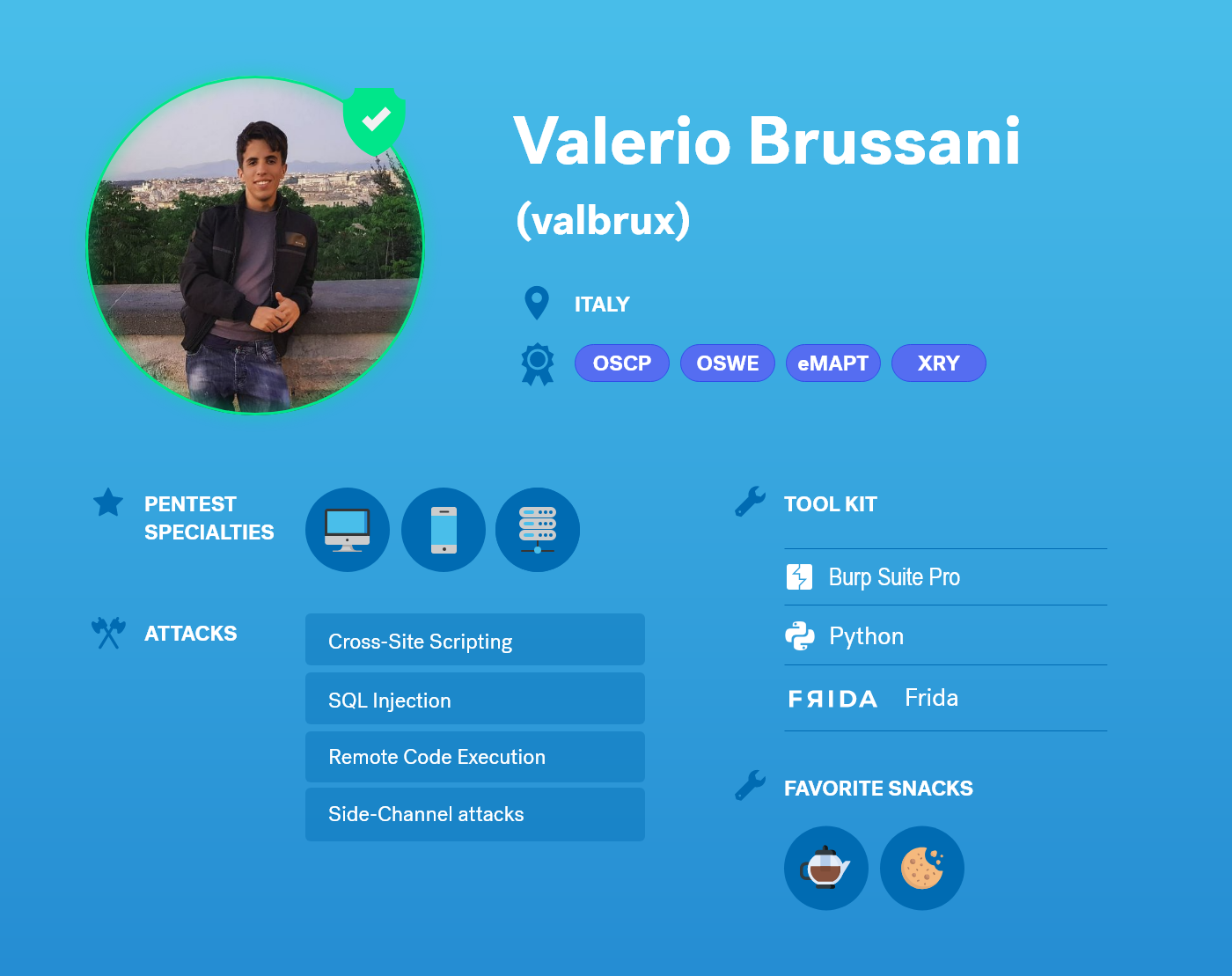
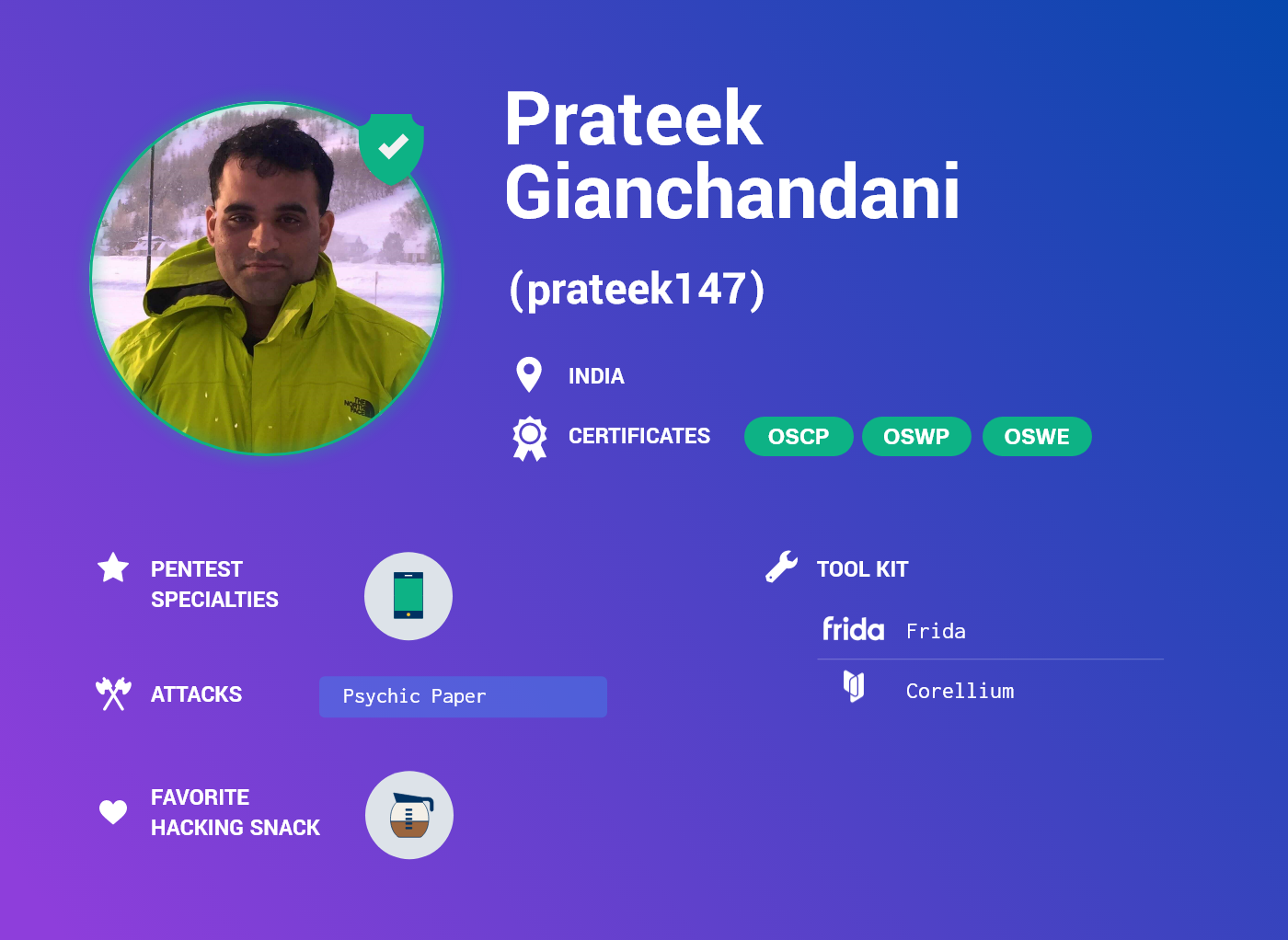
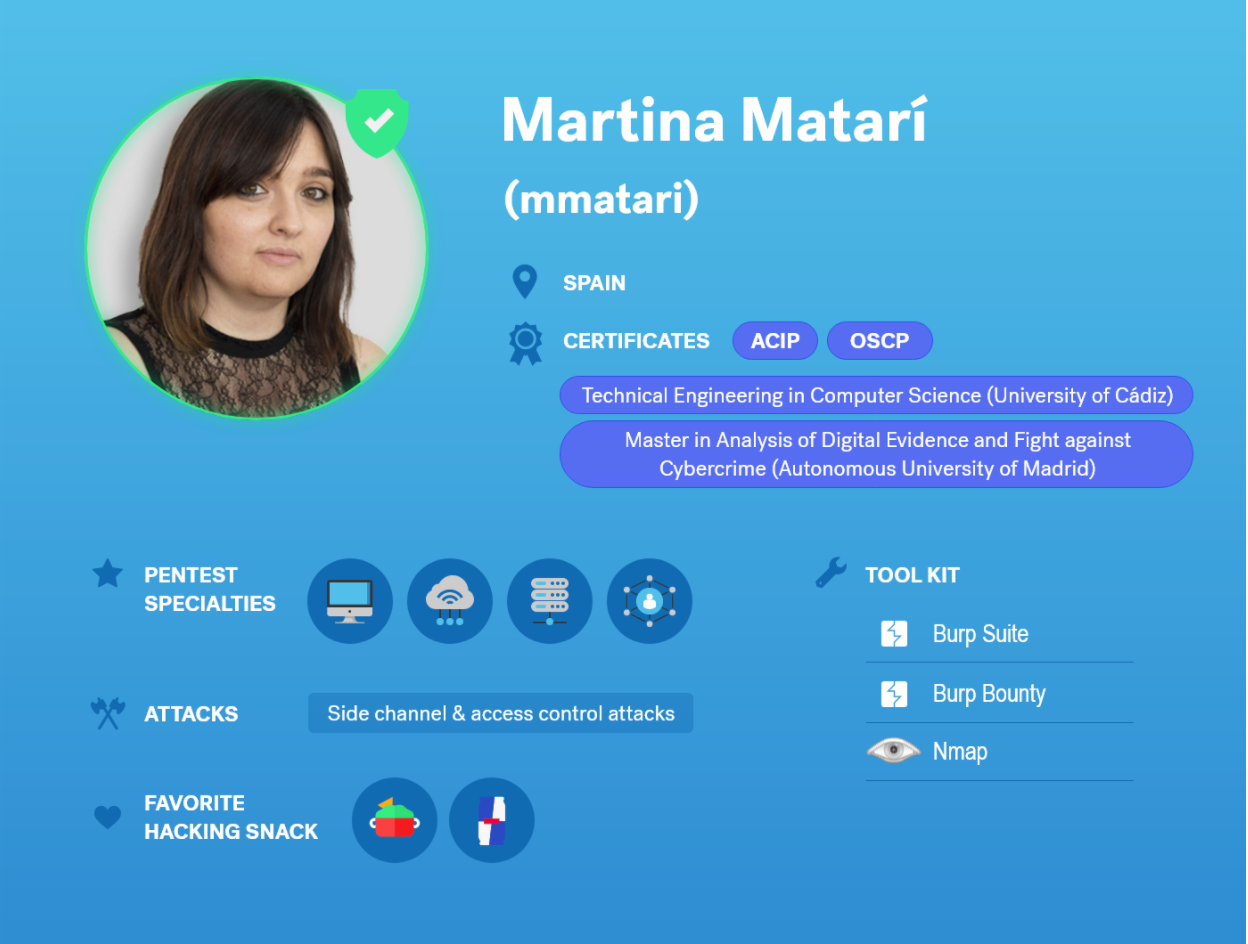
Alex Moraga has been a part of the Cobalt Core since 2015. Over the course of his seasoned pentesting path, he has built a reputation of being a distinguished lead, exhibiting both highly technical prowess as well as constructive communication. Alex is one of the 270+ pentester worldwide who has helped Cobalt secure over 2000 assets. We sat down with him to learn more about his transition into full-time freelancing, his learnings as a longtime Core pentester, and explore why he enjoys working at Cobalt.
