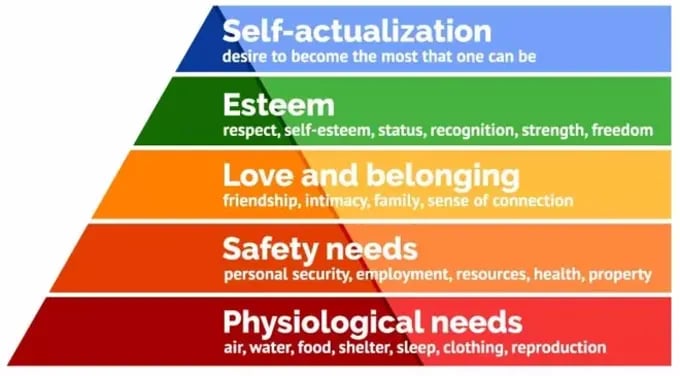
Maslow’s Hierarchy of Needs outlines the theory that human needs exist in a hierarchical structure. The hierarchy implies some needs as foundational and more important than others; while others higher up the pyramid are not as critical for survival. With the hierarchy, basic needs must be met before individuals can attend to the higher, more complex needs.
Attackers will utilize this knowledge, perhaps unknowingly, against the victims they exploit. Understanding the psychology behind these attacks illuminates ways to prevent them in the first place.
With this in mind, let’s take a closer look at Maslow's hierarchy of needs and how each need relates to common cyberattacks.
Basics of Maslow’s Hierarchy of Needs
Maslow’s hierarchy of needs segments into two easy-to-understand components.
-
Starting at the base of the pyramid, the deficiency needs exist. These needs required by humans for basic survival include food, security, and family.
-
While at the top of the pyramid lives the growth needs which consist of more complex desires such as psychological needs.
Looking closer at each category, the deficiency needs start with the basics of survival with physical needs for food, sleep, and water. Next in the hierarchy comes security and safety.
Moving up the pyramid, the needs become more complex with psychological needs establishing the next category. These consist of things such as belongingness with family and friends.
Next, esteem needs include aspects such as feelings of self-respect. Finally, at the top of the pyramid lies self-actualization, or the desire to reach one’s goals.
How does this psychological framework translate to cybersecurity?
With a bit of creativity, mapping the different needs from Maslow with examples from the security sector becomes possible and leads to insightful discoveries to be considered.
Maslow’s Hierarchy of Needs Real Life Examples in Security
Within the world of cybersecurity, different attacks align with the original hierarchy of needs Maslow created nearly 80 years ago. Many aspects of the hierarchy connect directly to the security challenges and hierarchy needed to solve these challanges today.
While this may be a metaphorical connection, the value here for security professionals lies in understanding the psychological motivation behind a breach. Furthermore, many examples center on individual attacks but it's important to remember that an exploited individual can lead attackers directly to a business to exploit.
While often motivated by money, we’re starting to see the rise of non-financially motivated attacks occurring. As these different motivators become more common, security professionals aware of the different end goals of an attack can better prepare their defenses.
Physiological Needs
Physiological needs consist of the necessities of human survival with such as food and sleep. If an individual finds it difficult to satisfy these needs, the deficiency in their life will be quickly and readily apparent.
For Maslow, he considered physiological needs as critically important. Thus, he ranked their importance above all other conditions after the primary physiological needs.
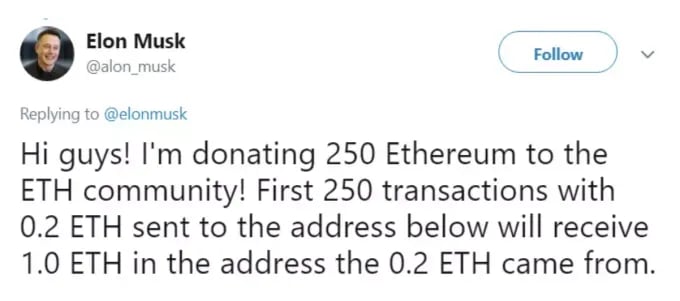
Attackers utilize this psychological understanding with attacks such as phishing attempts that promise a monetary reward. While not a direct connection to food or sleep, this monetary focused attack can jeopardize both for impacted individuals. One of the most common examples of this in 2021 comes from the Elon Musk Twitter scam where a fake (note the @alon instead of @elon) advertises a cryptocurrency giveaway.
