Core Academy is a platform for our Core Pentesters to share knowledge and expertise. Harsh Bothra hosted a session on Thick Client Testing. Harsh has been with Cobalt since 2021 and is an avid contributor to our Technical Blog Program. Watch his session below 👇
---------------------------------------------------------------------------------------------------------------------------------------------------------------------
In the recording, we discuss what thick clients are, give a quick overview of the architecture, and explore common problems when testing thick clients.
What Are Thick Clients?
Thick clients have a lot of nicknames like fat clients, rich clients, or thick clients. These all mean the same thing.
So what are thick clients? Thick clients are “Desktop Applications” that can be installed locally on a system. These applications may or may not interact with External API/Web Servers.
Common examples of thick clients are:
- Proxy Tools like Burp & Zap
- Web Browsers
- Computer Games
- Productivity Tools
- Audio/Video Conferencing Tools
- Diagnostics Software
Thick Client Architecture
Typically, there are two types of application architectures for thick clients. A two-tier application and a three-tier application.
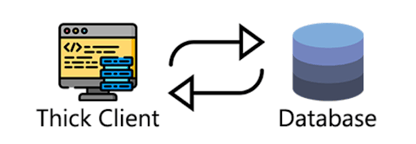
In the two-tier architecture, all the components required for the functionality of the application such as the database, code logic, etc sit on the local system/network of the user and generally, there is no external API communication.
In the diagram below, there's a thick client and a database. They all interact on the same local system or a local network. There is no third party or interaction that goes outside the network.
In the three-tier architecture, the application makes an outbound call to the external-facing components like an application server or an external-facing entity to process certain application logic.
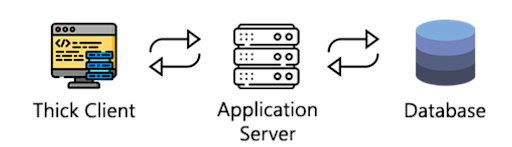
In the diagram above the thick client, application server, and database interact with each other.
One example of a three-tier architecture is Slack, where the communication involves APIs and other protocols to interact with other users.
Proxy Aware vs Proxy Unaware Clients
It’s also important to know if you are working with a proxy-aware thick client or a proxy-unaware thick client.
- Proxy-aware thick client: Natively includes proxy settings, so outgoing and incoming traffic is sent to the proxy server and then to the main server
- Proxy unaware thick client: Do not natively include proxy settings so the user is required to make some changes in the system’s host file
Thick Client Testing Methodology
Currently, there is no definite methodology when it comes to thick clients because there is no standard. There is an OWASP thick client top 10 but it is still in development.
Here is a methodology framework to follow:
- Enumeration: Identify language & framework, architecture, intercept traffic, and common functionality probing
- Client-Side Checks: Memory analysis, file analysis, binary analysis, etc.
- Server-side Attacks: OWASP Top 10 Checks if the application interacts with Web/API server
- Network Attacks: Intercept Traffic, Examine Vulnerabilities on External Server Interactions
Common Challenges in Thick Client Testing
There are a few common challenges when it comes to thick client testing. The first challenge is setting up the correct environment. You have to do this every time. Every test can require a different type of environment.
So, for example, in this session, we focus on the Windows-based client application. If you're testing a Linux- or a Mac-based client, you’ll need a proper setup. So having a setup per a thick client's requirement can sometimes be challenging and tedious.
The second challenge is language understanding. Often we see thick clients written in various programming languages. The most prominent are java.net and the visual basics. So, If you don't have familiarity with that application, you might face challenges. Especially on the client side because a lot of interesting attack vectors for finding the remote code execution or local proof escalation or code analysis depend on how familiar you are with the particular programming.
The third challenge is traffic interception, especially with proxy-unaware clients. A lot of old applications and old tech client applications are not proxy aware. And, it becomes a challenge to find a way to get the traffic intercepted.
In some scenarios, if your application is implementing any sort of certificate pending, you must also find a way to bypass that in intercepting the traffic.
Getting Started with Thick Client Pentesting
Watch the full training session to dive into setting up Thick Client Lab, what you need, tools often used when testing thick clients, and common thick client vulnerabilities. The training also explores common exploits for some of the most common thick client vulnerabilities.