From Pwned to Zero-Day: 20 Hacker Lingo Terms Every Tech Enthusiast Should Know
To the uninitiated, eavesdropping on a conversation between security researchers or underground hackers feels like listening to a ...






Make sure your IoT devices, laptops, and VDI environment have secure configurations and sufficient hardening. The more secure your devices, the less opportunities hackers have to do damage.

Lock down unnecessary services, ports, and system privileges in connected devices to prevent breaches and increase resilience against attacks.
Assess your organization's security across all your cloud services, including Azure, GCP, and AWS. Identify vulnerabilities and weaknesses and validate security controls to optimize your defenses.
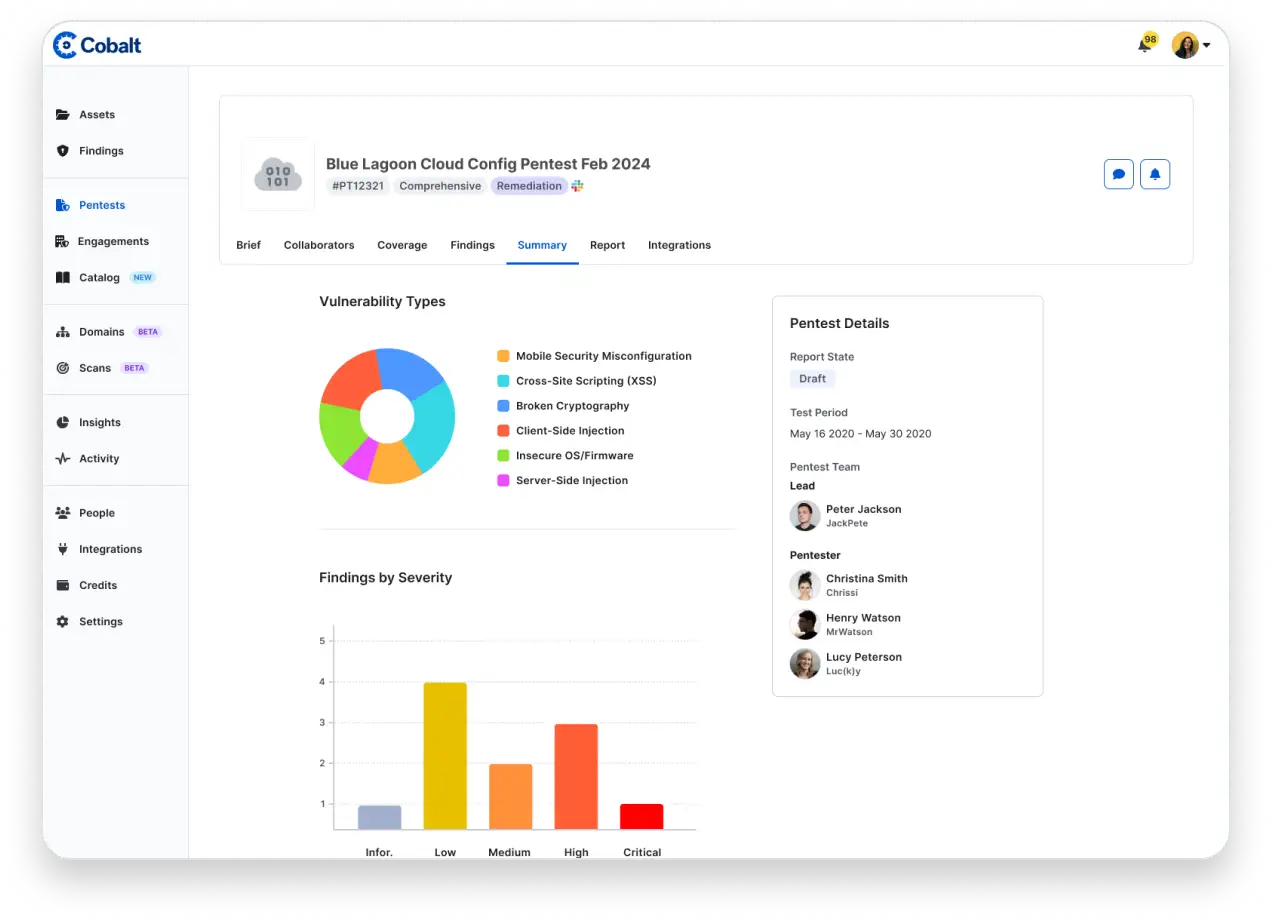

"Being able to interact with findings in the platform and discuss them through Slack makes for a much more efficient process. We’ve been able to get into it and engage with the findings there, which is a big improvement on the old process."
To the uninitiated, eavesdropping on a conversation between security researchers or underground hackers feels like listening to a ...
Empower your security and development teams with Cobalt’s unique combination of a modern SaaS platform and our community of vetted experts. Trust the pioneers of PtaaS as your offensive security partner across your entire attack surface.
