This blog post is part of an ongoing series in which members of the Cobalt product team provide deep dives into specific platform features.
Most organizations that have undergone a pentest understand that the actual test is just the beginning. The real work begins the moment you receive your pentest report with the list of vulnerabilities and posed risks, and a concluding report along with information on the testing methodology and remediation recommendations.
With Cobalt’s PtaaS platform, reporting is an interactive and ongoing process. Individual findings and recommended fixes are posted on the platform in real time, so your team can take immediate action. And in some cases, that can mean marking their associated risk as “accepted”.
What does accepted risk mean and why is explaining it important?
Today, security teams accept the risk of some findings for a variety of reasons. Their severity may not meet the internal risk threshold for remediation, or there might be upcoming security controls that address the. Unfortunately, the reason for accepting certain risks often resides in an organization's internal documentation and is not captured as part of the findings report. When reports are shared with their customers or stakeholders, the reason for accepting risk is either lost or must be explained separately.
With the Cobalt platform, you can now not only identify and mark vulnerabilities that have no measurable impact to your security posture, but also explain why the risk was defined as acceptable. This additional contextis captured in the final pentest report that can be shared with stakeholders including customers and auditors, so they can determine the security posture of your organization’s assets accordingly.
How it works
Once you have initiated a pentest on Cobalt’s platform and vulnerabilities are discovered, they become available for you and your team to review and analyze. If you decide that certain findings are not a true risk to your assets, you can change their state to “Accepted Risk.”
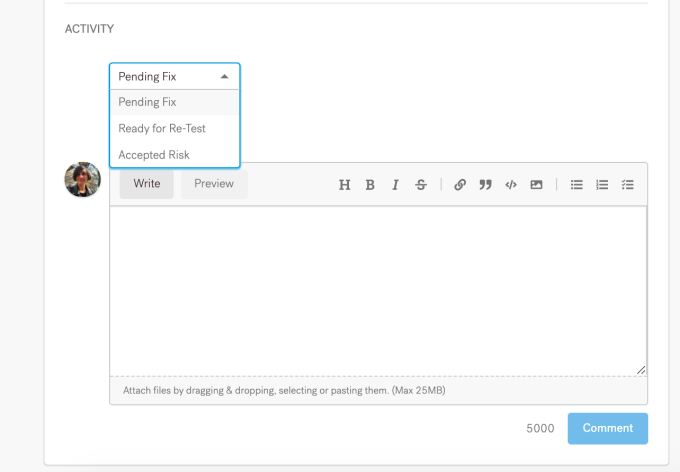
Once you click on “Accepted Risk,” a new modal opens.
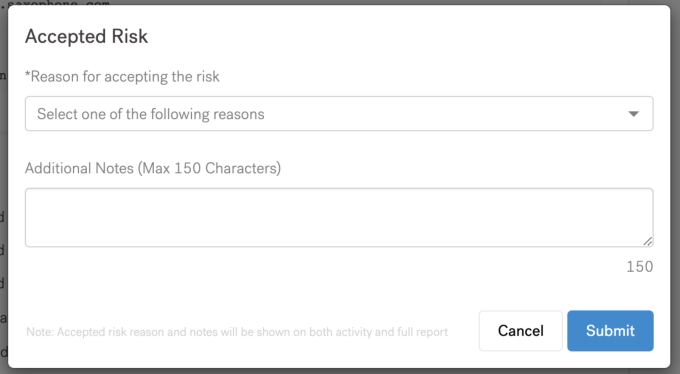
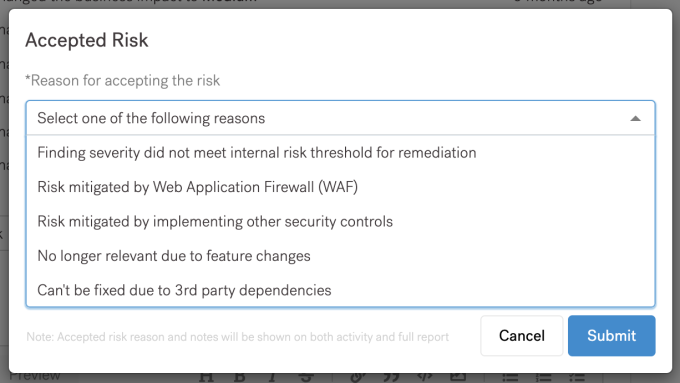
From here, you can select a reason for accepting the risk. If you don’t see a matching reason applicable to your organization, you can select “Other” from the drop-down list and enter additional information in the notes section.
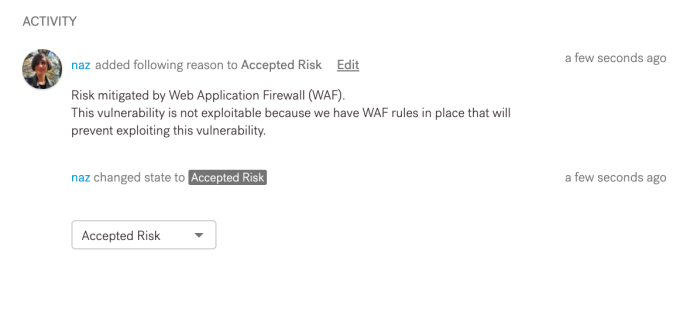
Once you click “Submit,” this information will be recorded in the platform and will be visible in the findings comments section for all users who have appropriate access. Additionally, this event will be recorded on the platform and collaborators from your organization will be notified within the platform, as well as through email. All users with access to the pentest and the associated findings will be able to see who has accepted the risk, when it was accepted, and why.
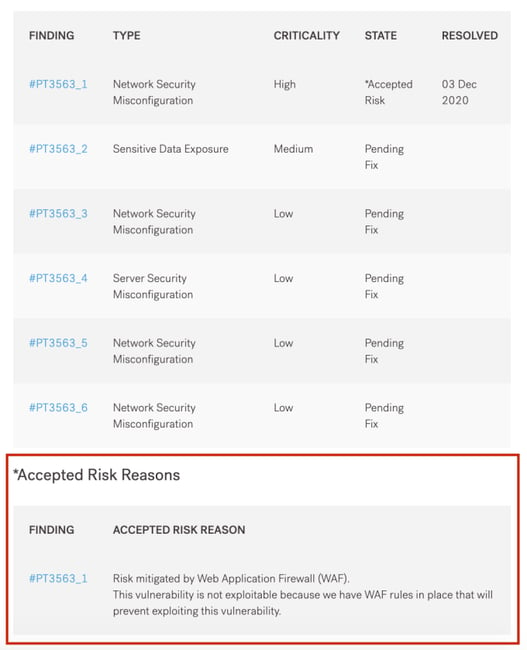
All of this information is also included in your final pentest report. The Post-Test Remediation table provides a summary of all findings from the pentest, along with their latest status. If the status is “Accepted Risk” ,there is a supplemental table below the remediation table that presents the accepted risk reason and additional notes. This will help organizations convey contextual information to their most important stakeholders such as customers, prospects and auditors without needing supplemental information or having to verbally explain it.
As we continue to be a leader in PtaaS, we are always looking for ways to ensure Cobalt is the most innovative solution for DevOps-driven software companies that want to implement security across the development lifecycle and optimize application security processes.
Curious to learn more? Schedule some time with one of our security experts to see Cobalt in action!