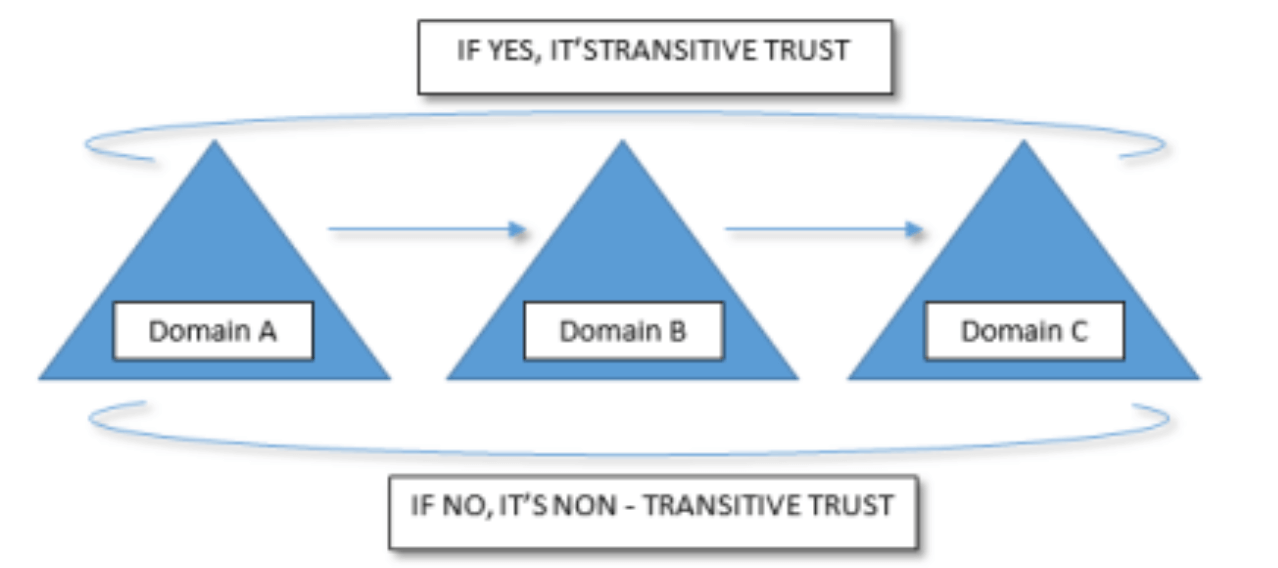
Transitive Trust
Transitive trust is a two-way relationship automatically created between parent and child domains in Microsoft Active Directory Forest. When creating a Domain, it shares the resource with its parent domain by default, enabling authenticated users to access a resource in both the child and parent. When adding child domains to the new Domain, the trust path ascends through the domain hierarchy, extending the initial trust path between the new Domain and its parent domain. Transitive trust relationships propagate upwards through a domain tree, forming transitive trusts among all domains in the domain tree.
Authentication requests follow these trust paths so that any other domain can authenticate accounts from any domain in the forest in the forest. With a single sign-on process, accounts with proper permissions can access resources in any domain in the forest.
Non - Transitive Trust
A non-transitive trust can deny trust relationships with other domains. Non-transitive trusts do not extend beyond the two domains that the trust connects. Hence, when a domain trusts another domain, it cannot communicate with the other domains that the trusted Domain has communications with.
Based on the direction, AD trusts fit into two categories. They are as follows:
• One Way Trust
• Two-Way Trust
One Way Trust
A one-way trust is a unidirectional authentication path created between two domains. In a one-way trust between Domain A and Domain B, users in Domain A can access resources in Domain B. However, users in Domain B cannot access resources in Domain A.
Two-Way Trust
Some two-way relationships can be non-transitive or transitive depending on the type of trust created. In a two-way trust, Domain A trusts Domain B, and Domain B trusts Domain A. This configuration means authentication requests pass between the two domains in both directions.
Sites
AD sites manage organizations with branches spread across different geographical locations but under the same Domain. AD sites are highly connected networks of IP subnets that define the physical structure of AD. Within an AD site, there is no change in any aspect of the logical structure of the environment. Every AD site maps to an AD domain, which can have multiple sites mapped to it.
References
- Microsoft: Active Directory Domain Services Overview
- Microsoft: Core Concepts of Active Directory Domain Services
- RootDSE: Active Directory Basics
- Atera: What is a Domain Controller?
- Testout Server Pro SlidePlayer