A threat model is a structured process of identifying and mitigating threats. Ideally, threat modeling should be performed during the design phase since this is where you have the most flexibility to make changes that can eliminate threats. Threat modeling can be performed for any application, network, or Internet of Things (IoT) device.
When Should Threat Modeling Be Done?
Threat modeling can be done during different phases of the project. The best time to perform threat modeling is at the end of the planning phase of a new project because it can help find potential vulnerabilities before development even starts. This can potentially save companies a lot of money especially if there is hardware involved.
The other time that threat modeling is recommended is when a new feature has been added to the project. As new product features launch, it’s best practice to update the thread model to ensure no new vulnerabilities are introduced.
Who Should Complete the Threat Modeling Process?
Threat modeling can be performed by a security professional or by the development team creating the software. It can be performed during the development life cycle after the development team receives training on it. However, having a security professional complete the model is oftentimes ideal, especially if a threat model has never been performed before.
Threat Modeling Advantages
Threat modeling can save companies money in the long run because they find potential vulnerabilities early on in the development life cycle.
With the advantages of threat modeling in mind, let’s review a common framework used to create threat models known as STRIDE.
What is STRIDE?
There are several frameworks used for threat modeling but the STRIDE framework is the most popular one. STRIDE is a mnemonic for security threats in six categories.
- Spoofing (Authenticity)
- Tampering (Integrity)
- Repudiation (Non-repudiability)
- Information Disclosure (Confidentiality)
- Denial of Service (Availability)
- Elevation of Privilege (Authorization)
During a spoofing attack, a person or program successfully pretends to be someone else. A person, file, machine, and process can be spoofed.
During a tampering attack, a file, network package, or data is successfully modified by an attacker.
A repudiation attack is claiming you didn’t do something or attacking the logging system.
During an information disclosure attack, an unauthorized person has access to information that they shouldn’t.
During a denial of service attack, resources are absorbed and services can become unavailable. The resources that can be absorbed can be RAM, disk space, CPU, and network resources.
During an elevation of privilege attack, an unauthorized person can perform actions they are not authorized to do. Elevation of privileges usually involves bypassing authorization checks or corrupting a process.
Threat Modeling Process
The first step when performing threat modeling is to create a Data Flow Diagram (DFD). You can start diagramming your project on a piece of paper first to get an idea of what you need to include. After that is complete, you can use a tool, such as the OWASP Threat Dragon (Free multi-platform modeling tool), to create a diagram. Depending on what software you are using, diagram components might look a little different than below.
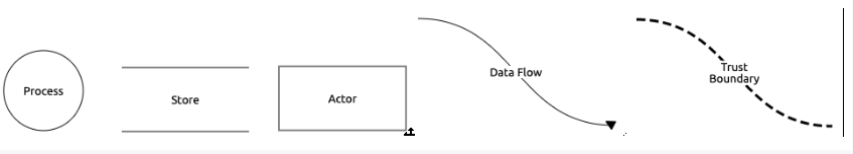
There are five main diagram elements that are used in threat modeling: process, data store, external entity, data flow, and trust boundary.
|
Element |
Definition |
Examples |
|---|---|---|
|
Process |
Transforms incoming data flow into outgoing data flow |
Code |
|
Data Store |
Repositories of data |
Databases, files and logs |
|
External Entity (Actor) |
Objects outside the system that the system communicates with |
People or code outside of your control |
|
Data Flow |
Flow of information |
Communication between processes or data stores |
|
Trust Boundary |
A change of trust levels |
Internet |
After you complete your DFD, you can start threat modeling your project. Use the chart below to perform STRIDE per element.
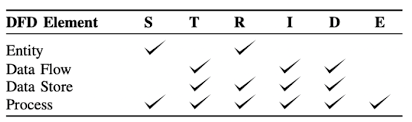
For every external entity, verify that there are not any spoofing or repudiation threats. For every data flow, verify that there are not any tampering, information disclosure or denial of service threats. For every data store, verify that there is not any tampering, repudiation, information disclosure or denial of service. For every process, verify that there is not any spoofing, tampering, repudiation, information disclosure, denial of service or elevation of privilege threats.
Once you have completed the threat model, share it with your team to verify its accuracy.
If you are just getting started with threat modeling or teaching others, check out this ShoStack game designed to make threat modeling into a fun interactive game.
Explore this topic more with the role of threat modeling in penetration testing.










