State of Pentesting Report 2025
Learn what 10 years of pentesting data and a survey of 450 security leaders tells us about the AI security gap, why pentesting is more essential than ever, and much more.






Legacy penetration testing doesn’t integrate into a modern secure development lifecycle. Pentest as a Service solves this problem and more.
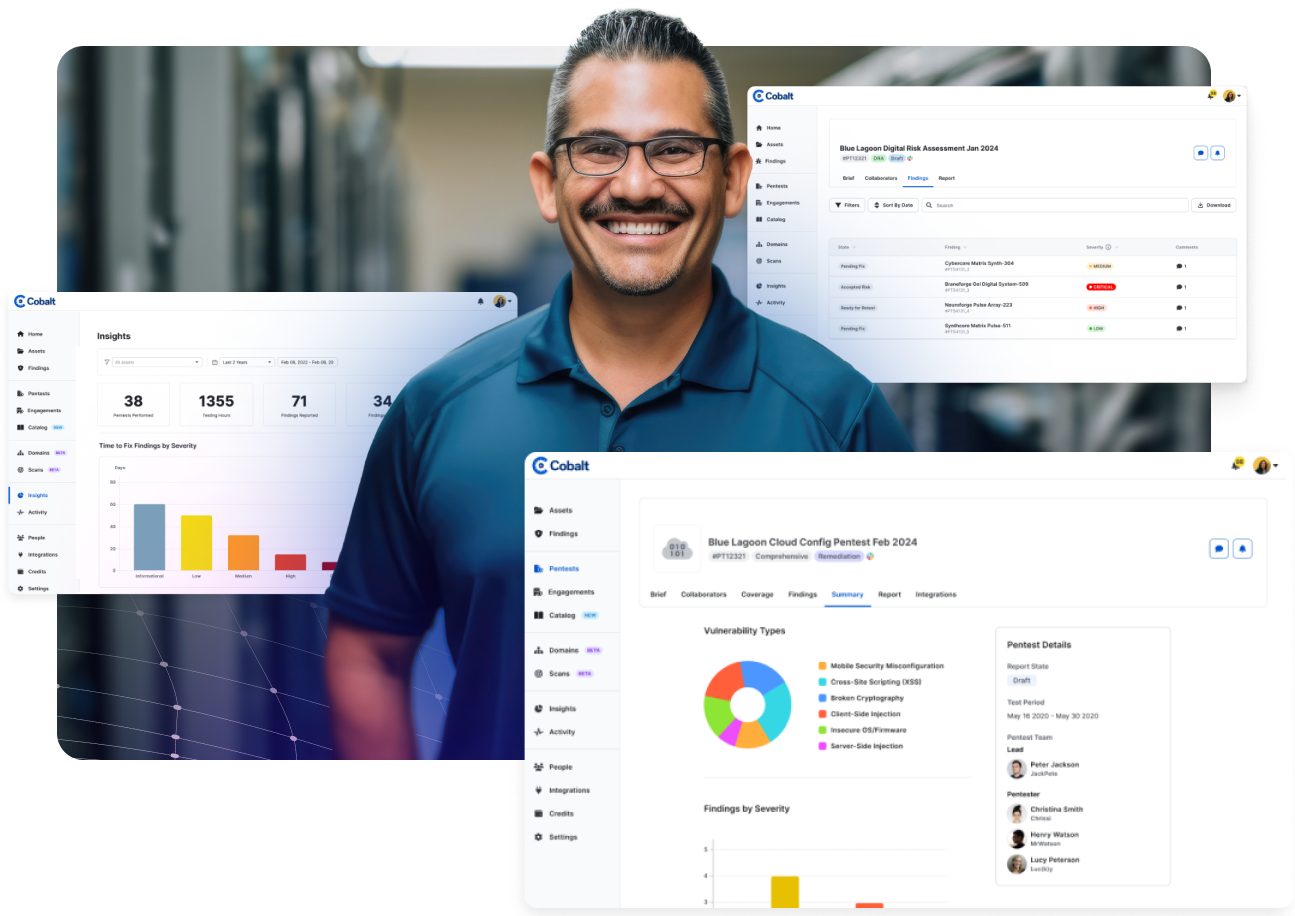
PtaaS eliminates the inefficiencies of traditional penetration testing, leveraging a digital platform for efficient and flexible testing with the ability to conduct multiple tests at one time while avoiding lengthy procurement processes to bring on new pentesters.
