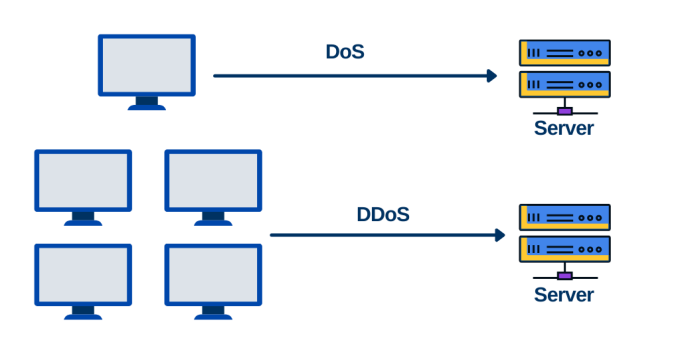
A Denial of Service (DoS) attack takes place when an attacker disables access for legitimate users or members of an organization to operate devices, information systems, network resources, etc with a single computer to launch the cyberattack. This can happen in two ways: by flooding or by crashing a system.
The main goal of a DoS attack is to overwhelm the capacity of a machine, causing denial-of-service to additional requests. So how can you tell when a computer is experiencing a DoS attack? There are a few key indicators, such as unusually slow network performance, inability to load a website, and abrupt loss of connectivity.
DoS attacks come in a variety of types with different motivations. A few common examples are:
- Extortion of money
- Targeting websites of opposing ideology
- Cyber warfare
- Business competition
High-profile corporations such as banks and government organizations are at the highest risk of enduring a DoS attack, although it’s important companies of all sizes and sectors remain vigilant and prepared to avoid losing money and resources to attackers. Here’s a look into the types of DoS attacks and methods for prevention:
Types of DoS Attacks
DoS attacks can typically be put into two main categories: buffer overflow attacks and flood attacks. In a buffer overflow attack, all available hard disk space, memory, or CPU time is consumed by a machine that leads to system-related crashes and denial-of-service. With flood attacks, the targeted server is oversaturated until denial-of-service occurs.
The three main types of DoS attacks include:
1. Application-Layer Flood
With this method, attackers flood services in an attempt to slow down and crash the targeted device. This type of attack can look like millions of requests per second from illegitimate/spoofed email addresses.
2. Distributed Denial of Service Attacks (DDoS)
DDoS attacks are similar to DoS attacks, except requests are sent from multiple sources rather than just one. DDoS attacks often include the use of a botnet or “zombie” machines — machines that have been compromised and are controlled by attackers.
3. Unintended Denial of Service Attacks
Like the name insinuates, unintended DoS attacks are unintentional. If a website (such as a news source) attracts a large volume of visitors, the request can become overburdened and slow or crash the site.
Of these types of attacks, DDoS attacks are quickly becoming the most prevalent at a quicker, higher volume.
Common DDOS Attacks
A Distributed Denial of Service (DDoS) Attack involves multiple machines working together to attack a target, often with infected machines controlled by malware. While there are many different types of DDoS attacks, there are a few that are most commonly experienced:
Smurf Attacks are a type of distributed Denial of Service (DDoS) attack where attackers exploit vulnerabilities of the Internet Protocol (IP) and Internet Control Message Protocols (ICMP).
SYN Flood Attacks aim to consume all available server resources by sending repeated SYN requests to overwhelm and “flood” the targeted server.
Plashing involves a series of fake updates sent to a piece of hardware that permanently damages the system.
IoT Botnet attacks continue to grow in frequency when attackers breach internet connected devices such as refrigerators or other appliances to execute an attack.
Categories of DDoS Attacks
Websocket DDoS is another form of DDoS attack. Websockets make communication between a client and a server more simple. That said, allowing an unlimited number of connections to reach the server gives attackers an open window to flood the server with a DoS attack. Websocket DDoS greatly exhausts the server, leaving the website slow and inefficient.
Together, DoS and DDoS attacks can be categorized into three types:
1. Volume-Based Attacks occur through flooding hubs with ICMP requests. The entire bandwidth is consumed in a volume-based attack disabling authorized clients from accessing the target network.
2. Protocol Attacks consume the actual server resources such as firewalls and load balancers.
3. Application Layer Attacks target Apache, Windows, OpenBSD vulnerabilities, and more with the goal in mind to crash the webserver.
DoS Attack Prevention Methods
When experiencing an attack, the Cybersecurity & Infrastructure Security Agency (CISA) says, “do not lose sight of the other hosts, assets, or services residing on your network. Many attackers conduct DoS or DDoS attacks to deflect attention away from their intended target and use the opportunity to conduct secondary attacks on other services within your network.”
Here are a few recommendations for preventing DoS and DDoS attacks:
- Limit or shut off broadcast forwarding where possible
- Set up firewalls
- Eliminate and patch known vulnerabilities
- Monitor network inbound traffic
At the end of the day, adding a Pentest as a Service (PtaaS) platform into your security program can identify the key vulnerabilities needed to help prevent cyber threats. Learn more about how Cobalt delivers the real-time insights agile teams need to remediate risk quickly and innovate securely.
Explore more on this topic with an overview of the Largest DDoS attack ever.










