Starting a company is hard, very hard.
Yet, different aspects of a startup will be more challenging than others, such as a security plan and corresponding budget. This is because companies can't readily use traditional approaches like setting a percentage of revenue to cybersecurity as they can with marketing or operations.
So today, we'll aim to answer an important question, “How much do companies spend on cybersecurity?”
Due to the vast difference in security budgets, it's often not the best approach to plan based on industry standards. Instead, a strong security plan is dependent on the following:
- business model
- technology stack
- internal operations
- regulatory requirements
Despite the complexity of security planning, companies can focus on some aspects that can establish a foundation. Examples include meeting compliance requirements or maintaining a certain level of risk. Regardless of the starting point, startups will still want to maintain a basic level of security to avoid a breach. They should also have a plan for how they will scale their security program as the company grows.
After outlining their cybersecurity must-haves, companies can then create their budget. The budget must align with the plan so that activities are prioritized based on an effort and cost model (so that the most urgent and most impactful tasks are prioritized over others with regard to their costs).
How much do companies spend on cybersecurity?
As TechCrunch highlights, “there is no easy answer” to this question.
That said, looking more broadly at the startup landscape, the latest studies suggest that companies spend around 10 to 15% of their annual budgets on cybersecurity. Yet, this can be a problematic benchmark for many new companies since business models and tech stacks vary greatly.
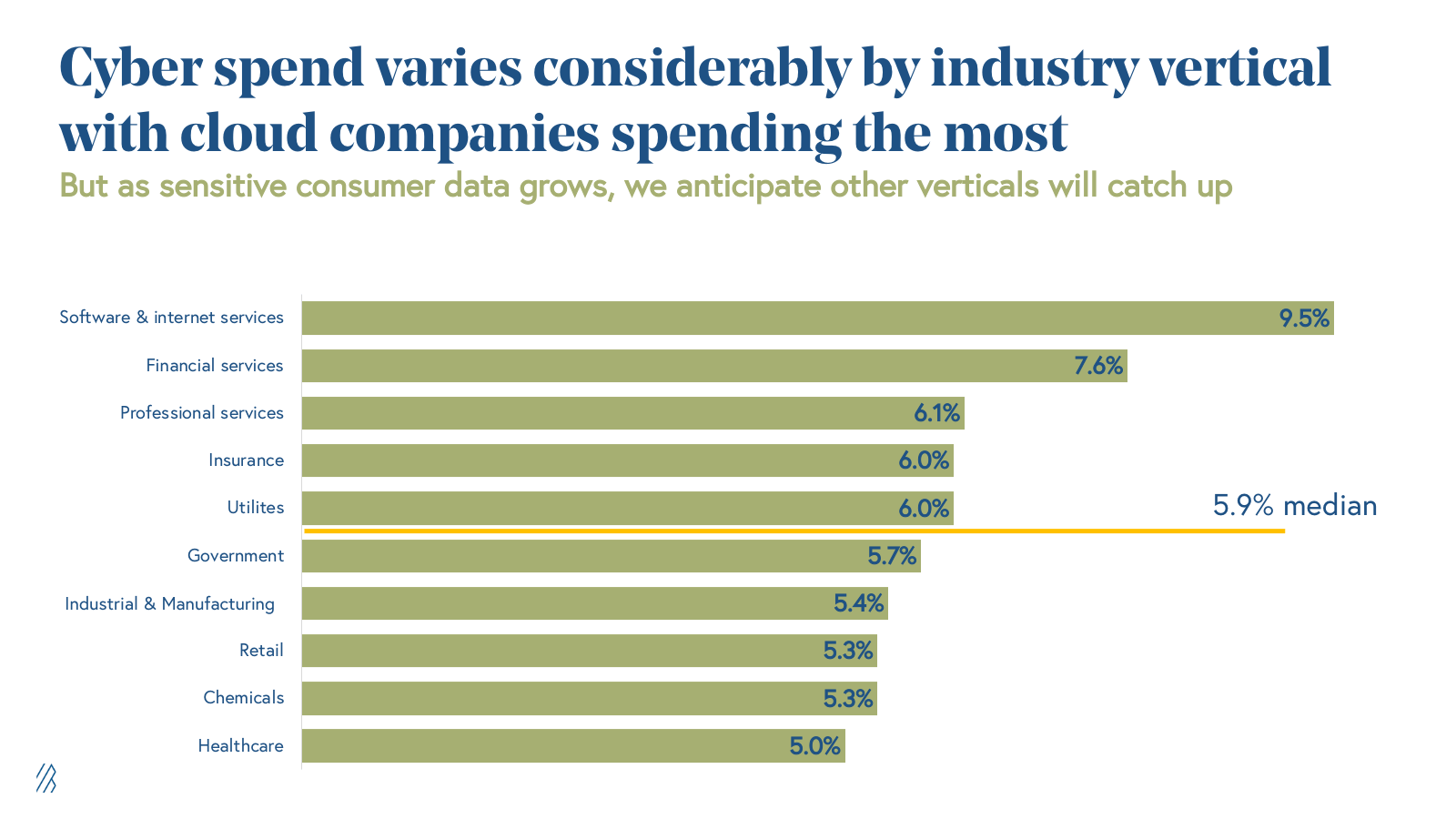
Companies can look at industry benchmarks which range from 9.5% of budgets of software firms to the lower band of 5% of budgets for healthcare companies. This top-down approach usually won’t work for a startup, though — their revenues are still multiplying, and their tech stack may be drastically different from legacy industry peers.
Different Approaches of Planning Cybersecurity for Startups
It’s important to note that there’s a big difference between a proactive and reactive security plan.
