With large amounts of data processed each day by IT systems and networks, it’s imperative that organizations know how to properly handle information privacy and security. Sensitive data is valuable information that must be protected from unauthorized access to protect the privacy of an individual or organization.
That said, “Sensitive data is defined as any information that is protected against unwarranted disclosure. Protection of data may be required for legal or ethical reasons, for issues pertaining to personal privacy, or for proprietary considerations.” (Services for Research)
Personal vs Sensitive Information
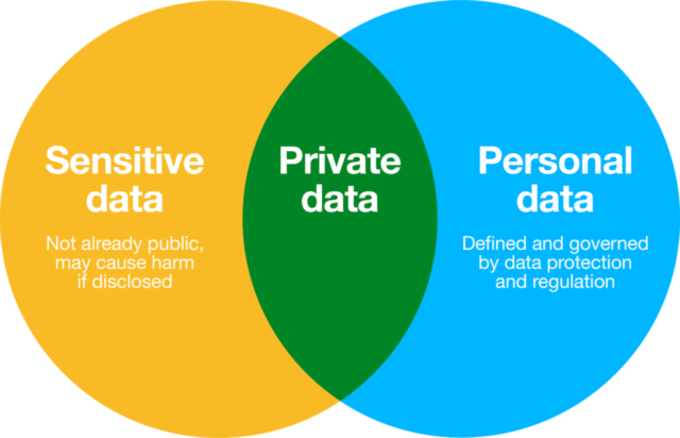
Image from Anonymisation and open data: an introduction to managing the risk of re-identification
Although sensitive information is a type of personal information, the consequences of releasing each type are different in scale. Privacy laws address and protect personal information, but they add an extra layer of assurance for sensitive data because, if revealed, can lead to discrimination or harassment. Sensitive information encompasses race, political affiliation, criminal history, genetic or medical-related information, and more.
3 Types Of Sensitive Data
The exposure of sensitive data is potentially harmful and can lead to major losses for organizations if the right measures aren’t taken to prevent unwarranted disclosure. There are three main types of sensitive information: personal information, business information, and classified information, with sensitive information examples that differ under each umbrella term.
Personal Information Personal information, also known as personally identifiable information (PII), links back to a specific individual and can be pulled together for identification purposes. Examples of a person’s personal information include:
- Driver’s license number
- Date of birth
- Medical data
- Social security number
- Phone number
- Bank account number
Business Information If business information is released to the public, competitors can use this type of sensitive information to their advantage. If your business has employees, it’s important to understand the type of information you collect, why you collect it, and how you can ensure this sensitive data remains protected. Examples include:
- Financial data
- Trade secrets
- Supplier information
- Customer data
Classified Information Classified information is restricted, confidential, secret, or top secret information kept private at a high or government level based on country laws and restrictions. Access to this type of information is only given to certain individuals with the proper authorization and security clearance.
Protecting Sensitive Information
There are a few things to keep in mind when determining the best course of action for storing sensitive data to maintain confidentiality, integrity, and availability for customers. Training and educating staff on the importance of data protection and best practices is key. A few best practices include following a compliance framework, using a VPN on public WiFi, encrypting files, and using password or passcode authentication.
First, it’s important to take inventory of the sensitive information collected by your organization and understand what types of data need to be protected. There are three essential categories:
-
Restricted: Data is on a need-to-know basis, and can cause major risk if released otherwise.
-
Confidential: Data that can cause moderate risk. Access is given only to employees or departments that require it.
-
Public: Data that can be easily accessible and causes little to no risk.
Failure to protect your network from internal and external threats opens the door for data to be compromised. Ensure the right controls are in place to manage data appropriately — achieving and maintaining compliance makes protecting sensitive data more secure and more manageable.
Adhering to the particular laws and regulations in your industry often involves certain certifications for compliance frameworks. For example, businesses that interact with sensitive data known as Protected Health Information (PHI) should be aware of the benefits of becoming HIPAA compliant. Another example is SOC 1 and SOC 2 compliance standards for companies operating under a SaaS model. These checks ensure businesses maintain privacy, security, availability, processing integrity, and confidentiality.
What’s Next?
Knowing your vulnerabilities and how attackers might exploit them to access data provides insights you can use to improve your security posture. Employing a Pentest as a Service platform delivers the insights needed to remediate risk quickly and innovate securely. To learn more about what security controls you have that are effective, how to meet compliance needs, and what next steps to take, learn more about Cobalt’s pentest services.