Are you a Pentester or a Red Teamer? Or are you both? What even is the difference? Core Pentester Saad Nasir works with Cobalt as a Pentester and at SolarWinds for their Red Team Operations. In this blog you'll find him explaining:
- What Red Teaming is
- What Pentesting is
- How are they different?
What is a Red Teaming?
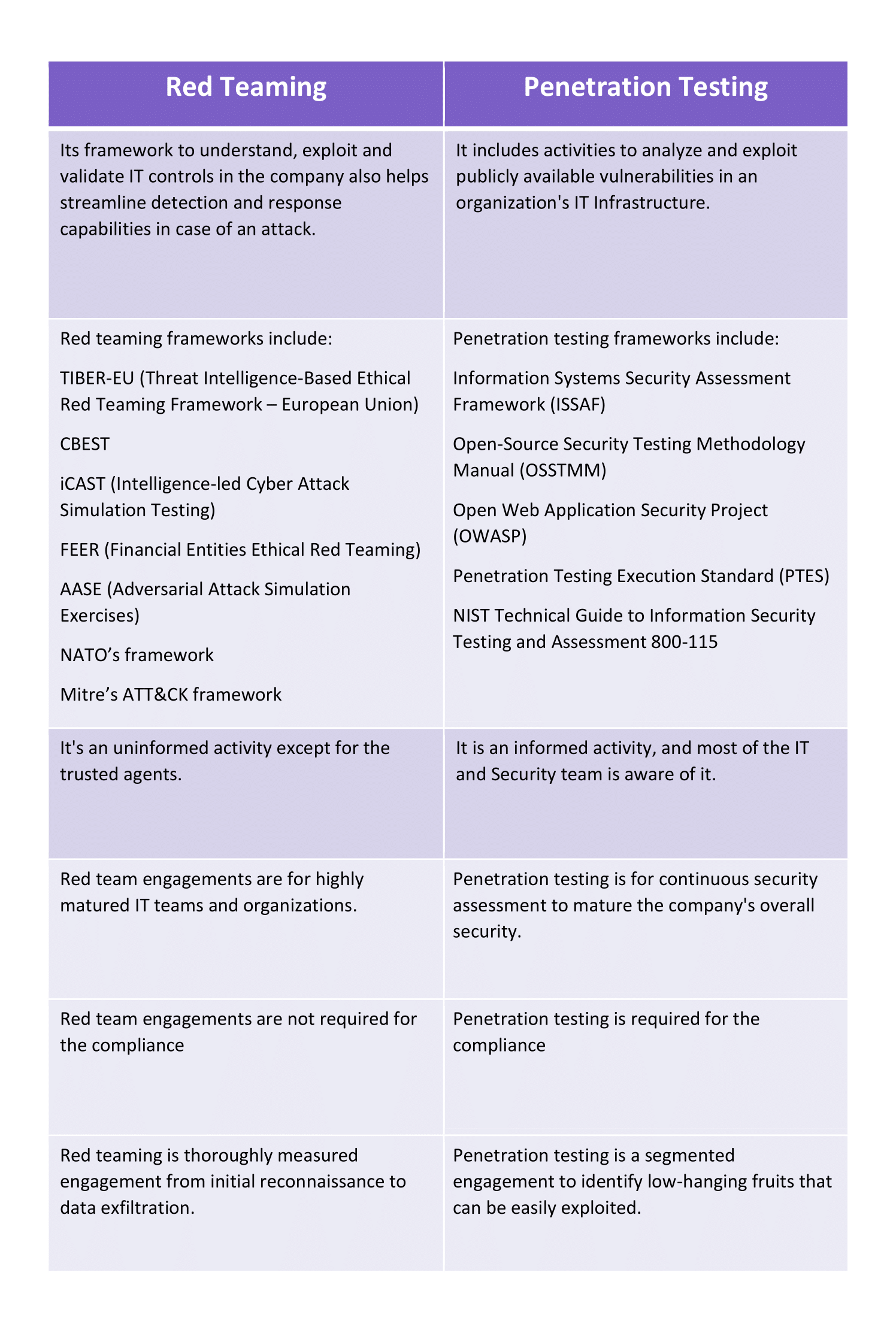
The term red team, by all accounts, came from the cold war when red was used to represent the Soviet Union in western countries. Today, red teams are still used in the military, extending their operations to cyberspace, but they have also seen wide adoption in the industry. Enterprises in the sector provide several red team services that often mirror penetration testing and even vulnerability assessments, with marketing guiding classification.
Red teams go after real threats, execute cyber-attacks to validate an organization's security controls, and share their experience with its defenders. Red teaming is pretty much similar to penetration testing, but both engagements have a different set of goals.
What is a Penetration Testing?
Penetration testing is an activity in which the Penetration Testers perform the security testing of an organization's IT Infrastructure (Applications, Networks, Hosts, etc.) with the organization's permission. The penetration testing scope of work is defined and agreed upon between the Pen Testing Service Provider and the Client.
Penetration Testing focuses on exploitation; it uses attack methodology to validate the security controls and defects in the target infrastructure. Penetration testing methodology against any target remains the same. However, the security frameworks may differ (for instance, pen testing a web application will require OWASP security weakness validation).
The objective of penetration testing is to find the security loopholes within an organization's infrastructure, explain the risks associated with the identified security weaknesses and provide proper recommendations for mitigating the identified security vulnerabilities.
How is Red Teaming Different from Penetration Testing?
A Penetration test involves a set of ethical hackers who are asked to perform security testing of an organization's IT Infrastructure (Hosts, Applications, Networks, etc.) with no element of surprise.
In penetration testing, the blue team of an organization is pre-formed about the pentest activity and continuously monitors the activities the pentesters perform on the in-scope assets. The blue team constantly monitors the pentesters' activities since they know the penetration test. Therefore, the blue team is ready to mount a defense.
A red team goes one step further and appends social engineering with an element of surprise. Unlike penetration testing in Red Teaming, the blue team has no clue about the red teaming activity. The primary purpose of not apprising the blue team is to validate the organization's threat detection and incident response capabilities against an actual world cyber-attack. The blue team is given no warning of the red team and will treat it as an intrusion.
Red-team assessment is similar to a penetration test but is more targeted. A red team aims to test the organization's threat detection and incident response abilities. An offensive red team will try to get in and access sensitive information in any way possible and remove their traces of penetrating the target systems.
When it comes to cybersecurity, there are different approaches to ensuring the protection of an organization's assets. These include offensive cybersecurity, often referred to as red teaming, pentesting or other services and then there is defensive cybersecurity, such as with antivirus software, intrusion detection software, or other tactics. Learn more about the differences between the two with an overview of offensive versus defensive cybersecurity tactics.