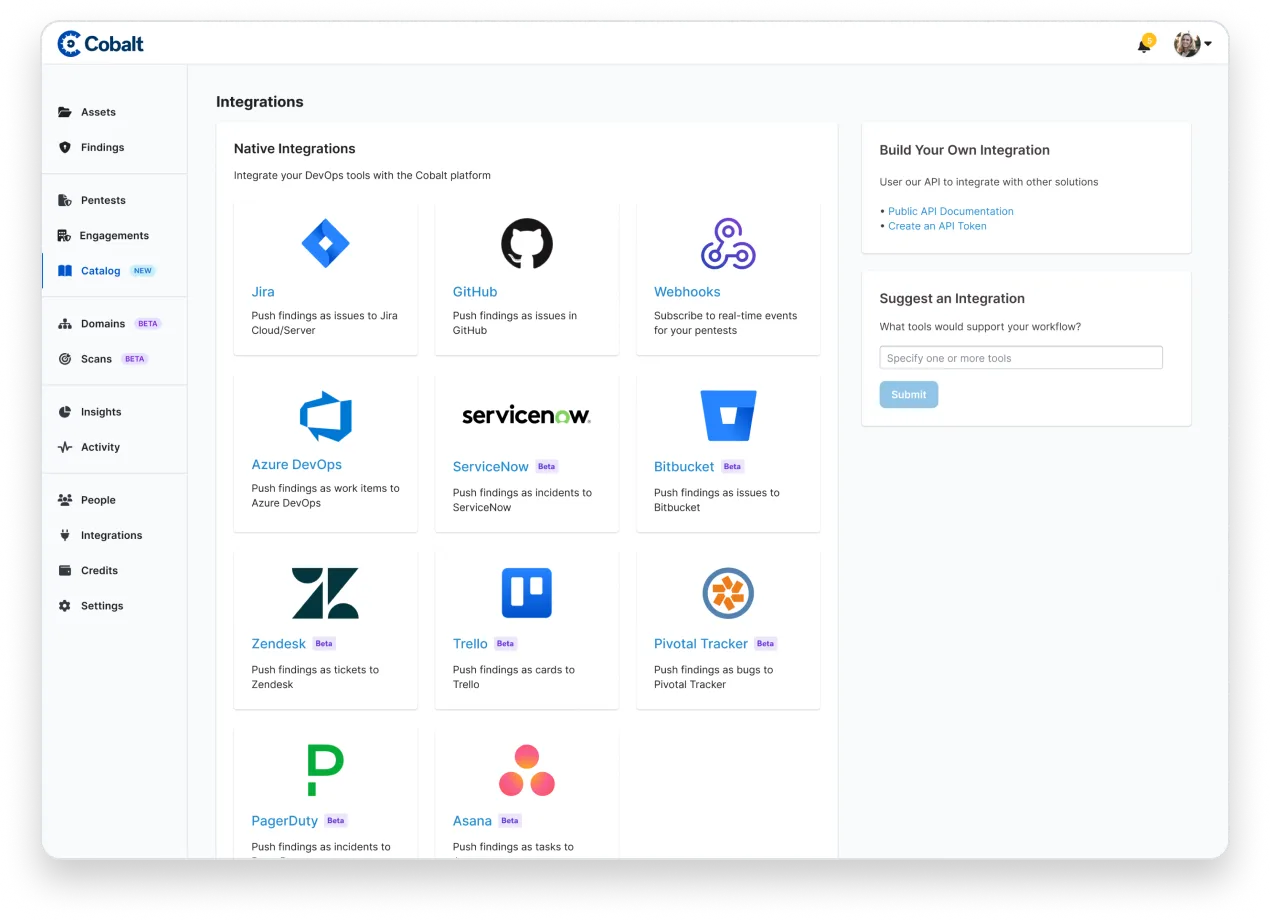
Seamlessly integrate with Jira, GitHub, or use the Cobalt API to relay the manual pentest findings to your development teams. Benefit from detailed insights and tailored fixes to remediate risks intelligently and strengthen security.
