With a sea of information available to most modern security practitioners, actions need to be based on high quality data. Cobalt is on a mission to bring data to our customers that enables their programs and ultimately helps secure their assets.
Let’s start with some basics. At Cobalt, our expert pentesters work together to discover findings. These are the building blocks of a pentest, and gathering this data leverages the skills and experience of some really technical people to uncover items that are worth fixing in your network. These findings are then assessed and triaged to deliver a curated list to our customers — aka items which present a documented risk to the assets covered in the scope of the pentest. Once in a customer’s hands, these would be best described as vulnerabilities.
Until recently, we categorized findings using two foundational pieces of data (business impact and likelihood) into three criticality bands:
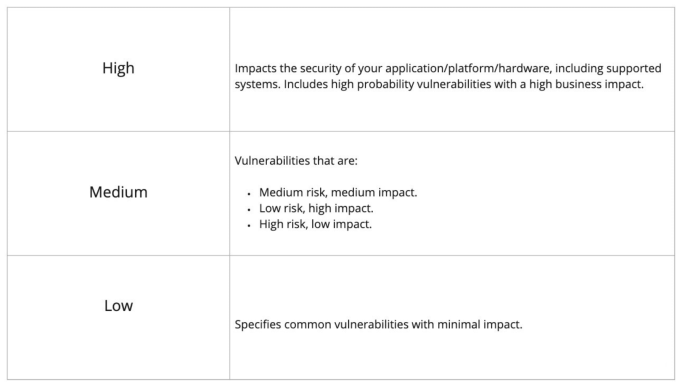
Over time, our understanding of criticality has evolved, and we’ve been paying attention to some heavyweights of the industry as they seek to help organizations understand not only the risks, but also their impact. One thing we pride ourselves in at Cobalt is humble learning and that we are always seeking to improve our awareness of customer needs.
While the High/Medium/Low scale offers simplicity and enables decision makers to take the necessary action to keep their assets safe, it lacks some of the granularity we have heard our users ask for time and time again, such as “Are there issues in the Low category I can safely ignore?” and “Are any of these issues worth waking up my CISO for?” With that in mind, we’ve moved to a model that also includes Critical and Informational as new severity levels.
“Wait, what? I thought we were talking about criticality?”
So yes; we were, but bear with us. Severity is the term best aligned with the frameworks and models for vulnerability management when classifying risk. We are working hard to adopt terminology that supports our customers, and decided this was an optimum time to align some of our key language with the security industry. Our platform will adopt this change from early November 2021, and wherever you saw Criticality, you will now see Severity.
Alongside the terminology, the vast majority of security aggregation tools follow this pattern of Severity and Critical/High/Medium/Low/Informational vulnerabilities. Aligning with this wider system enables teams to export data to 3rd party tools more easily, and offer maximum options for dividing up issues according to risk.
Now for the fun part. Let’s get to these new levels. 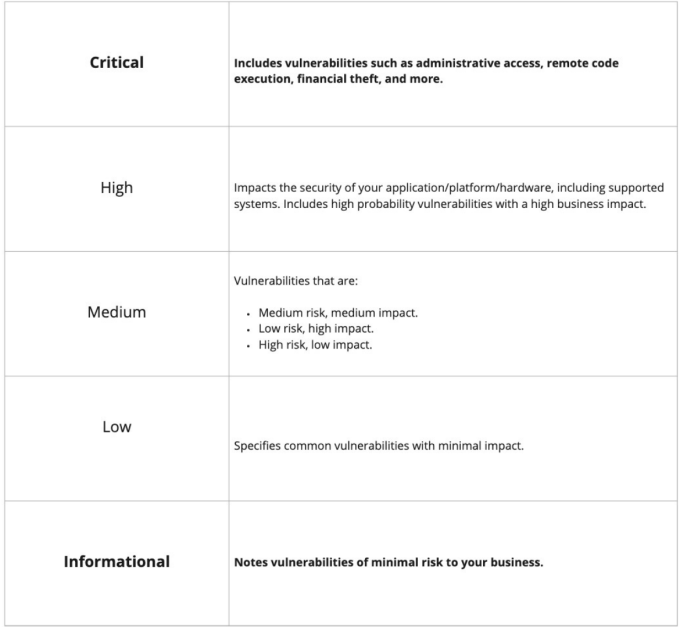

The new Critical level is designed to sound the alarm bells — as in, this is the highest end of the high risk category. These are issues that are being exploited in the wild, and are an organization’s shortest route to hearing their name mentioned in the latest news and/or breach reports! Long story short, these are items you want to create an action plan for. These issues are why we do what we do, and why we leverage experts to help us secure the portfolio against a sea of attackers.
Phew. Still with us? Great. Let’s talk about Informational. These are the other end of the spectrum, and in some cases — won’t appear as a categorization for vulnerabilities. Why? Because they present no real risk. As the name suggests, they can be considered as pieces of information, rather than vulnerabilities. Are they worth knowing about? Yes. Are they worth logging and tracking to keep in line with positive security practices? Absolutely. Are they worth waking up your C-suite at 4am on a Tuesday? Only if you were already planning a change of career!
This change will roll out for all findings across the platform. Approximately 10% of findings will now fall into the Informational category, and 1% of findings will leap up into the Critical category.
Will this impact existing reports?
Yes, but we’ve given it some thought. And we are releasing a revert to High/Medium/Low toggle for any report so you can download it in the original context it was created. By default you will see the new severity levels, and as always we are keen to hear feedback on how this feature update works for you and for your security teams. Reach out to your Cobalt Customer Success Manager with your thoughts, or check out Cobalt's latest product updates.









