Git is great versioning system that I am actively using while doing some development.
Few days ago, Osanda Malith told me that during pen test he found one domain have .git accessible through the web and asked me if we can get location of remote repository and see what we can do with it.
I was introduced to GIT at my previous job where I worked as Junior Developer which helped me to understand how it works. Shouts out to you guys!
Since there was only directory listing in .git main folder, but not in sub-directories this gave me hard time figuring out how GIT works under the hood and where is it saving commits, branches, diffs…
So I initialised local GIT repo to help me understand It’s structure. The starting point was when I found hash of master branch at:
.git/refs/heads/master
be42b85add97345e653f65e2556abc1b4372480b
I knew I have to find this hash file somewhere because I saw these files with hash names before. Doing quick search for the master hash from my local repo. Found nothing, ok. How about searching half of the hash? Bam, it worked. Hash file was found in:
.git/objects/be/42b85add97345e653f65e2556abc1b4372480b
Notice how first 2 bytes of the hash are being separated and rest of the hash is saved in that directory. That hash file must be saved in the same location at your local repo.
Great, so I downloaded the commit and now I can read the source or whatever? How about no!
Google to the rescue! After few minutes of looking at the results I found interesting one that might work: git-cat-file — Provide content or type and size information for repository objects
*git cat-file* (-t [--allow-unknown-type]| -s [--allow-unknown-type]| -e | -p | <type> | --textconv | --filters ) [--path=<path>] <object>
Let’s give it a shot!
git cat-file -p be42b85add97345e653f65e2556abc1b4372480b
tree fa4d5d060e1b0a76ee2649a7ceaa46e5a723d588
parent cf662496f73a9873a5325a003ef30d9fc8029e89
parent 9f8d8d9344e9edcfbfced76a4b736c9370099392
author XXX XXXX <XXXX@XXXXXX.XX> 1512147679 +0000
committer XXX XXXX <XXXX@XXXXXX.XX> 1512147679 +0000
Using the same technique I downloaded and read tree hash. Which returned list of files and directories from that repository.
git cat-file -p fa4d5d060e1b0a76ee2649a7ceaa46e5a723d588
100644 blob 91ba58f0299ff69b8fb2d4c0fa77ecdd123f8455 .env
100644 blob ca7fe338024f6dad049c2769d9aa44bea5cfb764 .gitignore
040000 tree 6a2e95ee1372246c0cd05f5ac6d9e1fdd2f3b909 app
100644 blob 5c23e2e24fc5d9e8224d7357dbb583c83884582b artisan
040000 tree f658c50fe4cd32477bd0dc2adbb7560aaeb1477f bootstrap
040000 tree b48aa1eb866f320c6566bf20cf3e62cbd7c67047 config
040000 tree 6ac9219ea772c3322e73f2a440e37c8bb322ed0f database
100644 blob 9f5b9fd83339f1bab4c35884ccac05130867fc44 package-lock.json
Doing same technique again I downloaded .env hash file from
.git/objects/91/ba58f0299ff69b8fb2d4c0fa77ecdd123f8455
Into my local repo at same location. Reading from this object returned useful information including DB and SMTP authentication.
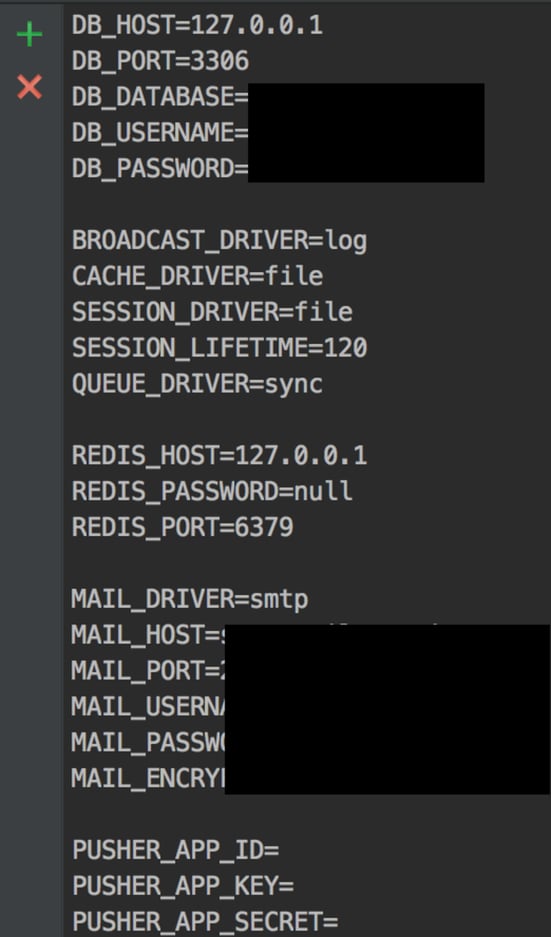
You can read every file from the work tree, you just need hash. All objects are saved in
.git/objects/<first_2_bytes>/<the_rest_of_the_hash>
Thanks to Osanda Malith for the idea of .git research.