Managing cybersecurity can be complex, but it doesn’t have to be. Pentesting has changed over the last decade to keep up with emerging trends in the cybersecurity space, prompting important questions like: how exactly has the pentesting market evolved over the past 5-10 years? What’s on the market now? What would be the right fit for my security program?
Our experts did the research, so you can stay informed and choose the best pentesting solution with confidence. The Buyer’s Guide to Modern Pentesting has the information you need to make finding, fixing, and preventing vulnerabilities with pentesting simple, so the groundwork is well-established for your business to run a productive pentest.
The Focus: Modern Pentesting
The focus of the guide is on modern pentesting, but pentesting can look different depending on the vendor you choose. It’s important to know what’s available, what to consider when purchasing, and the pros and cons of each option. The Buyer’s Guide provides a detailed overview and comparison of Crowdsourced Software Security Testing Platforms (CSSTPs), consultancies, and PtaaS vendors. It’s a one-stop resource on how these vendors stack up against each other.
The Buyer’s Guide thoroughly explores each vendor type, laying out all of the information you need to make an informed purchase without feeling overwhelmed. It breaks down the pentest cycle into 3 components: Discover & Plan, Test & Remediate, and Report & Analyze to show what should happen as a baseline for each stage, and see what the three vendor groups bring to the table.
For example, the Discover & Plan phase involves mapping out the attack surface and defining the upcoming scope. Take a sneak peek into what that vendor comparison looks like:
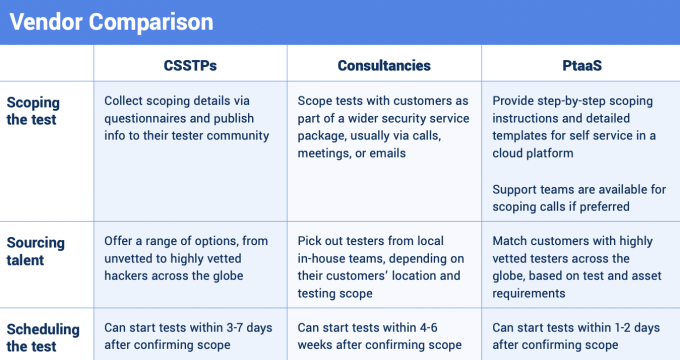
The full text provides an in-depth comparison of CSSTPs, consultancies, and PtaaS vendors — not just their features, but also their ROI and possible impact on your security program. For everything you need to know and do to bolster security with the right pentest solution, read The Buyer’s Guide to Modern Pentesting.