Avoid compromising between competitive pricing and human expertise. Circumvent the limitations of traditional pentesting and automated scanning solutions, ensuring thorough detection of complex exploits and business logic flaws with Cobalt's PtaaS platform and manual penetration testing services.
Launch new pentests rapidly with PtaaS and access to a pool of expert pentesters and the ability to start tests within 24 hours. Reuse stored asset data for subsequent tests and scale your security efforts effortlessly with our SaaS approach, catering to all testing requirements.
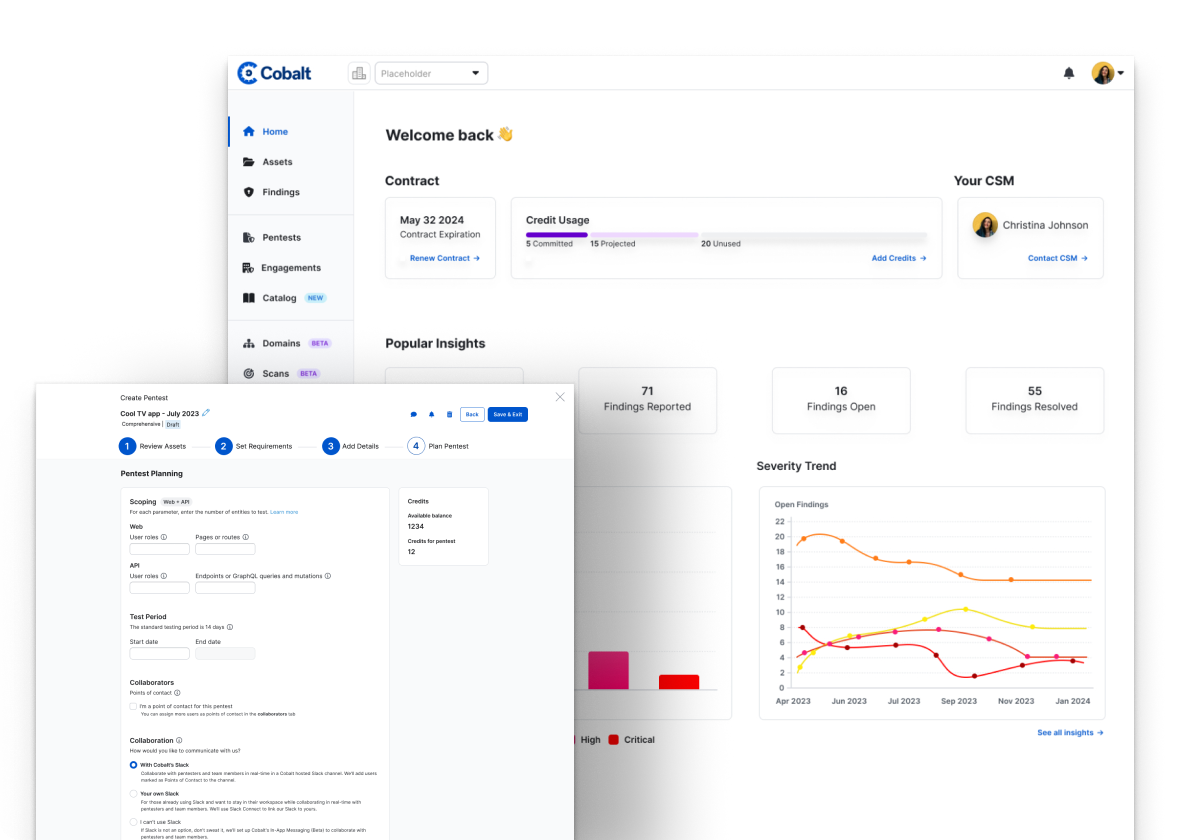
PtaaS brings data front and center, with advanced reporting that executive teams are sure to love. Businesses can actively monitor their tests' results over longer periods of time to identify trends, root causes, and opportunities for improvement. Better align with your SDLC by purchasing pentesting credits in advance and ensure you're able to quickly launch a test as needed.
