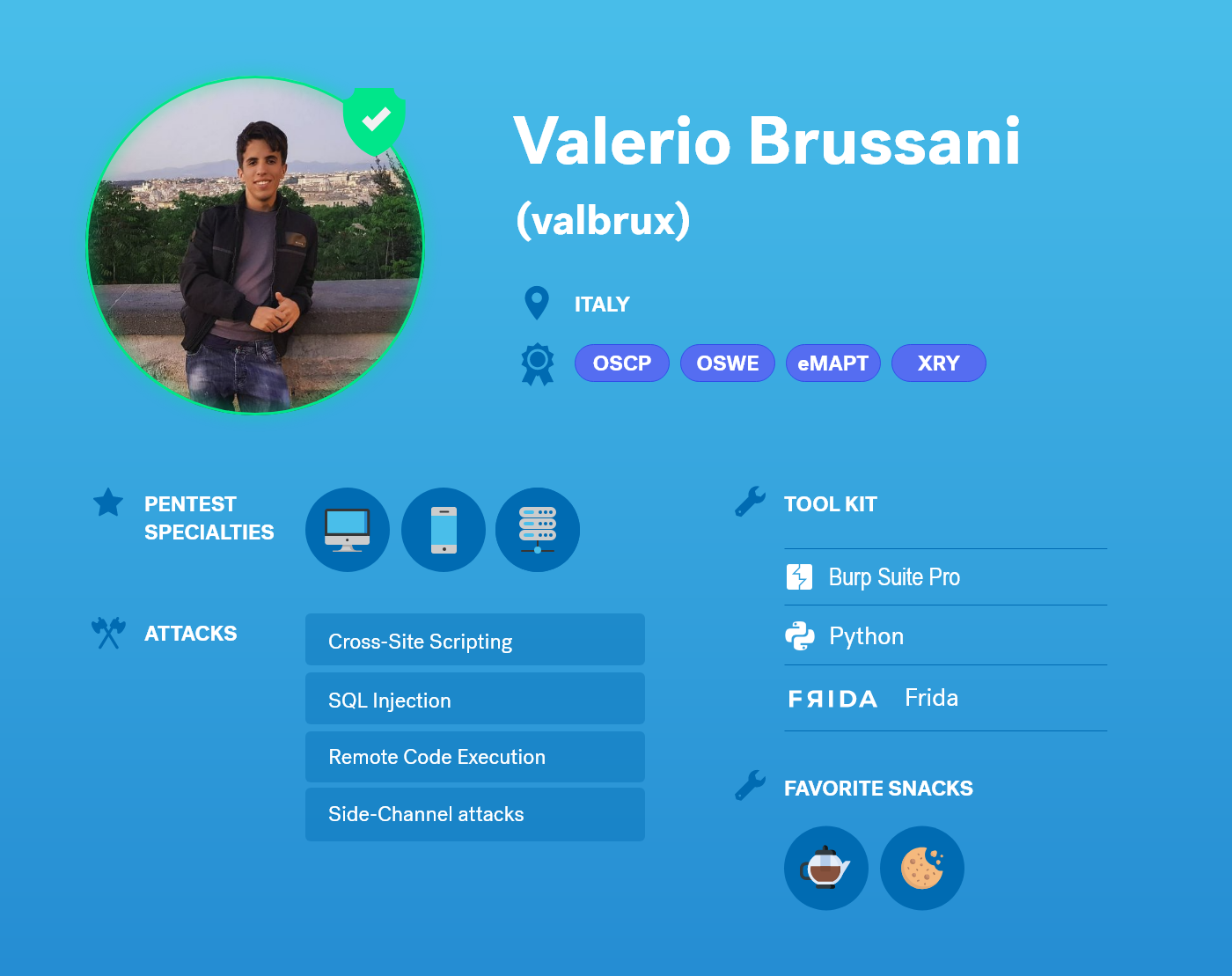
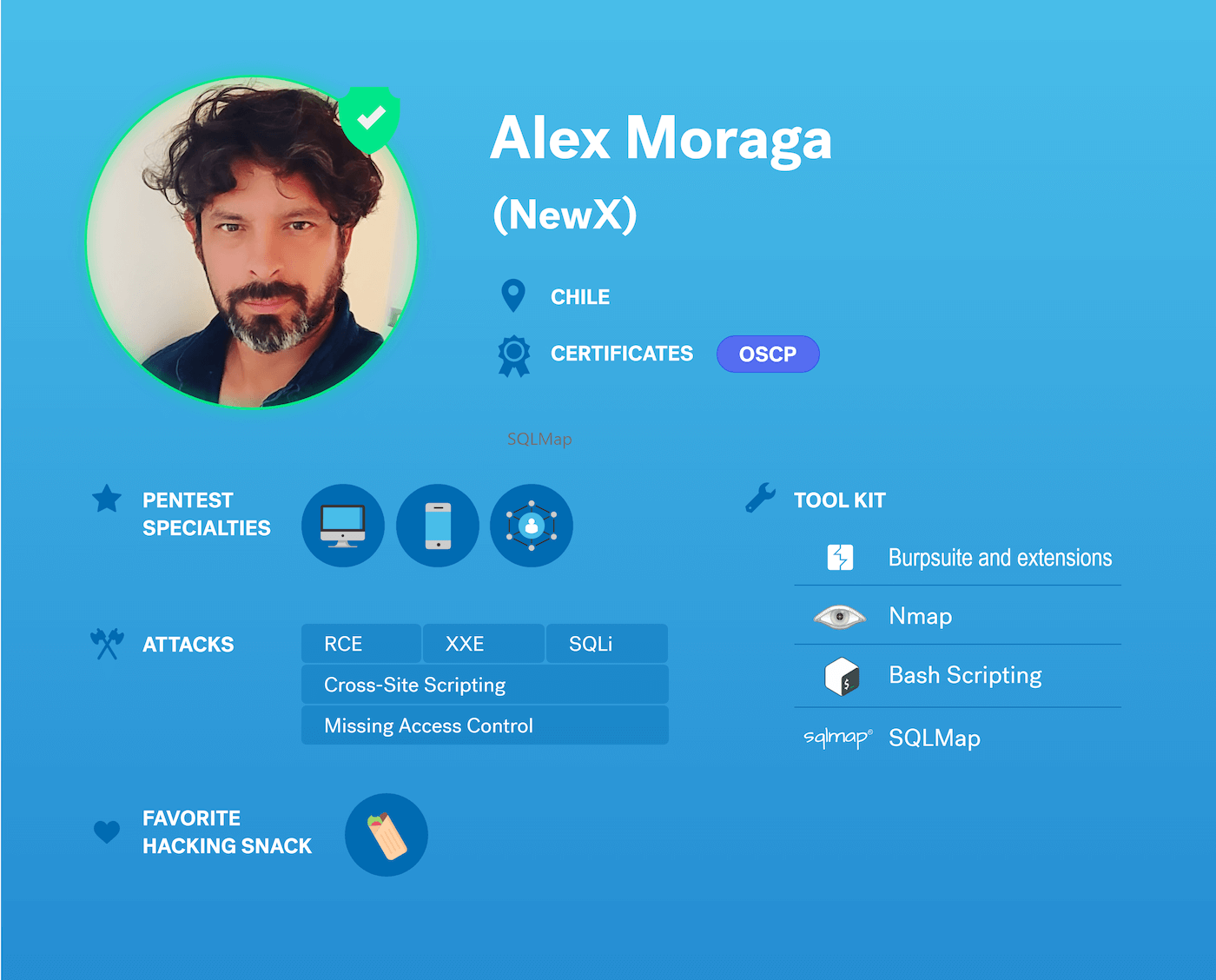
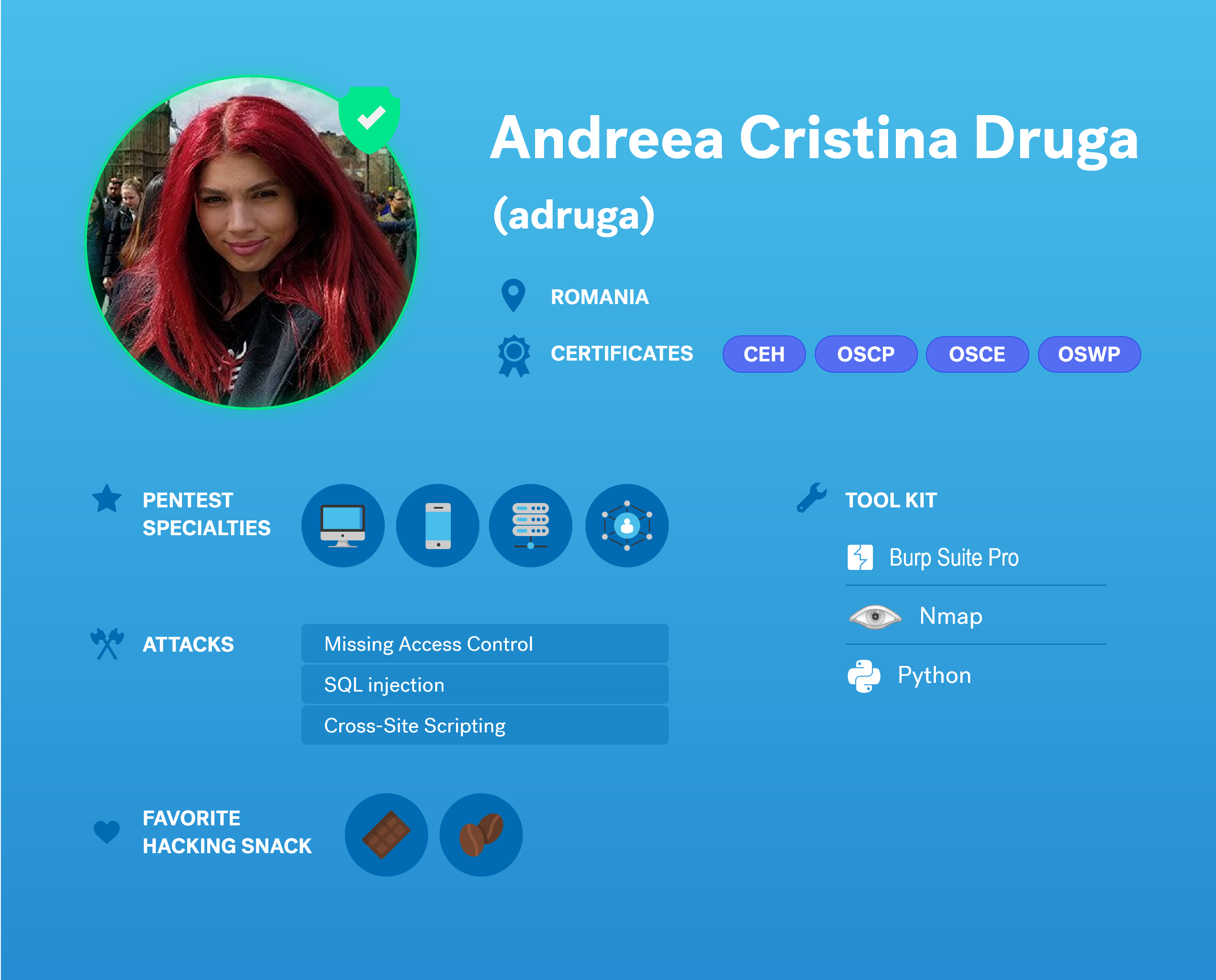
Martina Matarí joined the Cobalt Core, our highly-experienced, geographically-diverse community of pentesters, in 2020. She is one of the 270+ pentester worldwide who has helped Cobalt secure over 3000 assets.
We had a chance to hear from her to learn more about her pentester origin story and what she enjoys about being a part of Cobalt’s pentest community.
How did you get into security?
MM: I grew up surrounded by computers, although I didn't always have direct access to them. I'm the youngest of three sisters in a house where technology was always present. Truth be told, at the very beginning it was only available inside my father's study. That room was always locked and we were just able to (break things) go inside when my father was around there keeping an eye on us. But when my father went out to work, as the little hackers we were, we managed to open the lock with a knack from my sister Regina and a pair of hair pins. And there, waiting for us, was a computer with no other operative system than DOS, though for us, as you may imagine, it was like being inside the cybernetic worlds from TRON.