Pentester Origin Story: How did you first get involved in pentesting?
AM: I would say that it started when I first became interested in learning how networks functioned— during a time before the term pentesting was really used yet. Between 1994 and 1996, I discovered Internet Relay Chat (IRC), which was an early form of chatting with other people through a client/server networking model. This resource introduced me to attacks like 0day, Ping of Death (a peer to peer modem connection), and System Port Opens, that would lead me on a path now known as pentesting.
My past work experience came from the IT corporate side, where I was involved in deployments and was a server/network administrator for some of the top five banking environments in the world. In these kinds of environments, access control and norm following were very strict and restricted which provided me with a good knowledge base of secure environments that have contributed greatly to my current career path. While at Cobalt, I have been part of various pentest projects associated with web, mobile, host (networking), and desktop applications— all of these pentest engagements have given me new challenges and learning experiences.
How did you move into a full-time freelance career? What do you love about that kind of work style?
AM: After working in a corporate IT engineering environment for some time, I started to realize that this kind of work environment was not a good fit for me. Although I gained a lot of insight during this time, I was not spending my time on what I loved most. That’s when I decided to shift my professional career path that would allow me to focus on fields that aligned with my passion for information technology and ethical hacking.
In the beginning, this career path shift was not easy to achieve because there were almost no companies that provided ethical hacking services in Chile at the time. This field was still very new here, so I decided to test my skill and learnings. At that point, I already had an OSCP certificate, but I wanted to test my skills in the bug bounty arena. It was around that time when I resigned from my position as a Security Engineer to fully focus on freelance ethical hacking. After finding some interesting vulnerabilities on public programs, I began to receive invitations to join private bounties, until one day I received an invitation from one of the Cobalt founders to be part of the great Cobalt Core team in the early days. Since then, I have been pentesting with Cobalt.
Making this transition gave me the opportunity to learn new techniques and work on different projects—all in a work style that I love. I enjoy the flexibility in my schedule and ability to work on a variety of different projects. For me, managing my time is something priceless and when given the freedom to manage my schedule this opens up my ability to be fully creative.
What advice would you offer pentesters for managing their time and avoiding burnout during a pentest?
AM: It is good to get away from your screen from time-to-time. This gives you the chance to analyze the target in a different way, think through other approaches, and learn more about the vulnerability so you can return back with a fresh perspective.
You’ve been with Cobalt since 2015 with this unique perspective, what is it about the Core that you find continually gratifying over these years? How have you seen the community evolve - what interesting developments have you witnessed since you first started?
AM: Over the years, I’ve been fortunate to see the continuous development of the Cobalt platform and communication channels. It’s been amazing to see new technology integrations, increased customer-pentester communications, and the growth of the organization as a whole. The way the platform itself has been developing and improving is significant since the beginning. There are various new features, processes, and resources within the platform that simply did not exist back then in 2015. The Cobalt team really listens to us and wants to make our lives easier by creating processes that allow us to focus on what we love most: pentesting.
Another element that has been great to see is that the amount of quality pentesters joining the community continues to grow. This allows me to expand my network and knowledge, to be able to learn with and from so many amazing offensive security professionals.
In general, to see this kind of growth and connection year-after-year is inspiring and makes me proud to be a part of this team.
What motivates you when it comes to pentesting?
AM: I love learning about new technologies and understanding how applications work. To me, it’s motivating to see what I can find, gain an understanding, and then test it out. I love having a space to learn and an environment to interact with new and talented individuals.
What do you feel makes a good pentest engagement?
AM: Good engagement requires a good understanding of the scope and goals a customer has for a pentest. This makes communication extremely important. Ensuring that pentesters have the necessary access and giving them the tools and resources to understand functionality.
What kind of targets excite you the most? Do you have a favorite vulnerability type?
