The long-awaited Cyberpunk 2077 arrived last week, and well, it hasn’t met expectations. To put it simply, the Internet is outraged. Decrying the game’s buggy gameplay, disappointed players are calling for refunds while developers are working overtime to push patches. For a game that was expected to be one of the best video games of the decade, it crashed in typical 2020 style.
I’ve been a huge CD Projekt Red fan for years, but not because of its game design and experience. CD Projekt Red is known for its exceptional worldbuilding and lore, creating fully immersive and rich universes that allow you to dive deeper into the backstory and detail. As a hacker, gamer, and lore enthusiast, I was excited to see how Cyberpunk 2077 envisioned a cyber-immersive world.
I’m not going to trash the gameplay or chastise overzealous marketers for selling an unfinished product. There’s a whole subreddit for that. Instead, I wanted to explore the worldbuilding and hacking to see what they got right, wrong, and somewhere in between. So let’s dive in.
No matter which path you choose in the game, there isn’t a ton of context. They throw you into the gameplay in media res, leaving you to quickly make dialogue choices without the opportunity to figure out the backdrop. Fortunately for you, I read the world compendium.

Restricted public access to information: Real
Cyberpunk 2077 is set in a future dystopia where a weakened United States is reckoning from economic collapse, successive wars, and climate change. Massive corporations, which largely trade in technology, bioinformatics, and weapons, seized geopolitical control. Megacorporations Arasaka and Militech engaged in corporate warfare at the same time “thousands of viruses and malware” were launched into cyberspace, subsequently crippling the stock market. To protect the country from rogue code, Netwatch, the equivalent of the NSA, constructed a massive firewall separating the open World Wide Web from the United States. Northern California subsequently ceded from the United States and Night City blossomed into a part anarchist, part capitalist metropolis.
The concept of a country implementing a massive firewall to restrict information isn’t speculative fiction. It’s reality. Every country has some restrictions on the Internet, including the United States, to mitigate illicit use. If you build an online black market where people can exchange cryptocurrency for drugs and assassins, the FBI will shut you down. As for the deluge of viruses and malware, that’s an ongoing struggle that plagues businesses and consumers alike in 2020, particularly through ransomware.
Yet restricting the flow of information online isn’t a novel concept either. The Great Firewall of China was constructed in the late 1990s and still pervades today. Intended as a means of enforcing social order during trade expansion with the West, the internet in China remains heavily censored. Websites like Facebook, Twitter, Wikipedia, and Google are banned. Instead, netizens rely on Chinese-operated sites like Weibo and QQ. Certain searches, like the Tiananmen Square protests, are restricted. And the idea of a city revolting against national surveillance and the restriction of information? We’re witnessing it right now in Hong Kong.
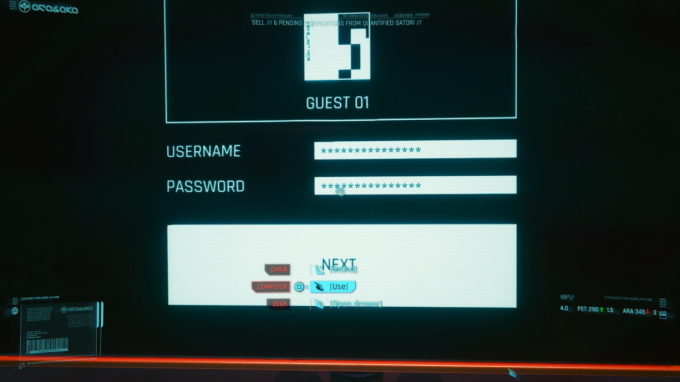
Credential theft: Real
In the year of 2077, the Arasaka Corporation wields formidable influence over Night City. It is also largely responsible for protecting the metropolis. Drones, automated cars, brain implants, and cyberware body modifications are the pulse of the city. Unfortunately for security professionals, usernames and passwords pervade—even for counterintelligence agents working with the Arasaka company to wage war across the globe.
The irony is that security professionals today have argued against using passwords. Credential theft plays a large role in breaches because passwords are frequently exposed or easily guessed. Following the recent SolarWinds breach, which compromised more than 18,000 companies, it came to light that the password for the company’s update server was “solarwinds123”. As a penetration tester, I am always on the lookout for credentials and will attempt to brute force authentication into systems. I might also attempt to guess passwords and security questions based on an employee’s social media profiles. Hopefully passwords will be deprecated in our lifetime, but for Cyberpunk 2077, let’s just pray the password for this character’s desktop isn’t ArasakaRules!

