In the modern world, cybersecurity or lack thereof impacts almost every industry.
Recent attacks on Colonial Pipeline, JBS Meat Processing, Martha’s Vineyard, and many others show how prevalent these attacks are to modern society. With these disruptive trends increasing, companies seeking to avoid the next big cyberattack need to deploy security components directly within their development process.
Recently, the White House released new cybersecurity guidelines encouraging companies to proactively secure their digital infrastructure. These troublesome ransomware attacks may have a silver lining by accelerating the transition from a traditional security approach to the DevSecOps engineering process.
With this in mind, let’s take a closer look at DevSecOps and how this development process empowers a higher level of security.
Defining DevSecOps
DevSecOps bridges the gap between development, security, and operations. The goal of this development method is to align the different interests across these departments and create a more cohesive development cycle proactively accounting for security. This explains the emphasis on the DevSecOps methodology which many within the world of development refer to as a best practice today.
IBM defines this new methodology as, “DevSecOps automates the integration of security at every phase of the software development lifecycle, from initial design through integration, testing, deployment, and software delivery.”
What is DevSecOps methodology?
With more cyberattacks than ever before, the trend of prioritizing security is just beginning. With this in mind, teams operating under a DevOps framework should consider the new iteration with DevSecOps which includes security. With an end goal of increasing a company’s security posture, a DevSecOps methodology offers this as a solution.
Why is a DevSecOps model Important?
Since development cycles under a DevSecOps model include security aspects before deployment, this methodology offers a more proactive approach to security. As opposed to bolting security onto applications as an add-on after deployment, DevSecOps allows companies to integrate security best practices within the development lifecycle.
There are many reasons why companies should care about DevSecOps. For example, imagine a situation where an attacker gains access to an application before the deployment. Then the attacker implements an exploit included in the application as it goes out to thousands of customers. This worst-case scenario becomes far less likely to occur when operating under a framework that promotes security to remain top of mind.
Now let’s take a closer look at how different tactics support businesses operating within a DevSecOps methodology.
Best Practices Implementing
DevSecOps
1. Automate
With modern development, companies should always be mindful of what tasks they can automate versus ones that require a manual touch.
Automation empowers companies to operate at a faster velocity while still adhering to security best practices. The important part here is for a well-versed security professional and developer to collaborate together to determine which processes merit automation.
Remember, automation applies to both tools and processes since each offers unique security benefits and drawbacks. For example, a security scanning tool offers a reliable quick view of security metrics. On the other hand, pentesting requires a manual tester to review the many aspects a scanning tool simply can’t comprehend.
2. Threat Modeling
Another important aspect to DevSecOps comes with threat modeling. With a threat model, businesses gain a better understanding of their security posture. This understanding leads to insights into the company’s ability to identify vulnerabilities, understand their potential impact on businesses, and therefore begin to prioritize different vulnerabilities based upon their severity and potential impact.
A strong DevSecOps program will incorporate the threat modeling processes directly within engineer's workflows. Through this process, code will become more secure and vulnerabilities discovered faster. Furthermore, the combined input across security and engineering teams helps encourage more cohesion.
3. Culture: Code with Security in Mind
With security as a holistic practice, one where the weakest link in the chain can lead to an exploit occurring, it’s vital to encourage development teams to code with security in mind.
At the essence of DevSecOps, collaboration across different departments fosters the end goal of this methodology to improve a company’s security posture. To this point, companies should encourage a security-minded culture. When developers and other employees consider security throughout their day-to-day work, it improves the company's ability to operate with a higher level of security.
To make this occur, companies deploy a variety of tactics such as regular security briefings for teams. Another great example comes from companies who encourage their staff to direct security concerns to an internal expert before any concerns become actual issues. Lastly, companies requiring staff to implement security best practices such as 2-factor authentication are easy wins to implement here.
4. Leverage Security Tools
With a plethora of DevSecOps security tools available, companies should have no lack of resources available to assist in deploying a DevSecOps methodology within their development process. Testing tools empower a more effective process for both security and engineering teams.
Presenting security tools to an engineering team encourages security to be incorporated directly into the development process. The underlining awareness to include security as a core component during the engineering process will inevitably help improve security. Also, there's an abundance of tools available to support engineering teams focused on developing securely as presented by the DevSecOps methodology.
5. Be Proactive & Start Early
Last but certainly not least, companies should proactively start their security programs early!
Proactively approaching security embodies the essence of DevSecOps. Through a proactive approach, such as proper planning and incorporating known vulnerabilities within engineering workflows allows for a faster remediation process and thus, more secure code.
Strong DevSecOps programs not only emphasize security but also plan time for security reviews and time for engineering remediation. With these two teams planning in tandem, security improves faster.
Furthermore, the collaborative nature generates points of synergy between the teams empowering both to take into account their counterpart's perspective and create code more securely.
What is the Difference Between DevOps and DevSecOps?
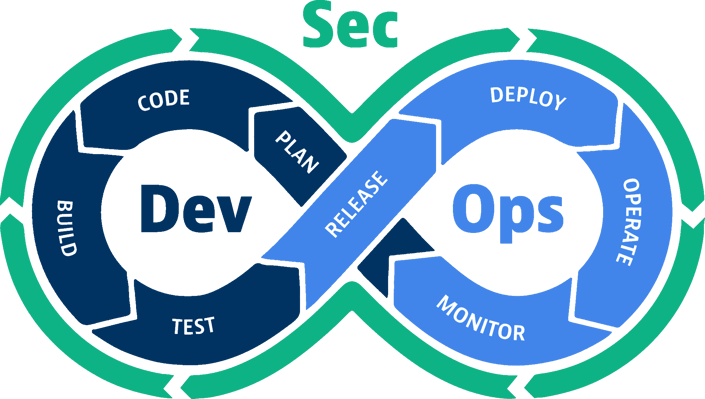
DevSecOps integrates security directly into the development lifecycle with the goal of promoting a stronger security posture.
With a DevSecOps approach, companies will increase collaboration across different disciplines and departments including operations, development, and security. Two factors here will benefit companies using a DevSecOps model including: the increased emphasis on security and distribution of the responsibility to ensure security. Both of which will help increase the security program's effectiveness at a business.
Read more about the differences between DevOps and DevSecOps.
In closing, remember that security generates the best business results when proactively implemented instead of reactively added onto an application. For companies interested in expanding their security posture, learn more about Cobalt’s offering of an innovative approach to pentesting with a Pentest as a Service (PtaaS) platform.










