Remote code execution (RCE) is a vulnerability that allows attackers to remotely execute commands on a server over the network, without the need for direct access. For example, one common way attackers exploit websites is through file upload features. It's essential to ensure file uploads are handled securely, as a mistake here can lead to complete system compromise.
Below is they types of attack vectors leading of how RCE can be achieved:
- File Upload: Depending on the execution environment supported by the web server, attackers might gain code execution by uploading a malicious PHP or ASPX file.
- SSRF (Server-Side Request Forgery): Cloud Metadata and server-side PDF generators are examples of internal services that might be vulnerable to command execution via SSRF.
- SSTI (Server-Side Template Injection): Insecure use of templating engines can expose SSTI vulnerabilities, allowing attackers to run commands on the host system.
- Insecure Deserialization: When user-controlled data is passed into deserialization routines without validation, it can open the door to RCE, especially in languages like Java, PHP, or Python.
- CVEs (Common Vulnerabilities and Exposures): Depending on whether the target web application is using a vulnerable version of Apache Struts2, RCE might be achieved by exploiting CVE-2017-5638 through a crafted Content-Type header.
- SQLi (SQL Injection): In certain database configurations, a successful SQL injection can go beyond data extraction and be leveraged to execute system commands, ultimately leading to remote code execution.
RCE in a Customer Website
Cobalt pentesters recently identified a critical RCE flaw in a customer website that allowed harmful files to be uploaded. Servers must verify uploaded files to ensure they are safe, but this step was missing. In this case, the website accepted files without proper verification. When a user uploads a malicious .aspx file, the server executes it automatically, causing remote command execution.
As a result, attackers could take control of the server, access private data, install harmful software, or even use the compromised server to attack others. Imagine an attacker gaining complete control over your business website and all its data. This worst-case scenario clearly shows why addressing such issues quickly is crucial.
How We Discovered and Demonstrated a RCE Issue
We started by logging into the application. Typically in penetration testing we explore all functionalities of the web application, and then map our attack path accordingly.
1. After exploring various functionalities, we tested the email creation feature, which allows users to attach images.