Defensive misdirection: Real
For those who played through the corporate narrative of Cyberpunk 2077, you might have missed this NPC on the other side of your office. He mentions a corporate spy who’s just received top-level clearance for their competition. Yet the mole is not able to dig up any dirt. As the NPC explains, “[the servers] are clean … we suspect they flagged him and are feeding him phony data.”
This situation is surprisingly similar to modern-day honeypots, where security professionals will create fake servers to lure cybercriminals. Attackers will think they have breached their target, when in actuality they have fallen into a trap. Honeypots are effective at distracting cybercriminals from attacking the real target while also gleaning information about their tactics, techniques, and procedures.
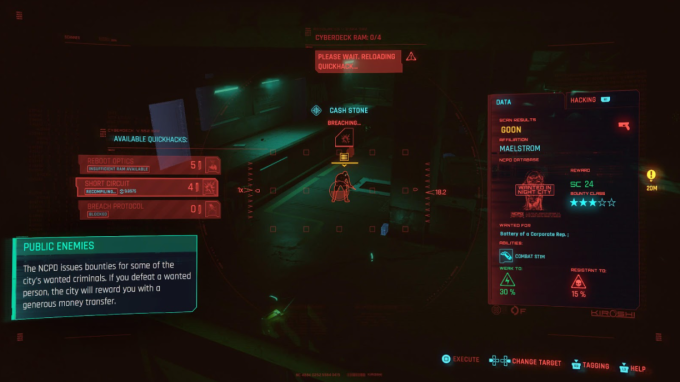
Quickhacks: Real, though not completely accurate
Cyberpunk 2077 relies as much on aggression as it does on strategy. You can brute force your way through a battle with sheer gunfire and melee attacks, but a more efficient tactic is to hack. Characters can scan targets and identify “quickhacks” for both people and technology, then assign RAM for exploitation. Although it’s wild to think we could potentially “scan” and hack humans, the methodology is similar to penetration testing today.
All penetration testing begins with initial reconnaissance and enumeration. We first understand the target and what’s in scope, then begin to gather as much information as we can about the assets. This includes scanning assets, typically through using the tool nmap, and gleaning as many details as we can about the servers.
The “available quickhacks” option within Cyberpunk 2077 is also similar to a penetration testing tool called Metasploit. It essentially provides a list of potential vulnerabilities based on the target and then assists in exploitation.
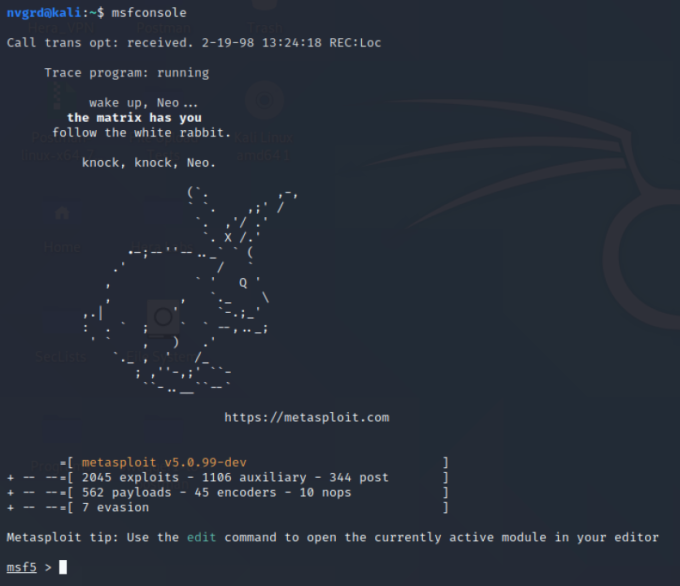
An example of launching Metasploit, the 2020 version of quickhacks.