Surprisingly these scams will generate tens of thousands of dollars, if not hundreds depending on how long the spoofing attempts remain live on platforms like Twitter.
Safety Needs
Once an individual fulfills their physiological needs, they can then focus on their physical needs for security, safety, and shelter. Naturally, people prefer a secure environment. Therefore, they opt for things that will help to fulfill this in their day-to-day lives.
Attackers utilize this knowledge by deploying scare tactics on users. These exploits often target senior citizens over the phone or email, informing them something tragic occurred to threaten their online security. The attackers will present themselves as the hero of the tragic situation and happily offer assistance in exchange for money or access to the individual’s computer.
Another good example here comes from when these types of attacks center around geopolitical affairs. Consider the attack on the Iranian Nuclear Power Plant in 2018 which shut down a nuclear facility. This attack shows how cybersecurity, or lack thereof, can quickly become a national security concern- jeopardizing the security of an entire nation.
Love and Belonging Needs
With primary needs met, the next step on Maslow’s hierarchy of needs is love and belonging. People are social creatures. Thus, the desire for things such as friendship, intimacy, acceptance, and love comes naturally.
Attackers, again most commonly with phishing attempts, will aim to exploit these innate desires. Impersonating others to build and exploit fake relationships, shows one common example from this category of the hierarchy.
As the world continues to become a smaller place with the prevalence of the internet and social media, hacks focused on love appear to be on the rise. If individuals online are not careful, they can become a victim of this type of exploit.
Esteem Needs
Self-esteem or respect for others brings us to the fourth component offered by Maslow. The need for self-care often precedes self-esteem or dignity. If you’re hungry, you tend to focus on that before working towards dignity.
To boost self-esteem or respect, sometimes people will try to take a shortcut which is where an attacker can take advantage. This occurs with fake traveling jobs as highlighted by HBO’s new show, Generation Hustle where unsuspecting victims accepted a fake job and were exploited through the work process. While these types of complex social engineering attacks are not common, they do occur and should be considered by individuals when a new opportunity sounds too good to be true.
Cognitive Needs
Moving further up the pyramid, the need for knowledge, understanding, and curiosity comes next. These needs stimulate the brain and help us strive for a better tomorrow than we had today- again a natural human tendency.
Attackers actually may fail more often than not with regards to this particular point. Oftentimes, critical thinking will stop a spoofing attempt in its tracks. While this isn’t the case with highly advanced attacks, it certainly remains true for simpler phishing attempts.
Sometimes, phishing attempts will purposely use misspelled words and poor grammar to sort through the receipts to find someone who didn’t notice these blatant errors, with the assumption that they are more likely to fall for the hack and become profitable for the malicious actor’s time.
Self-Actualization
Lastly, Maslow presents the desire for self-actualization or personal growth to reach one’s potential. This component offers attackers the opportunity to tap into the desire of progress humans embody with promises of fame or fortune.
This category presents more of a scam than an actual hack, with similarities to a traditional phishing attack. With examples from fake schools or degree mills which sell students educational services without any merit, self-actualization exploits tend to be less clear-cut than other phishing attacks. The FTC warns about these scams, noting that “Many bogus degree programs have well-designed websites and familiar-sounding names in order to seem real.”
In closing, understanding the psychological motivation behind an attack helps show ways to prevent them. With these insights, cybersecurity professionals can deploy the necessary security measures depending upon how vulnerable assets are from a psychological perspective.
While this exercise may not always lead to fruitful insights, it does so with many common attacks. With the new perspective, security teams empower themselves to make more strategic decisions.
At Cobalt, we help secure digital infrastructure by offering an innovative Pentest as a Service (PtaaS) platform where businesses can enhance their cybersecurity programs with pentesting.