As a pentester, I like to look for ways to leverage automation so I can focus my efforts on bugs that are hard to identify using automation. Things that only humans can find. Typically, during a pentest engagement, the pentester has a limited time of around 2 weeks. When testing large scopes, it can be a challenge to perform in-depth testing without missing issues. Therefore, it is essential to automate testing where possible using different pentesting tools or scripts.
In this post, I will demonstrate how one can use open-source tools from ProjectDiscovery in a typical network pentest. ProjectDiscovery is an open-source group developing essential tools needed in the security workflow.
Reconnaissance
During an external/internal network pentest, I use naabu to perform network reconnaissance. It is a port scanning tool written in Go that allows me to quickly and reliably enumerate valid ports for hosts. I start by providing the list of hosts to naabu for the full port scan. Here, I am running a full port scan with the -verify flag to avoid any false positives.
After that, I pipe the results to another tool called httpx, a fast and multi-purpose HTTP toolkit that allows to run multiple probers, making it easier to identify critical assets to focus on. While the scan is running, I manually test the hosts with interesting titles. Here, I am using httpx to print our title, status code, web server, and brute vhost from a default wordlist.
Vulnerability Assessment
Next, I pipe the httpx output to Nuclei, which I think is one of the best security tools out there. Nuclei is used to send requests across targets based on a simple YAML-based template and supports various protocols, including TCP, DNS, HTTP, File, etc. With powerful and flexible templating, I can model all kinds of security checks, including workflows, with Nuclei.
During my last pentest engagement, I ran the public templates from the nuclei-templates repository, which are contributed by the community. It currently comprises 900+ templates, including recent CVEs, default-logins, misconfigurations, etc.
Now putting it all together:
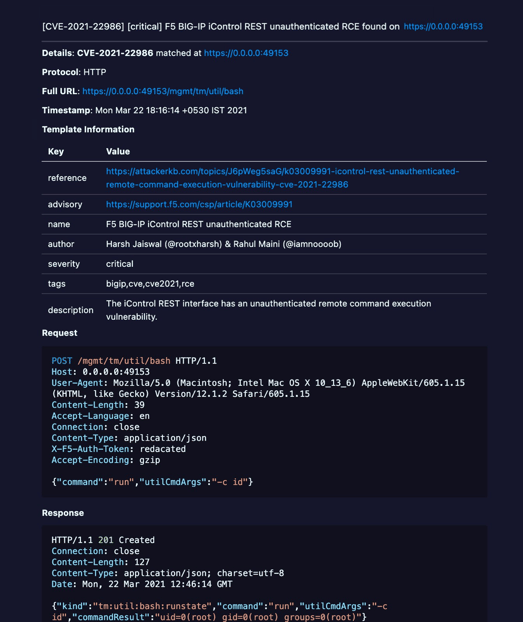
Here are a few findings from my recent pentest, which I found by using just a few open-source tools. Nuclei was able to identify quite a few low to high severity issues.
Nuclei has a dedicated repository that houses various templates for the scanner. The templates are regularly updated by the community, and you can check out these templates.
We can also use a flag named-tags to run a scan for a particular check. For example, the -tags cve2021 will only run the scan for the latest CVEs, -tags dlogin will run the scan for default login credentials.
Writing your own unique templates helps you to create more personalized checks for future pentests. I usually write nuclei templates for the issues I have found manually. Scan the entire range using that template to find more vulnerable hosts.
With Nuclei we not only can build templates, but we can also write our own workflows to run when Nuclei detects a particular technology or the network meets a specific condition. For more workflows, see the Nuclei workflow library.
If the testing scope is huge, I also use notify after running Nuclei on my VPS instance to send notifications on Discord or Slack every time Nuclei identifies a new vulnerability while I am performing manual testing on the side.
Reporting
Nuclei also comes with a reporting module that allows you to create tickets automatically on different platforms like Github, Jira, etc. I use the -disk-export flag to save the report of found issues in that pentest directory along with -include-rr flag, which saves all the requests/responses in the markdown report, which comes in handy when reporting the vulnerability to the client.
Takeaways
Automation and manual testing should go hand-in-hand to maximize the coverage and yield a complete and successful pentest engagement. We should automate repetitive tasks in order to free up time for identifying critical issues.
All known CVEs and misconfigurations like phpinfo files, default credentials, etc. can be easily identified and reported by these tools. There is no way automation can replace the job of a pentester anytime soon, but until then, we should leverage the power of Intelligent tooling.