After a short time, my father, who knew about our not-so-secret fondness for breaking into his study, started to bring video games home. That which is still my favourite game of all time, "La Aventura Original" (a text adventure based in the “Colossal Cave Adventure”), arose my interest in learning how to program and code. I wanted to make my own video games. Thanks to a magazine, I learned that there was a system called DIV Games Studio which could help me achieve my goal, so highly determined, my sister Patricia and I went to an IT store to buy it. I don't know if you can imagine the scene, but it was rather funny. Obviously, that system wasn't available nearly anywhere in Spain at that time, but the shop assistant was nice enough to ask for it directly to the manufacturer. My sister and I created a game in which a huge Pikachu walked in the woods and when the walk finished, it went into a cave. The long-lost E.T. game for Spectrum had more plot and action than ours, but there it was! We had done it, it was our own game.
When I was thirteen I started to have contact with the Internet thanks to an after-school activity. But until I was fourteen we didn't have it at home. I remember that it was Saturday and my father was sitting on the stairs at my home's door, talking to my granddad. When he saw me going out holding my child savings book, he asked me about the aim of my trip with such an item. I told him that I was going to buy a router to take the Internet home. I believe he thought that I wouldn't be able to get money from that account, as I was under age, or maybe he was just curious on how all that would end, because he didn't ask me anything else. Two hours later, you could hear the scratchy sound of a router connecting the network of networks all around the house.
The arrival of the Internet at home opened a world of possibilities and knowledge awaiting to be found. My sister Regina found everything she wanted about poetry and Egyptology, my sister Patricia found all those games she always wanted but never had access to. And as for me, I found hacking.