AM: For me, web, networks, and mobile devices are definitely some of the most interesting and exciting targets to play with. One of my favorite vulnerabilities is when a direct interaction with the hosting node is achieved, so I would say Remote Code Execution (RCE) is always challenging and satisfying to find and report.
Where do you go to learn about different security concepts? Are there certain pages/handles you follow?
AM: Twitter and Medium are two of the sources that I use the most to stay updated with the latest attacks, bypasses, and techniques. Also, keeping an eye on the publicly available reports from other researchers helps to add other approaches to potential targets and trending issues to your wheelhouse.
How do you conduct research and recon for a pentest?
AM: The first step for me is to check the target function and gather as much information on it as I can. This includes looking into details on the backend, services, servers, potential error messages with internal information, banners with detailed versions. As well as conducting OSINT and researching the target. For example, sometimes you find a deprecated endpoint still available on the target domain, in case of web applications, try forced browsing. In mobile applications try to reverse the package, and check what the application does in the device file system and their logs.
Do you leverage any tools? What are your go-to tools?
AM: I can not imagine performing a web or mobile application pentest without the help of a proxy— this helps a pentester view and tamper the interaction between the client and server. Burp Suite is the main source in these cases. I also use SQLMap to help me exploit SQL injections, nmap, fuff, Metasploit, Bash scripting, and testssl.sh. For mobile testing, I like to use Frida, and for OSINT I will use Google, Censys, or Shodan.
What advice would you offer to someone who is interested in getting into pentesting? What do you wish you would have known before you started?
AM: The first piece of advice would be to learn the basics of how an operating system works. This base of understanding opens the door for continuously learning new concepts and furthers your growth as a pentester. I would also recommend familiarizing yourself with the use of the Shell Command prompts to gain a good understanding of how the web application and API works on the backend side. Learning how an application is deployed and learning a little scripting and coding will always be a plus. Last but not least, having knowledge about networking will be very helpful in network pentest scenarios. Understanding these network scenarios will provide a solid foundation in pentesting to help pivot internally between different internal networks or segments, bind reverse shells via different tunneling types, or retrieve target data via Out-of-Band (OOB) exploitation.
What do you wish every company/customer knew before starting a pentest?
AM: A good definition of the target provides the pentesters with a clear understanding of what to look for and what to avoid during the pentest process. By providing endpoint documentation (Swagger or Postman), role credentials, and examples will help save pentesters valuable time and will likely yield better results. When pentesters are provided with these resources, they are able to plan out their project and schedule their time effectively— ensuring enough time is dedicated to what matters the most. Rather than them dedicate time on gathering information on something that may slow them down and not take precedence.
As an experienced Pentest Lead at Cobalt, what would you say to Core pentesters that are interested in being a Lead?
AM: Being a Pentest Lead at Cobalt is more than just finding interesting bugs and properly reporting them. It’s about collaboration and ensuring that your team is working together effectively to provide the best possible engagement for the customer. As a Lead, keep an eye on the updates and reported findings. Always be aware of what’s going on in the Slack channel, empathize with the customer and their environment, provide feedback, and let the pentesters enjoy what they are doing (give them guidance when needed but don’t micromanage)– these are a few of the most key parts of being a great Lead.
What do you like to do outside of hacking?
AM: When I am not hacking, I like to take time with my friends, listen to music, travel to the hills, and enjoy sunsets at the beach whenever possible. Being active is important to my routine so I workout at the gym regularly, and lately, I have been bicycling outside or on a home trainer. Before the pandemic, I would surf, but that is currently being replaced with street longboarding– it is a nice alternative because now my puppy can join me while I ride. I also enjoy taking pictures because it allows me to engage my creative side, eating good food, and learning new skills whenever I can. In the future, I would like to visit some places such as Spain and Italy.
What are your short term and long term goals?
AM: In the short term, I would like to find some time to take another Offensive Security certificate, like OSEP and OSWP. In the long term, I am planning to build my own home, and professionally, I want to expand my pentest skills– reverse engineering is an area that I’m interested in diving deeper into.