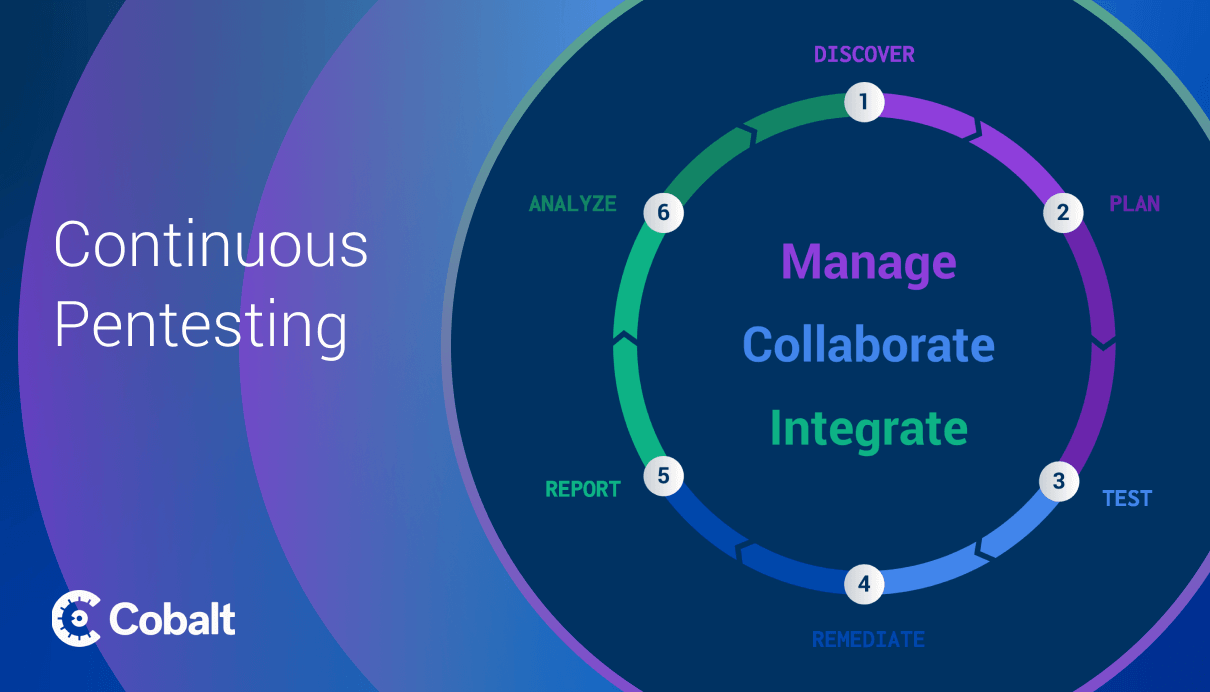
Pentesting requires companies to do more than simply receive a report at the end of the test.
The true value derived from a pentest is through the remediation of discovered vulnerabilities. Without taking action from your pentest results, there’s a missed opportunity to capture the full value from pentesting. It’s vital for standard pentest results interpretation to include a remediation plan.
With a proper remediation plan in place, companies benefit two-fold while utilizing a Pentest as a Service (PTaaS) platform. The first benefit comes from the collaborative nature of the platform, which empowers developers and security testers to connect directly for knowledge sharing.
Furthermore, a proper remediation plan prioritizes a faster vulnerability fix time. Thus, creating a smaller window for attackers to exploit vulnerabilities.
With this in mind, let’s take a closer look at the end goal of a pentest and how companies best use pentest reports and results to improve their security posture.
What is the End Result of a Pentest?
When starting anything, it’s important to keep the end goal in mind. This helps define the necessary steps to reach the goal, while also minimizing distractions that could jeopardize success. Stephen Covey encapsulates this message best by saying:
“Begin with the End in Mind means to begin each day, task, or project with a clear vision of your desired direction and destination, and then continue by flexing your proactive muscles to make things happen.” - Stephen Covey
Thinking about the end goal of a pentest, companies should prioritize their plan to utilize insights discovered during the test to guide remediation plans. With this, developers will be delighted with the option to communicate directly with security testers to clarify vulnerabilities discovered and ensure they’re properly remediated.
To this point, let’s take a closer look at what’s included in the pentest report and how businesses can best utilize this information to process their pentest results.
Pentest Report
At Cobalt, we offer customers a variety of different reports to cater to different stakeholders: auditors, customers, management, and more. Further, customers can customize their pentest reports to include more specific information.
After an executive summary, the pentest report will include a scope of work and methodology statement highlighting the process undertaken during the test. Next, for each vulnerability identified, the pentest report will include two important categories to assist with the remediation prioritization process: vulnerability risk and criticality.
Lastly, and most importantly, the report will identify post-test remediation tasks such as retesting — which on Cobalt’s PTaaS platform comes complimentary after every pentest.
Through the pentest report, companies will be empowered to better understand where their security risks occur. With this understanding, the benefits created are two-fold to complete the pentest process with the actual end results.
Let’s take a closer look to understand what benefits pentest results offer companies.
Pentest Results to Improve a Security Program
After you’ve received the pentest report, it’s time to process the results. This will include identifying granular details that should be included in each of the custom reports you need for various stakeholders.
The pentest results will fuel the remediation prioritization process. Remember, it’s more important to remediate vulnerabilities found during the pentest rather than simply receive the report by itself. Pentest remediation shouldn’t be overlooked.
To this point,companies using a PTaaS platform will be able to connect developers directly with the security testers to clarify discovered vulnerabilities and apply a proper fix for remediation. This benefits companies with a more secure remediation process. It also helps encourage security teams to learn more about security vulnerabilities and thus, apply these fixes in their day to day work going forward.
The report should be used as a foundational guide for remediation. Companies that get the most value from pentesting will prioritize remediation and benefit from the final value proposition from a successful pentest.
Finally, companies will also gain an improved security posture through the remediation process. This is often the largest value proposition for companies proactively approaching security with pentesting, as it decreases the window of time an attacker can exploit the vulnerabilities.
In closing, remember that the real value of a pentest is not to check complete in a compliance box, but to improve the security posture of your digital assets. To this point, companies should plan to prioritize remediation of identified vulnerabilities after their pentest.
Thankfully, when pentesting through Cobalt’s PTaaS platform companies can enjoy complimentary retesting of their assets after remediation. This value add helps ensure businesses have properly remediated their identified vulnerabilities and helps bridge the gap between security and engineering departments.