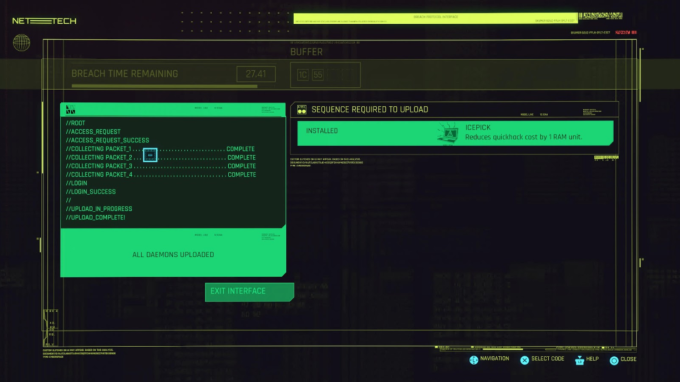
The mechanisms of the quickhacks don’t quite make sense to me. It’s unusual to start with “root” access to a system and then request access, login, and upload a malicious exe. This could be a circumstance where Cyberpunk 2077 tries to outline a pivot, where an attacker (or penetration tester) moves from a rooted system to one that is not yet accessible in the network. Or it could just be factually inaccurate. However, I was impressed that the game developers included packet sniffing, where you collect and analyze packets passed through networks to gather additional information.
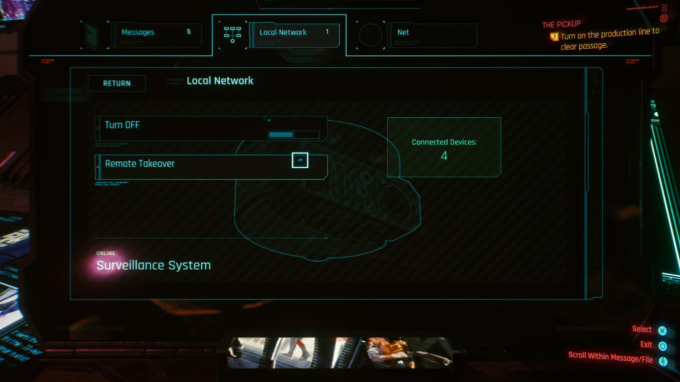
Hacking connected devices: Real
Cyberpunk 2077 does an excellent job of revealing just how many “things” are connected to the Internet and offers opportunities to exploit them for quest reconnaissance.
It is scarily easy to find information on IoT devices today. While I was working on this article, I was able to find webcam footage from a building in Kherson, Ukraine using the search engine Shodan. You can even search through surveillance cameras on your own using this nifty tutorial.
Like in real life, Internet-connected devices in Cyberpunk 2077 are easy to take over remotely. Internet of Things (IoT) devices are everyday objects that are connected to the Internet. This can range from refrigerators and toaster ovens to pacemakers and insulin pumps. Yet IoT devices are shockingly insecure. In a case earlier this year, a cybercriminal hacked a Ring security camera in a child’s bedroom—and communicated with the 8 year old girl. Security researchers have also identified ways to place malware in pacemakers. In short, anything that is connected to the Internet is at risk of getting hacked. Not every gadget that is “smart” will work to your benefit.

Hacking human bodies: Fiction...for now
In a world where our bodies are completely connected to the Internet, make sure you close Port 1779. I cracked up that Cyberpunk 2077 specifically mentions a port that allows third parties to access your brain circuitry and software—and in this case, the companion made sure she was connecting securely. In all seriousness, open ports can pose significant risks and allow cybercriminals to access unauthorized information. When penetration testers scan a network, as I mentioned earlier in this blog post, we always search for open ports. If I was an attacker attempting to hack another person, I would be very interested in open port 1779.
Finally, I wanted to draw attention to a speculative idea in Cyberpunk 2077 that is creeping closer to reality thanks to advances in modern science.
The idea of cyberware intricately connected to our bodily functions—from the frontal cortex to the nervous system—may seem fantastical. Certainly the way it is imagined in Cyberpunk 2077 is unrealistic now. But advances in modern medicine are pushing the frontier.
Researchers at Brown University, with support of grant money from the U.S. Defense Advanced Research Projects Agency, are testing an “intelligent spinal interface” to help connect neural circuitry with injured spinal cords. The goal is to help people with spinal cord injuries regain movement and sensation in paralyzed limbs through rerouting neural signals.
Meanwhile, scientists are building bionic limbs that “establish an interface between the biological residuum and an electronic device, providing not only motor control of prosthesis but also sensitive feedback.”
While Cyberpunk 2077 paints a bleak dystopia filled with violence and corruption, it also imagines a world of technological possibilities. Many of the speculative elements of the game are true to modern-day advances, just repurposed for the entertainment of the masses. As the game takes hacking and technology to their extreme, we are seeing the seeds of these technologies planted in modern research.
The future is closer than we think.