Not knowing well how, I ended up enrolled in Izhal, a community devoted to hacking and wargames. Challenge after challenge I learned what being a hacker meant, that not everything was decided, that there is not just one way of seeing and doing things, and that collaborating with other pals was easier and more fun. And of course, my adventure didn't end there.
More than twenty years have passed since all that, now I'm a Certified Ethical Hacker, an Offensive Security Certified Professional, and I have eleven years of cybersecurity experience. I teach lessons on Hardware Hacking in several Universities, I offer workshops in Security congresses, and I have created a well-known project on Hardware Hacking in Spain. The road to where I am now, as any road ever gone through, hasn't always been easy to walk, but I can assure you it was worthwhile.
What motivates you when it comes to pentesting?
MM: Without a doubt, my main motivation is the challenge itself. Each pentest is a personal challenge that I take very seriously, and at the same time find it extremely fun at the same time. I have to admit that at the beginning of my career my motivation was somewhat different. When you are a woman in a predominantly male sector you want acceptance and respect from your colleagues, and in a pentest, that can be achieved with good findings. When you grow professionally and gain confidence in yourself, fears disappear and that's when you enjoy your work the most.
What does a good pentest engagement look like?
MM: A good pentest has as its main ingredients a target with a medium-high level of maturity (not a Swiss cheese, nor impenetrable) and some friendly colleagues with whom to share and learn along the way.
What are the top 3 traits that a pentester should possess to be successful on Cobalt?
MM: If I had to choose three essential skills to be successful at Cobalt, they would be the following:
- Have good communication skills. This helps information flow with both customers and colleagues, and leads to better findings.
- Know how to write good documentation on the findings. This makes it easier for the lead and customers to understand what happened and how the issue can be reproduced. The sooner it is understood, the sooner it can be mitigated.
- Be a team player. Individualism must be put aside. Asking for help or other points of view from your colleagues helps the project in every way and you will achieve better results.
How do you organize yourself during a pentest?
MM: I try to always follow the same schedule and methodology when I perform the tests. Obviously, each target is different and I can't always apply it 100%, but it helps me to cover the most important parts of the job.
What kind of targets excite you the most? Do you have a favorite vulnerability type?
MM: The targets that I enjoy the most are those in which I test new technologies. They add extra difficulty but make me study and learn more.
I really like vulnerabilities related to access control. They do a lot of reputational damage to companies so I always make a huge effort into finding them.
How do you learn about different security concepts? Where do you go?
MM: I admit that I am passionate about buying technical books, although I always end up googling on any type of topic to delve into it. On the other hand, I follow many technical accounts on Twitter, and technical feeds, which keep me up-to-date.
How do you conduct research and recon for a pentest?
MM: I tend to be very methodical in this part of the pentest. I love to take a few days before the project starts, in order to learn as much as possible about the target using passive methods. For each type of information that I want to obtain about the target, I have a series of favorite tools and websites that make it easier for me to collect information as, for example, Hacker Target, censys.io, FOCA, GitHub, ZoomEye, FOFA, or Shodan.
Do you leverage any tools? What are your go-to tools?
MM: If we talk about web pentesting tools, I love the classics. Burp Suite is a must in any arsenal worth its salt, and even more so when used in conjunction with Burp Bounty, the Burp Suite extension created by Eduardo Garcia. We can’t also miss tools like nmap, sqlmap, dirb or wfuzz.
What do you enjoy the most about being a part of the Cobalt Core?
MM: I love to feel part of such a multicultural community like the Cobalt Core. You can meet people from all over the world with whom you share interests. Also, the learning element is great, there is no pentest in which I do not learn new things from one of my colleagues.
What advice would you offer to someone who is interested in getting into pentesting?
MM: Never stop studying and learning new things. The key to success in this profession is to keep learning constantly. And please, don't be afraid to ask any questions, no matter how absurd the question may seem in your head.
What do you wish every company/customer knew before starting a pentest?
MM: I would love for them to know that they can express their main concerns to the pentesters. The more information we have about the target, the better we will do our job. Also, they are free to ask us for additional information on any of the findings. We are here to help, both during the pentest and during the retests.
What do you like to do outside of hacking?
MM: When I disconnect from work and computers, I spend as much time as possible with my family. In my spare time, I read science fiction books and play Oculus Quest. I have always loved video games, I enjoy the more classic video games (graphic adventures, conversational adventures, pixels the size of a coin ...) but with the appearance of virtual reality, I have fallen in love with video games again.
What are your short term and long term personal or career goals?
MM: My goal, both in the short and long term, is to become a better cybersecurity professional everyday. To do this, I train and test my offensive and defensive skills daily.
Learn more about how to become a pentester with insights from the Cobalt Core.