2. We prepared a test .aspx file containing a simple webshell, which we attached as an image .

3. Once we uploaded the file, the application provided us with a URL as part of the server response.

4. Upon opening this URL, we observed that the server executed our uploaded file. We confirmed this by executing basic system commands directly from our webshell on the compromised Windows server.
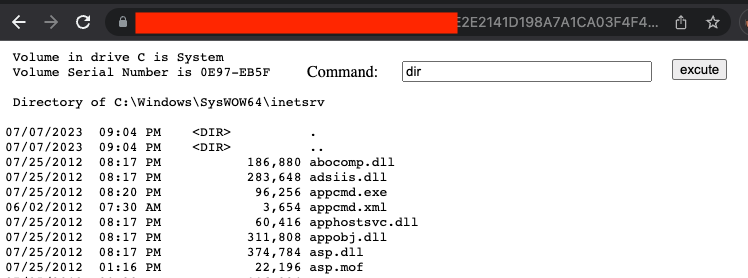
Figure 4: Webshell successfully executed, and commands are executed.
Initial Fix and Bypass Discovery
Initially, the customer’s development team responded quickly and attempted to block files ending with .asp and .aspx.
However, we continued testing and found this fix wasn't strong enough. We bypassed the restriction simply by adding an extra space at the end of our filename ("webshell.aspx "), proving the fix insufficient.
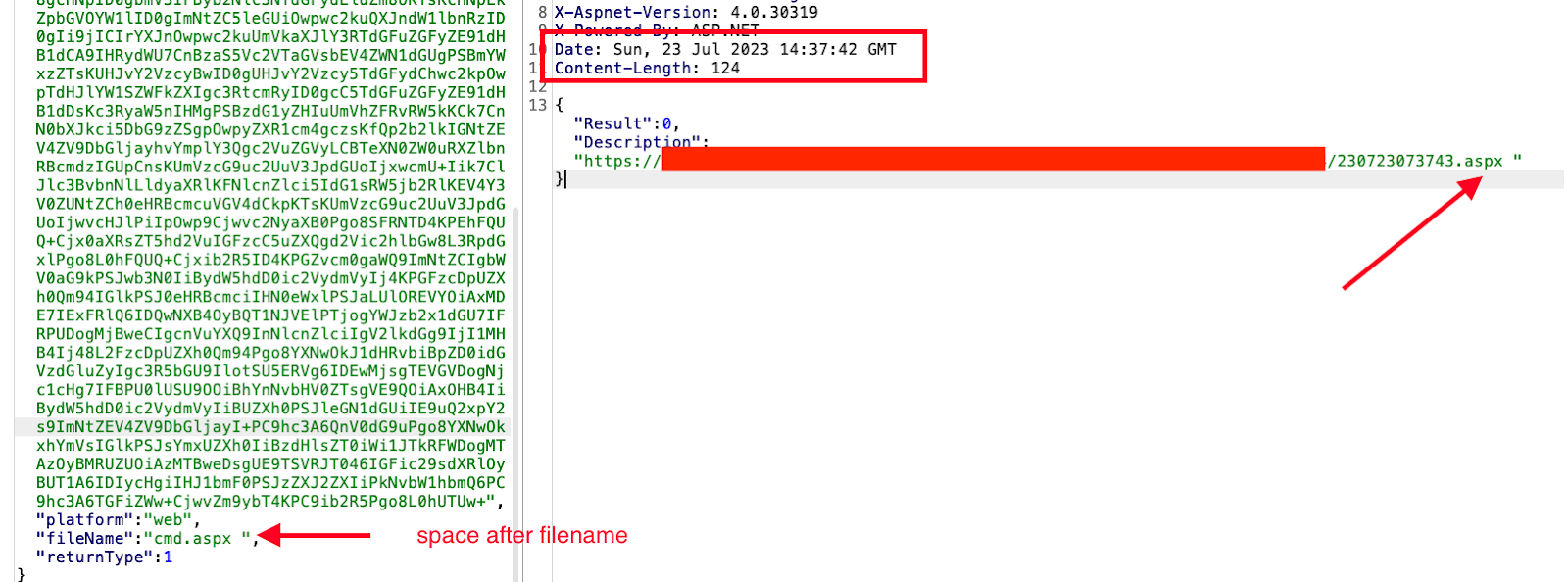
Figure 5: Bypassing the fix with ‘space’
Upon opening this URL, we observed that the server executed our uploaded file.
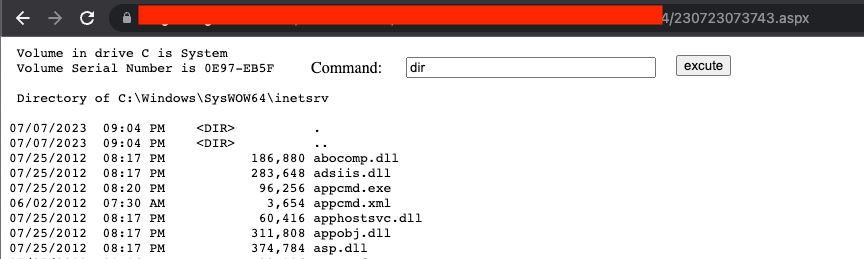
Figure 6: New webshell successfully executed, and commands are executed.
Recommended Remediation Solutions for RCE-Bypass
Using multiple security measures together is important because any single measure alone may not be sufficient to keep a service secure.. We advised the client to implement stronger security checks, including verifying the actual content of uploaded files, validating file extensions, ensuring strict file content-type validation, and securely configuring upload directories to prevent uploaded files from executing on the server.
We strongly encourage pentesters and developers to thoroughly test security patches and stay updated on secure coding practices. For more details on securely managing file uploads, consider exploring OWASP security guidelines or this piece of content on how to prevent remote code execution vulnerabilities.
Protect your web applications from critical threats. Discover the Top 5 Web Vulnerabilities and safeguard your digital assets with Cobalt's comprehensive offensive security services.










