Pentesting and ethical hacking consist of two similar, but very different cybersecurity practices.
To the average person, these two concepts appear identical. Yet, the reality is more complex. Pentesting is more specific and a subcategory of ethical hacking.
Ethical hacking offers companies a broader approach to identify vulnerabilities in their systems. Whereas, pentesting offers a more in-depth service specific to the assets tested, be it a web app, API or network
With this in mind, let’s dive into the definition of both pentesting and ethical hacking to better understand what each is. Then, present a better understanding of the differences between the two.
What is Pentesting?
Pentesting or penetration testing is the process of a trained cybersecurity professional attempting to breach specific computer systems, networks, or applications.
Through this process, pentesters aim to provide businesses with a proactive approach to their cybersecurity program. To do so, testers identify exactly how they breach a system and report this back to businesses — hopefully, to be remediated.
Pentesting Defined
Pentesting as defined by CSRC is “A method of testing where testers target individual binary components or the application as a whole to determine whether intra or inter component vulnerabilities can be exploited to compromise the application, its data, or its environmental resources.”
What Is Ethical Hacking?
While similar to pentesting, ethical hacking does not clearly define the assets to be tested. This key difference changes the coverage of the test and therefore, the confidence of the security vulnerabilities discovered.
Sometimes referred to as a white hat hacker, ethical hacking consists of professional information security practitioners attempting to break into a network or computer system. If a breach occurs, an ethical hacker will report it to the vulnerable company.
Another important note, ethical hackers have permission to breach a system before doing so, just as a pentester would. This draws a clear line between gray hat hackers and malicious exploits.
To better understand ethical hacking, consider a homeowner doing a 5-point inspection on a new home. This would cover the core aspects to ensure the property’s core systems are in good working order but wouldn’t be as inclusive as a dedicated and in-depth home inspection looking closely at each aspect of the home.
Ethical hacking helps provide broad coverage but doesn’t have the depth pentesting does, due to the lack of scope.
Ethical Hacking Definition
The experts at Search Security define ethical hacking as, “an information security (infosec) expert who penetrates a computer system, network, application or other computing resource on behalf of its owners -- and with their authorization.”
With this in mind, it’s easy to see how this broader term of ethical hacking could easily be confused with pentesting since both terms refer to penetrating a computer system or network.
While many certificates exist for ethical hacking, pentesting requires a variety of skills specific to the assets scheduled for testing. With this in mind, let’s take a closer look at pentesting ethics and how these two terms offer slightly different ethical perspectives.
How Does Ethical Hacking Differ from Pentesting?
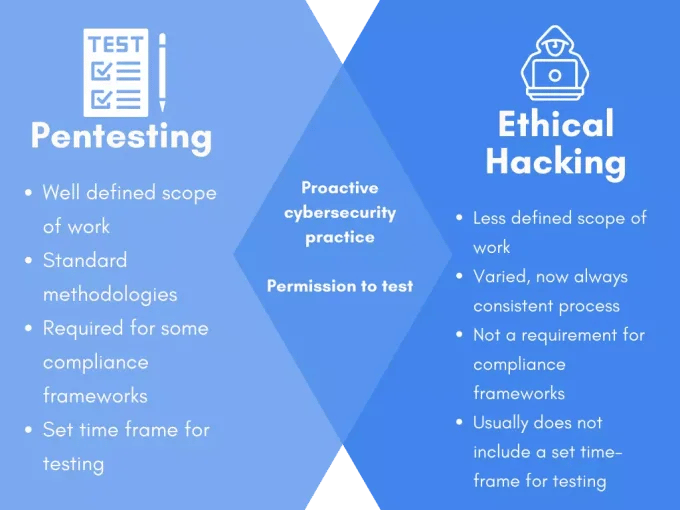
Ethical hacking differs from pentesting in a variety of ways:
- Pentesting clearly defines the scope of the test to a specific network or computer system.
- Ethical hacking utilizes any attack vector to breach a system whereas a pentest will often define the attack vectors more specifically before testing. For example, a pentest will often not include a phishing email attack, whereas an ethical hack may.
- Pentesting is required for some compliance frameworks whereas ethical hacking is not.
- Finally, while both services will often include a timeline for the attacks, ethical hacking will often function more similarly to a bug bounty program with no hard end date.
With these in mind, pentesting and ethical hacking offer companies a different approach to a proactive cybersecurity program. That said, they do not offer the same end-goals if those are more well defined, such as with compliance or to secure a specific system.
In closing, learn more about Cobalt’s highly-vetted pentester community and how they can help secure your computer systems by identifying vulnerabilities. The Cobalt Platform offers a diverse range of experienced pentesters and across various technology infrastructures.
The Cobalt Pentest as a Service (PtaaS) Platform offers companies a faster and easier-to-use approach to pentesting. With a PtaaS platform, we combine the advanced skill set of human testers with modern software solutions to create a modern pentesting experience.
Get in touch with our team of experts for an efficient, scalable pentest program!