Cobalt is transforming the PtaaS landscape with Dynamic Application Security Testing (DAST) and Attack Surface Management (ASM). In today's world, where businesses face a broadening array of cyber threats—from budding teenage hackers to powerful nation-states—the importance of proactive security measures has never been more clear. The evolving security environment demands that companies adopt continuous testing strategies to uncover and fortify against vulnerabilities.
Streamline your security posture with PtaaS. Seamless integration into existing systems, select from a fresh pool of pentesters to enhance your defenses without the red tape of procurement between each test, and track results in real time.
If you’re only doing compliance testing once a year, you’re flying blind to potential weaknesses—while pushing new code every day. With Cobalt, you can pinpoint vulnerabilities and accelerate time to resolution, whether you’re testing regularly or auditing once a year.
The Cobalt Offensive Security Platform brings together data, technology, and talent to resolve security challenges in modern web applications, mobile applications, networks, APIs, and AI & LLMs. From penetration testing to red teaming, secure code review, and more, we identify security issues across your entire digital footprint to help you better understand and eliminate risk.

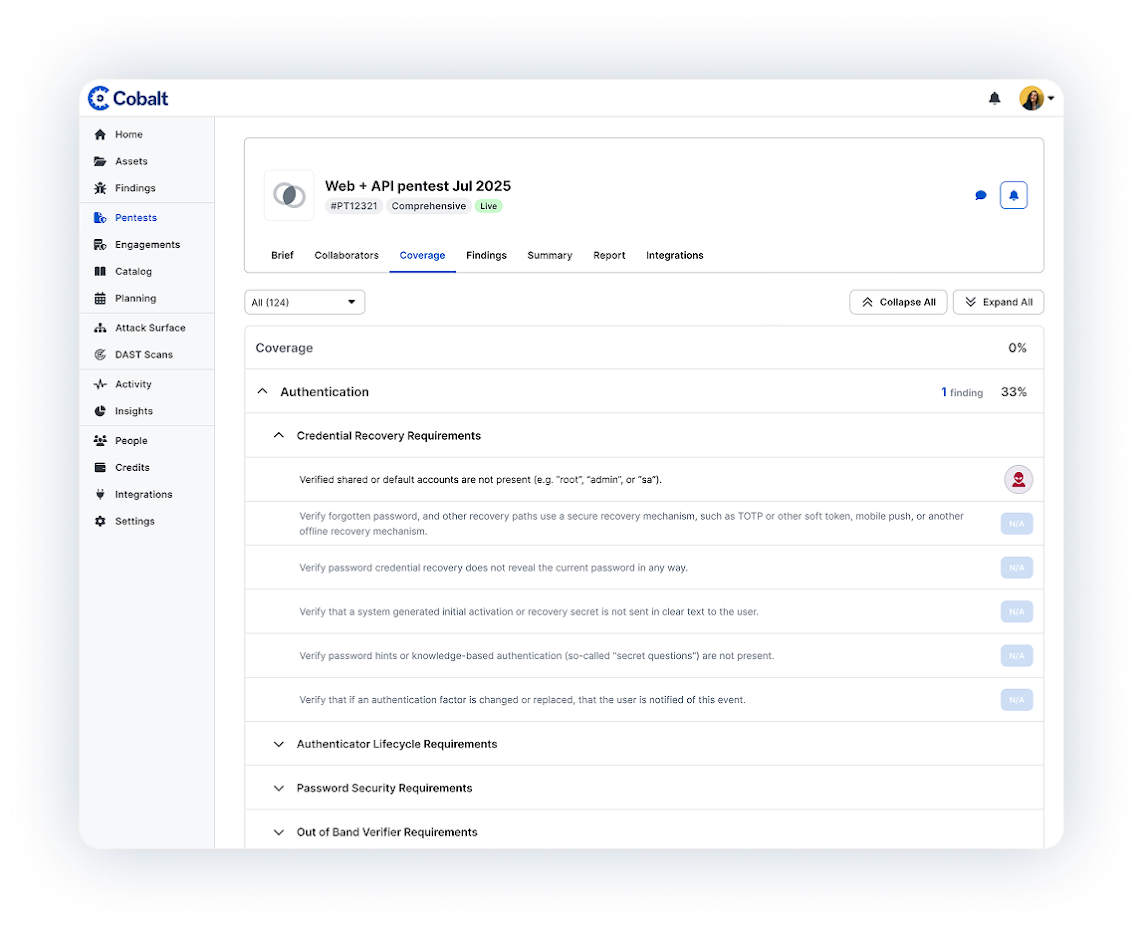
Map your attack surface to identify critical internet-facing assets for testing. Leveraging customer input, and automated Attack Surface and DAST scanning, we create a map of your environment so we know where to look for vulnerabilities.

Prioritize and scope your pentests to meet the desired goals. Cobalt helps you proactively plan out your annual pentest schedule, resources, and budget to ensure continuous coverage across your applications, networks, and environment.

Cobalt identifies domain experts with skills that match your technology stack. Your expert testers will analyze the targets for vulnerabilities and security flaws that could be exploited if not mitigated.

Take immediate action on high-severity findings while the test is ongoing. With real-time pentester collaboration and over 50 integrations, the Cobalt platform enables your team to start remediating vulnerabilities early, without waiting for the final report.

As vulnerabilities are reported and fixed, Cobalt Pentesters will verify the fix and update the final report. Every pentest includes free retesting of individual findings for either a 6 or 12-month period.

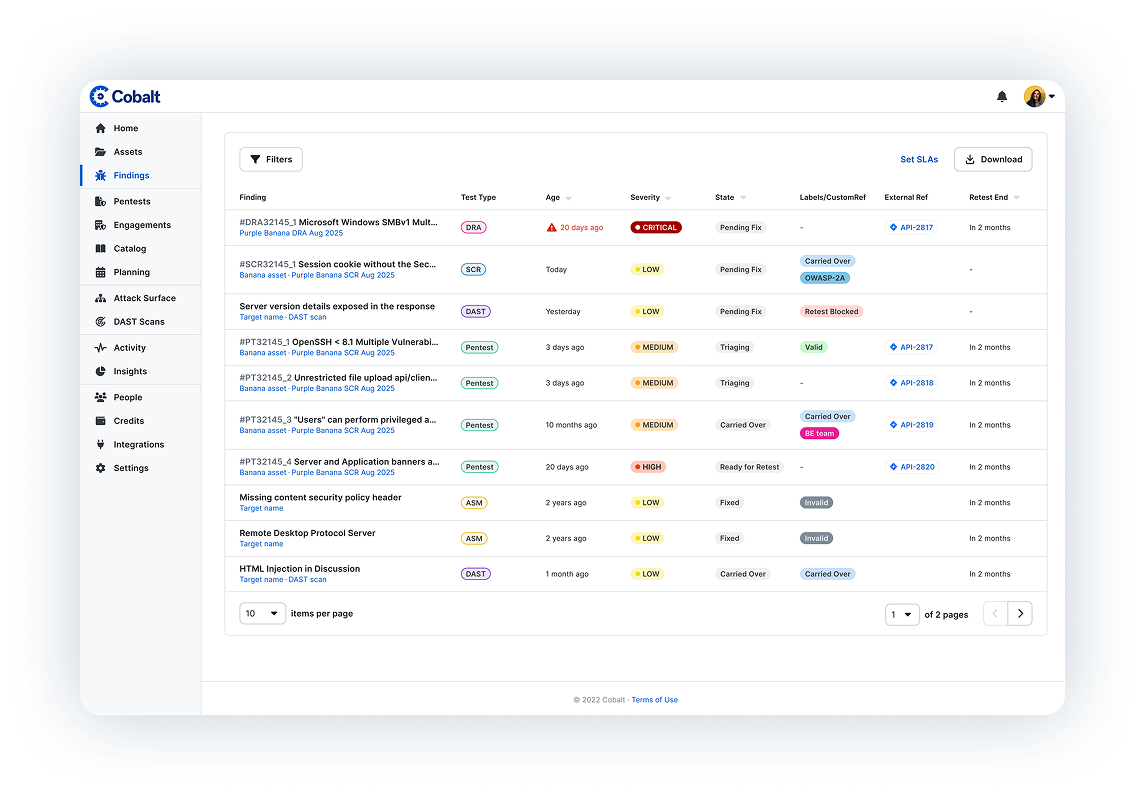
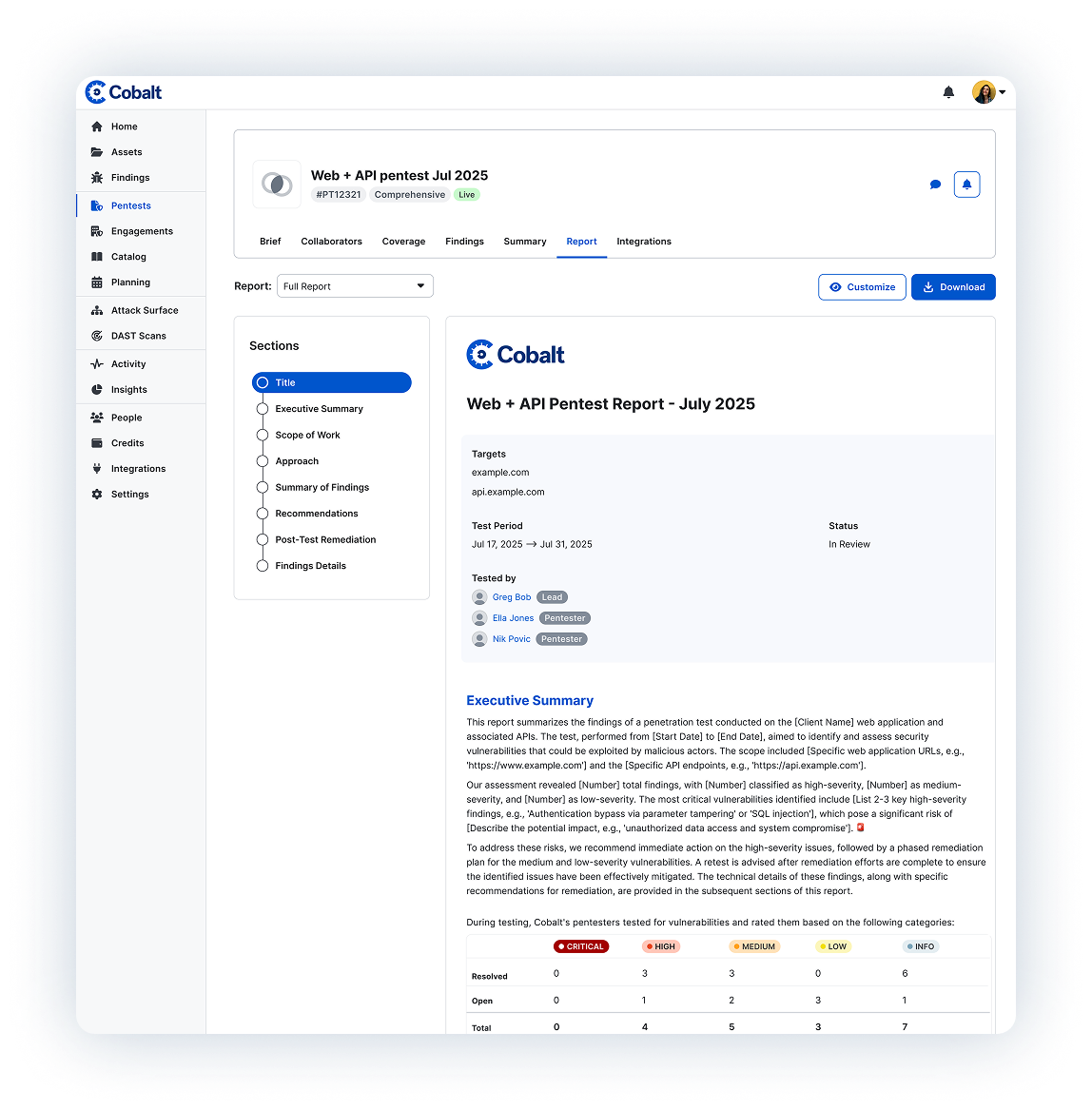