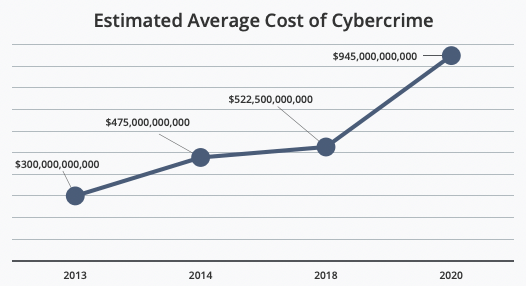
With cyberattacks costing companies over 11.5 trillion dollars each year and growing, even small companies and startups must proactively approach their security programs.
The risks of a breach are too high in the modern age to neglect cybersecurity.
There are different approaches to building a security plan that can work with smaller budgets. Let’s take a closer look.
Risk-Based Approach
A risk-based approach may be the best option for a startup, but it does require a strong understanding of your specific business and technology.
To complete a risk-based security plan, companies should aim to assign different levels of risk by mapping the likelihood of vulnerabilities being exploited and their potential impact on the company.
Next, companies can plan on how to address cyber threats based on their risk tolerance levels. After completing this exercise (again, this requires a degree of technical expertise to complete correctly), companies can assign mitigation plans to the necessary threats.
An important note when creating a risk-based cybersecurity plan is to account for the fast-changing nature of technology. Companies should include some form of monitoring in their security program and incorporate regular updates.
Drawbacks to a risk-based approach will likely surface based on each risk tolerance level. For example, if your risk tolerance is too low, the costs can soar. Conversely, if your tolerance is too high, then it can leave your tech vulnerable.
Compliance Requirements
Another common approach startups will take when setting a cybersecurity budget is to adhere to the required compliance frameworks, such as GDPR in Europe, California’s CCPA, and industry-specific requirements, such as PCI-DSS or HIPAA. The benefit of starting with a compliance certification as a baseline is that it can be explicitly mapped to costs. For example, companies such as SecureFrame offer turn-key solutions to achieve and maintain compliance.
While this can be a great place to start since it is the most common, it also has drawbacks. For example, adhering to compliance requirements doesn’t mean your company is 100% secure, and a breach can still occur.
Security evolves faster than compliance framework requirements. These are a good starting point but won’t necessarily propel companies to the required level of security. Therefore, understanding data security best practices should be a standard for all startups.
Data Security Best Practices
Endpoint Protection
Endpoint protection focuses on the perimeter of a company’s security, similar to a cellular wall. At a high level, this includes servers and devices with different approaches to safeguard these popular targets against attackers.
There are more than a half dozen different approaches to implementing endpoint protections, ranging from anti-virus software to more robust endpoint detection and response tools. For companies looking at this approach, endpoint security software exists to help centralize information and make it easier to digest and action.
Network Security
Similar to endpoint protection, network security focuses on the underlying infrastructure. Network security aims to monitor and prevent attacks against a company’s computer network or network-accessible resources.
Again, there are many different approaches to network security. Common practices range from a firewall to more advanced solutions such as an intrusion prevention system. Similar to how a company would select an application security policy, a network security policy can be established. At a high level, both are based on their tech stack, resources, and the nature of their assets.
Cloud Security
Cloud security is a critical aspect for startups to consider in order to protect their sensitive data and ensure the safety of their operations.
Implementing strong cloud security best practices is essential for safeguarding against potential breaches and cyberattacks.
Practical measures to implement for a start to secure their cloud environment include network security measures, maintaining up-to-date software, training the team on security practices to avoid phishing attacks, requiring strong passwords and multi-factor authentication, removing unnecessary data, scanning emails for malware, and properly backing up data to thwart ransomware attacks.
These practical tips can help startups and small businesses better secure their networks and ensure cybercrime doesn’t impact their business.
Breach Response Plan
A breach response plan is an important component for companies to be prepared in case the worst-case scenario happens — a breach. After a breach, things quickly become chaotic, and the need for a response plan becomes apparent.
Thankfully, the FTC guides how best to respond to a breach. After a breach, companies will likely have a million competing priorities, and a plan allows them to respond more strategically.
Other Security Basics
In addition to compliance or following data security best practices, other basic security measures should be taken into account. These include:
- Maintain up-to-date software
- Properly train your team (creating a security mindset within your company’s culture)
- Require strong passwords (Best Password Managers for Startups)
- Implement multi-factor authentication
- Remove unnecessary data
- Implement data protection best practices
- Scan emails for malware
- Properly backup your data
In closing, remember that even startups need to take a proactive approach to their information security. This can vary depending on your exact business with different levels of security, from a risk-based approach to meeting compliance certification requirements to a more straightforward set of best practices.
Overall, it’s important to remember as your company grows, so will the threat from cybercriminals. Through this, most companies will reach a point in their growth where it makes sense to partner with a cybersecurity company to decrease their security risks.
For companies interested in improving their security posture, consider turning to Cobalt and our trusted security team. Our innovative Pentest as a Service (PtaaS) platform makes pentesting easy. Further, Cobalt offers a variety of cybersecurity consulting services to help improve your security posture.
Sources
- https://techcrunch.com/2020/02/20/how-much-should-a-startup-spend-on-security/
- https://greyjournal.net/hustle/work-tech/startup-cybersecurity-threats-spending
- https://www.bvp.com/atlas/2022-cybersecurity-startup-trends
- https://www.ftc.gov/business-guidance/resources/data-breach-response-guide-business
- https://www.forbes.com/advisor/business/software/best-password-managers/