Show pentesting results with full reports including findings details, an executive summary, and customer attestation to fit the needs of your key stakeholders. With insights and analysis in the Cobalt Platform, you can track and improve your security posture and show progress over time.
Planning
and workflows
Collaboration
Collection and
Dissemination
of Information
Level 1
Level 2
Level 3
Level 4
Cobalt offers expansive manual penetration testing services with increased speed, a collaborative environment, integrations to speed up remediation, and complimentary retesting. Cobalt buckets pentests into two offerings: Comprehensive Pentesting and Agile Pentesting.
Comprehensive Pentesting encompasses all vulnerability categories across an asset. Primary use cases include compliance testing, customer requests, and M&A due diligence.
Agile Pentesting has a targeted scope focused on a specific piece of an asset or a specific vulnerability across an asset. Primary use cases include new release testing, delta testing, exploitable vulnerability testing, single OWASP category testing, and microservice testing.
Read more about the key benefits of PTaaS.
PTaaS brings together some of the best attributes of both security scanners while still leveraging human testers to investigate business logic. Learn more about the difference between traditional pentesting, security scanners, and traditional pentesting. Cobalt also offers a single complimentary DAST target for our platform users.
Customers using the quality at speed offered by a PTaaS platform can start a test in as little as 24 hours, depending on the scope of the test.
77% of IT security professionals say they don’t receive any findings from pentesters until the final report, which takes an average of 7 weeks. With this, companies report a reduction in time-to-results by 50% compared to traditional consulting engagements.
Yes, Cobalt offers a variety of offensive security services ranging from code review to digital risk assessments.


"When we first went with Cobalt it was purely for PCI requirements, but we were looking to scale our program and pentest on a more continuous basis. Cobalt gave us the ability to pentest on a frequent basis with minimum effort from our teams, saving us time and providing us quality results on a consistent basis."
Learn what 10 years of pentesting data and a survey of 450 security leaders tells us about the AI security gap, why pentesting is more essential than ever, and much more.
Discover insights from 150 security professionals on pentesting challenges, vendor satisfaction, and the urgency of adapting to AI and evolving threats. Download the report now.
Start testing in 24 hours. Connect directly with our security experts. And centralize your testing using the Cobalt platform. Trust the pioneers of PtaaS to optimize your cybersecurity across your entire attack surface.
